|
.Super Cool Investigative information for a Malware type investigations. This is one of the way modern malware maintains persistence in the system across shutdowns and reboots.
Step -1
sudo mkdir /Volumes/apfs_disk_image/ Step -2 sudo mkdir /Volumes/apfs_disk_mount/ Step -3 sudo xmount --in ewf --out dmg /Users/<Username>/APFS/apfs_disk.E01 /Volumes/apfs_disk_image/ Step-4 hdiutil attach -nomount /Volumen/apfs_disk_image/apfs_disk.dmg Step-5 diskutil ap list Step -6 (Optional)In case of encryption use this: diskutil ap unlockVolume <Disk Guid> -nomount Step-7 sudo mount_apfs -o rdonly,noexec,noowners /dev/disk#/Volumes/apfs_disk_mount/ Install.log file has an immense value to see all the installations on you Mac. Use this command on your terminal to get the list: grep 'Installed' /private/var/log/install.log This log file has an immense forensic value to identify the user installation activity. Questions like remotely installed applications, failed installation can be answered by analyzing the 'Install.log' file. cat /private/var/log/install.log MacOs Key Chain Analysis
Location: ~Library/Keychains File of interest: keychain-2.db Data in Login & System Keychain can be very useful in an investigation. Once you copy the keychain-db file - you can use keychain native app to view the content. $ cd /Users/<Username>/Library/Preferences
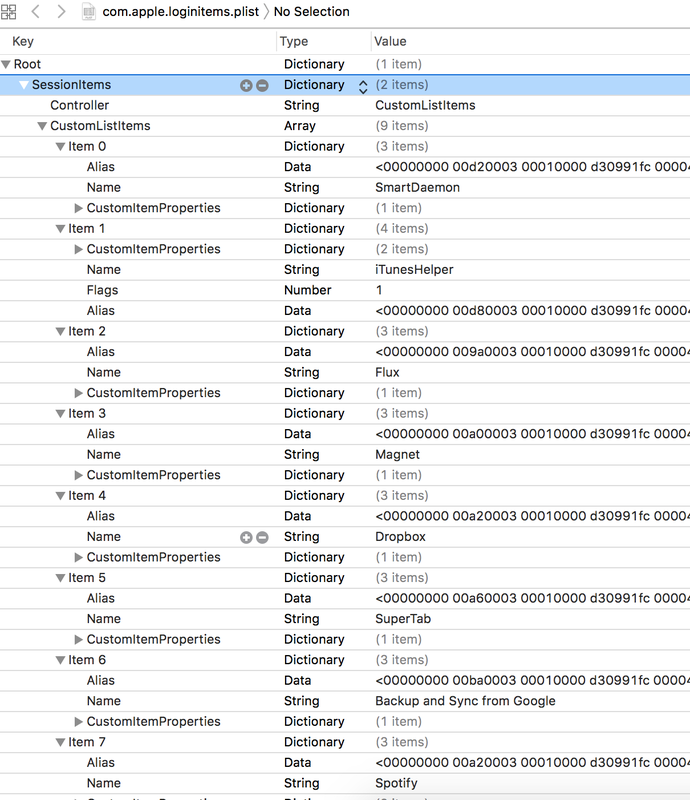
$ open -a xcode com.apple.loginitems.plist You can use any hex editor to read the hex data. Hex will give you the location of the file path of the login item. https://docs.google.com/spreadsheets/d/1t6swpG1kN_8ZP6BX3CkEeOyUmsAv86pqU5yEvwIdAP0/edit?usp=sharing
Location: /Users/<username>/Library/KeyboardServices/TextReplacements.db
The data from this DB can be very handy in investigation ot get access to the suspects' machine. Following plist hold the information of the application that get start at the system boot:
open -a xcode ~/Library/Preferences/com.apple.loginitems.plist Launch Agents (User Level) - Background User Process
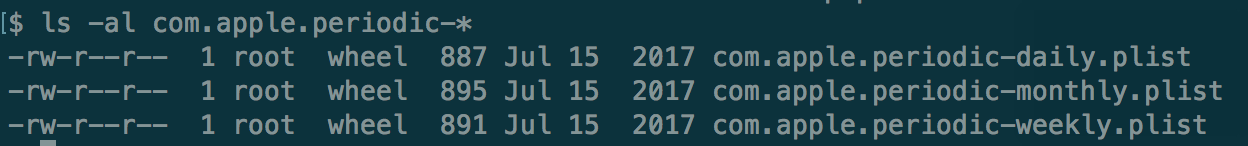
$ cd /System/Library/LaunchAgents/ $ cd /Library/LaunchAgents/ Launch Deamons (System Level) - Background System Process cd /System/Library/LaunchDaemons/ $ cd /Library/LaunchDaemons/ This is basically like a cron jobs.Best examples of Launch Daemons are following plist files: |
ArchivesCategories |
 RSS Feed
RSS Feed