|
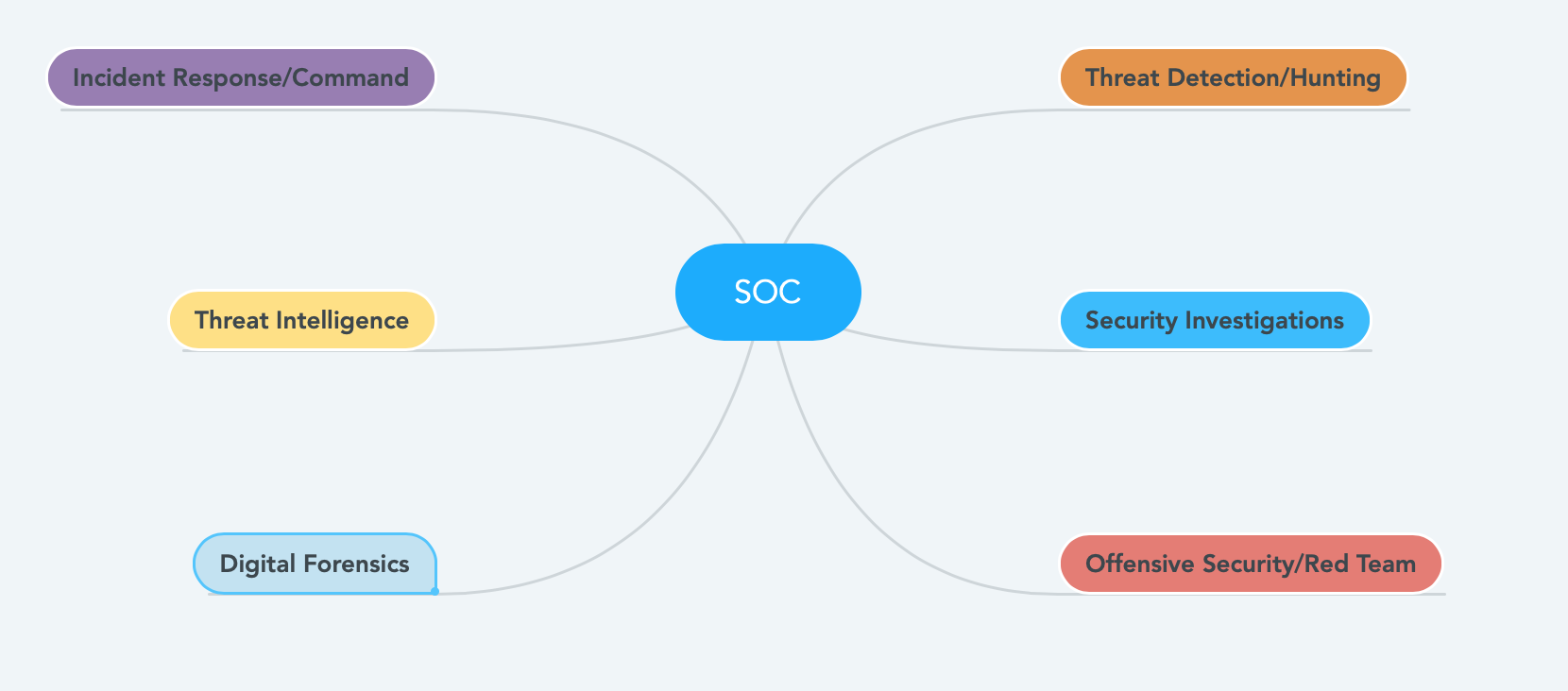
I have to build many SOC teams in my professional career. In this post, I’d like to declutter some of the myths about SOC. Let’s start with the basics. One of the most important questions is why your organization needs a SOC? Enterprise often collects a large amount of data in the form of logs. Simply storing the data is not valuable. The humongous amount of information needs to be searched for malicious activities. If there is malicious activity, you need a human to respond to it intelligently. SOC team members will do the Detection, Investigation, and Response to the incident. Another critical aspect of the SOC team (often overlooked) is the post-incident reviews. What are the sub-team/sub-group in a SOC? Key Roles in a SOC Team?
