|
Securing a container in AWS involves multiple layers of security, from the container runtime to the AWS infrastructure itself. Here's a step-by-step guide on how to secure a container in AWS:
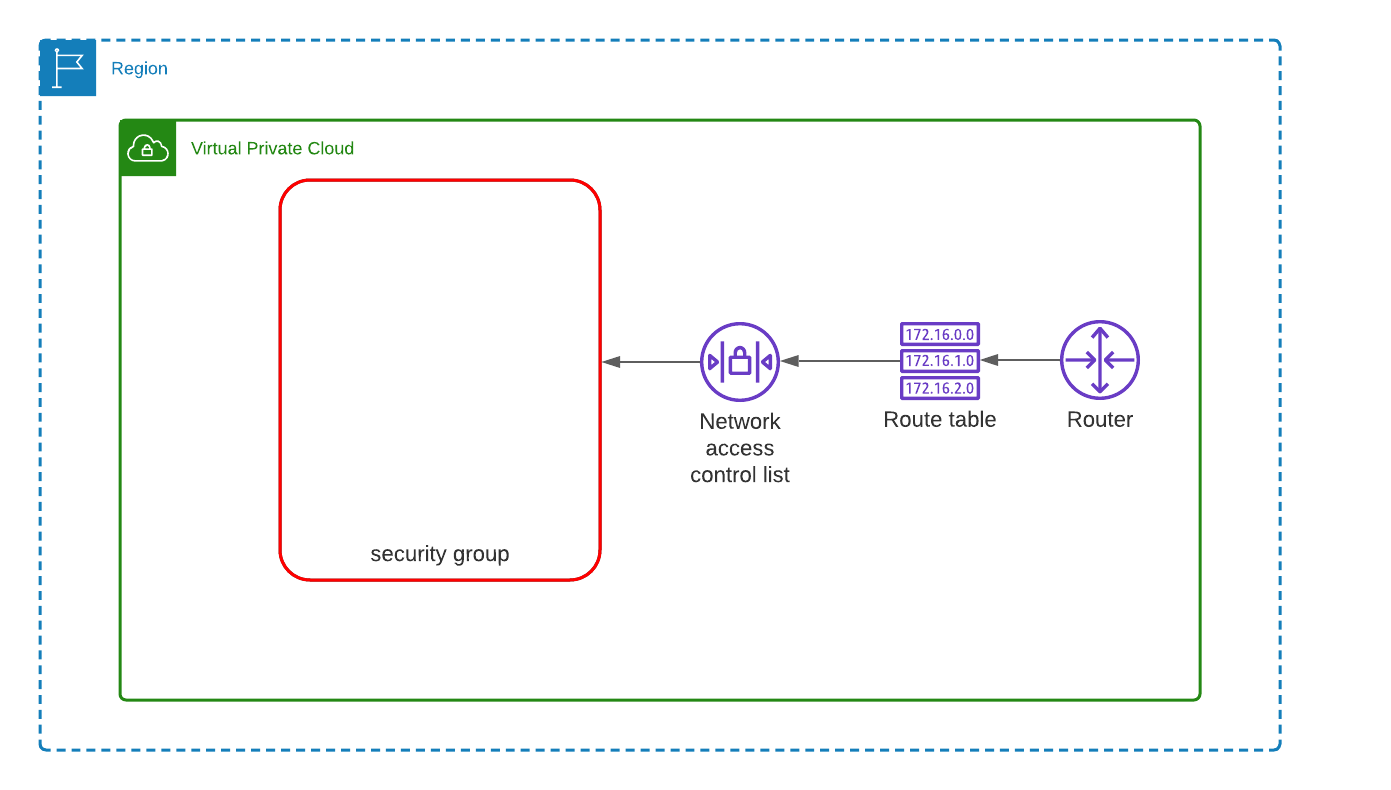
• AWS Account Security: ◦ IAM Policies: Grant the least privilege – only give permissions necessary to perform a task. ◦ MFA (Multi-Factor Authentication): Enable MFA for your AWS accounts. ◦ Audit regularly: Review AWS CloudTrail logs for any suspicious activity. • VPC & Network Security: ◦ Private Subnets: Deploy containers within private subnets, not directly exposed to the internet. ◦ Security Groups: Use security groups to define inbound and outbound traffic rules. ◦ NACLs: Use Network Access Control Lists to provide a second layer of security. ◦ VPC Flow Logs: Enable them to monitor and capture all IP traffic going to and from network interfaces in the VPC. • Container Registry Security (Amazon ECR): ◦ Vulnerability Scans: Use Amazon ECR to scan images for vulnerabilities. ◦ IAM Policies: Grant least privilege access to ECR repositories. ◦ Use Image Signing: To ensure the integrity and authenticity of an image. • ECS & EKS Security: ◦ Roles: Use IAM roles for ECS tasks and EKS pods to grant permissions. ◦ Logging: Enable CloudWatch logging for your containerized applications. ◦ Secrets: Store sensitive data in AWS Secrets Manager or AWS Parameter Store and reference them in your tasks or pods. ◦ Network Policies (for EKS): If you are using Amazon EKS, utilize Kubernetes network policies to control communication between pods. • Runtime Security: ◦ Container Scanning: Regularly scan containers for vulnerabilities. ◦ Read-Only Root Filesystem: Configure containers to have a read-only root filesystem to make it harder for attackers to write malicious files. ◦ Drop Unneeded Capabilities: Limit the Linux capabilities granted to your container. ◦ Use a Trusted Base Image: Use a minimal, trusted base image (like Alpine) to reduce the attack surface. • Monitoring & Logging: ◦ CloudWatch: Collect and monitor logs, metrics, and events. ◦ CloudTrail: Monitor API calls. ◦ Config: Use AWS Config to monitor configurations and relationships of AWS resources. ◦ Amazon GuardDuty: Enable GuardDuty for intelligent threat detection. • Updates & Patching: ◦ Keep your container orchestrator (ECS, EKS), container runtime, and container base images updated with the latest security patches. • Limit Resource Usage: ◦ Use resource limits and quotas to prevent resource exhaustion attacks. • Backup & Recovery: ◦ Regularly back up your container data. Consider using Amazon EBS snapshots, Amazon RDS, or AWS Backup. ◦ Have a recovery and disaster response plan in place. • Third-party Tools: Consider integrating third-party security solutions for deeper analysis and protection, such as Aqua Security, lacework, or Sysdig. By combining AWS's built-in security features with best practices for container security, you can ensure that your containerized applications are as secure as possible.
