|
Purpose of NAT is to hide the internal IP. Purpose of using NAT Was to save the IPv4 Range. IPv4 is 32 bit.
Private IP Range Class A- 10.x.x.x Class B- 172.16.x.x - 172.31.x.x Class C- 192.168.x.x It also provides privacy as it conceals identity. Remember GDPR considers IP Address is PII. Virtual LAN (vLAN): Logically segment a network without altering the physical topology
Virtual Desktop Technology: - Remote Access - Extension of Virtual Applications Virtual Networking - Storage area network - Software Defined Network (Makes organization Vendor independent) Virtual Extensible LAN (VXLAN): As Organization are moving towards client, the requirement is that CSP (Cloud Service Provider). VXLAN allows you to segment your network and also solves the scalability limitation of VLAN's and provides benefits that VLAN Cannot. - You can create 16 Million VXLAN (24 bit VNID) vs 4094 VLAN (12 Bit VNID) We need VXLAN for the Scalability of VLAN Stored XSS: Attacker will find the vulnerable website and inject a malicious code into it. When the users click on the page the malicious code automatically get downloaded.
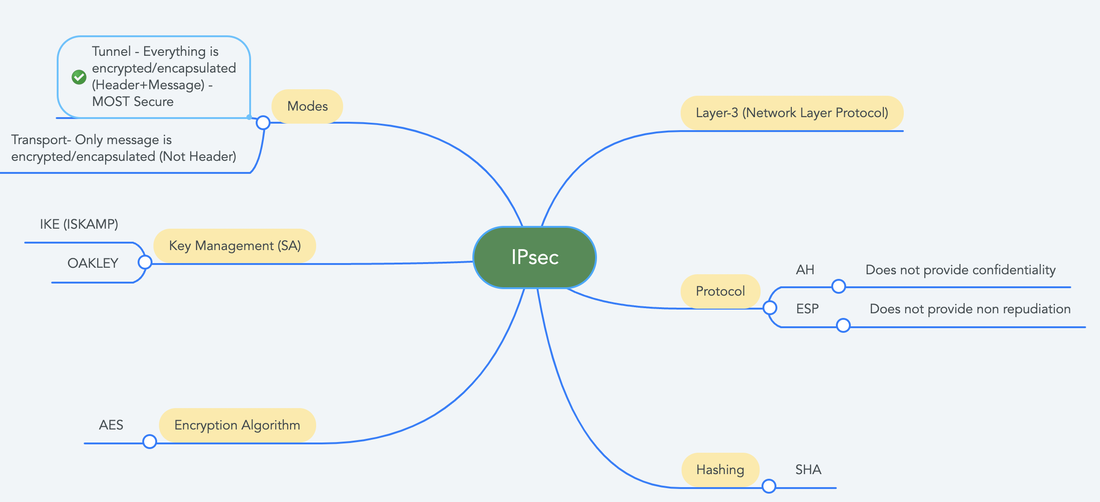
XSS attack usually targets the blogs, forums - (Places where people can add comments). There are three type of XSS: 1) Persistance/Stored XSS 2) Non Persistant/Reflective XSS 3) DOM based XSS Attack Breach: https://www.gnucitizen.org/blog/the-orkut-xss-worm/ Internet Protocol Security (IPSEC) is a standard architecture for setting up a secure channel between two entities.The entities can be anything like two system, two routers, two gateways or any other combination. IPsec uses Public Key Encryption to provide confidentiality, authentication, Integrity and Non-Repudiation.
IPsec relies of security association and there are two main associations: 1) Authentication Header (AH) - Provides assurance of Message Integrity and Non Repudiation. 2) Encapsulation Security Payload (ESP) - Provides confidentiality and Integrity of the packet content. Provides encryption and prevent replay attacks (Captures the packet and replay it later). Primary use for the IPsec is for the VPN. IPsec can operation in Two Modes 1) Tunnel Mode - Message + Header is encrypted 2) Transport - Only message is encrypted |
Archives
November 2022
Categories |
 RSS Feed
RSS Feed