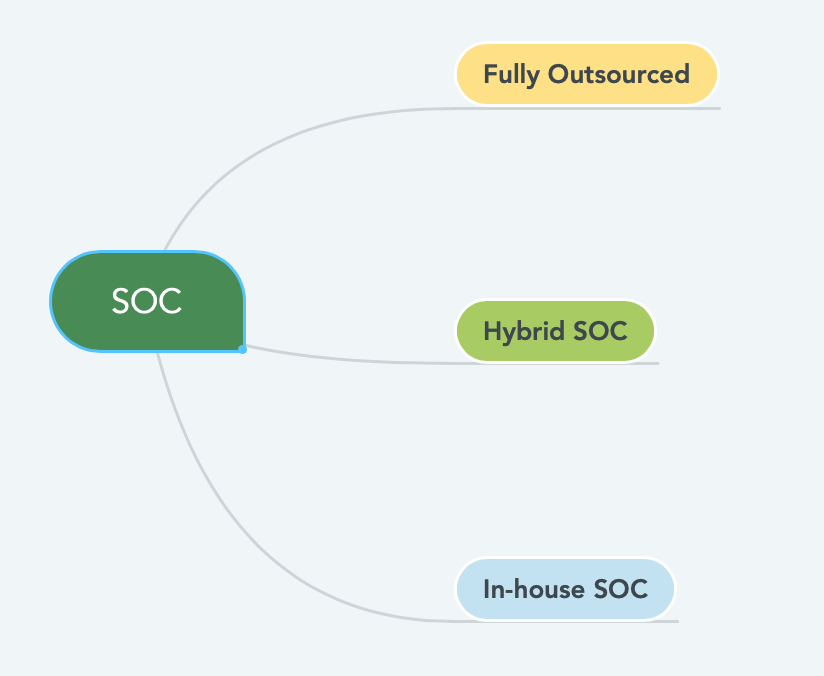
Types of Security Operation Center (SOC) Fully Outsourced SOC: Hiring, Building, and retaining SOC Teams are challenging and expensive. There are not a lot of experienced Cyber Security Analyst and Engineers out there in the market. It’s honestly a new career option. To avoid the hassle, the organization often decide to outsource the security operation fully to Managed Security Service Providers (MSSP).
There are a few advantages and disadvantages of having a fully outsourced SOC. The most significant benefit is the speed; you can have someone start looking at your data/alerts as soon as you sign the contract.In there is any anamoly, MSSP will do the hunt, investigation and escalated it to you pretty quickly. The biggest downside is the knowledge gap. All the knowledge/intelligence about your network/endpoint stays with the MSSP. As soon as you cancel the contract, it’s gone. Another significant disadvantage is the MSSP is expensive. You have to pay a lot of money out of your budget for the SOC. In some cases, the quality of the investigation can be poor too. Even after outsourcing your SOC, mitigating a malicious and compliance stays with the organization only. Usually, companies in the early stage will go for this model. MSSP will care more about the SLA’s rather that the quality of the investigation. If you are adopting this model, please ensure to discuss all the norms upfront, including the resume/profiles fo the Analysts. Hybrid SOC: It’s a combination of the MSSP + In-house SOC team. Usually, the Detection, response, and forensics team will be in-house, and the Tier-1 & 2 Analyst will outsource. The majority of the pros and cons of MSSP mentioned above applies here as well. The benefit is you keep your institutional knowledge. If your want to run your SOC 24/7 and your security team is only in one country this model will be helpful in terms of coverage and control. In-house SOC: Fully In-house SOC Teams are high, usually big size organizations with big budgets will go for this model. I’d say having a functional in-house SOC is a sign of maturity of an overall cybersecurity program. If your company is global, you may want to have your SOC team in mutiple time zones. Key Responsibilities of SOC
0 Comments
Threat modeling is a process of identifying all possible threats to a system so that they can be categorized and analyzed. It's a proactive approach to a system security. Essentially, you are trying to identify and fix the vulnerability before adversaries can exploit them. There are two broad categories:
Goals:
Approaches:
Threat Identification:
STRIDE Method (Developed by Microsoft): S - Spoofing - Attacker trying to gain the access by falsified methods T - Tampering - Any action resulting in unauthorized changes of the data either in transit of storage. R - Repudiation - The ability of user or attacker to deny the activity. I - Information Disclosure - Revelation of private, confidential or controlled information to external and unauthorized sources. D - Denial of Service - An attack to prevent the authorized use of the resource. E - Elevation of Privilege - An attack where a limited user account is transformed into a higher privileged account. |
 RSS Feed
RSS Feed