0 Comments
What is CloudTrail Logs?
Cloudtrail is an audit logs for the cloud tenant AWS API communication. It's created by default and retained for 90 Days. Each Log entry is an event. It only records the API Communication and it's also not a replacement of AV, EDR, MDR or XDR tools. For Instance, CloudTrails logs can log the entry of another service accessing the EC2 but it will not log the other activity happened inside the EC2 Instance. All CloudTrail logs are recorded in UTC. Default Log Retention Time? 90 Days (Free) - after 90 Days you should send/store it in S3 Bucket or Send it to your SIEM. What can you do with CloudTrail? The answer is a lot of things as far as Incident Investigation is concerned. Couple of common type answer you can find is: - What actions did a given user take over a specific time period? - What is the source IP address for a particular activity? Can you collect CloudTrail logs from all of your AWS Accounts and regions and put it in a centralized bucket? Yes, you can do it while creating a new bucket for all your Cloudtrail Logs. Detection Rules: Disabled AWS CloudTrail logging Splunk Queries: index=aws-cloudtrail | search NOT eventName in ("Des*", "List*","Get*") | stats count values(eventName) by userIdentity.arn userIdentity.type userIdentity.accountId | sort -count
Resources
AWS Inspector is used to list down all the Vulnerability as per the center of Internet security.
 What is AWS CloudWatch? One word: Performance Monitoring AWS CloudWatch is a monitoring service to monitor your AWS Resources and the application that you run on AWS. CloudWatch is used for Performance Monitoring. It can monitor EC2, Autoscaling Groups, Elastic load Balancer, Route53, EBS, Storage gateway etc. It can also monitor Host Level Metrics like CPU, Network, Disk etc. CloudTrail vs CloudWatch CloudTrails is like a CCTV and used for increasing the visibility for API Calls and CloudWatch Monitor Performance. Alerting CloudWatch Alerting: Yes, you can create alerts in CloudWatch as well and trigger notifications for it. Security Use-Case
Use AWS Config and Lambda to Ensure that S3 Bucket Remains Private
- AWS Config will trigger the Lambda Function to invoke SNS for any changes in the AWS. Create a Lambda function to monitor the Bucket ACL and Bucket Policy Changes. If the bucket ACL found public - Lambda function can over write it to make it private. if the Bucket Policy found public - it can trigger a SNS Notification to the Security Team. -- Cross region replication for the bucket ensures that the S3 Bucket is available in another region as well. -- Use "AWS Encryption CLI" to encrypt the data first before sending the data across the wire. |
Archives
October 2023
Categories |
 RSS Feed
RSS Feed