Message DigestUsed to ensure the authentication and integrity of information and the confidentiality SaltingSalting is used in hashing for the randomization MAC - Message Authentication CodeSmall Block of data that is generated using a secret key and then appended to the message. HMACHMAC works with any arbitrary hashing algorithm like SHA256 or MD5. If we use it with SHA 256 then it's called HMAC-SHA256. HMAC Is used to achieve integrity
HMAC Takes Three Input 1) Message 2) Hash Function 3) Secret (Symmetric Key) Steps (Sender and Receiver should agree on Hashing Algorithm and the much have the same Symmetric Key. 1) Sender concatenate the Symmetric key (Secret Key) with the Message. 2) Result goes though an hashing algorithm (MD5 or SHA) and a MAC Value is generated 3) The MAC Value is appended to the message 4) Sender Sends the message (With Appended MAC Value) to the receiver 5) Receiver concatenate the Symmetric key with the message 6) Result goes though an hashing algorithm and a MAC Value is generated 7) if Sender MAC Value matches with Receivers MAC Value - Integrity is achieved Here is a nice website for you to test this process: https://www.freeformatter.com/hmac-generator.html#before-output
0 Comments
Note: This content will only focus on High Level Cryptographic Concepts from CISSP Perspective.
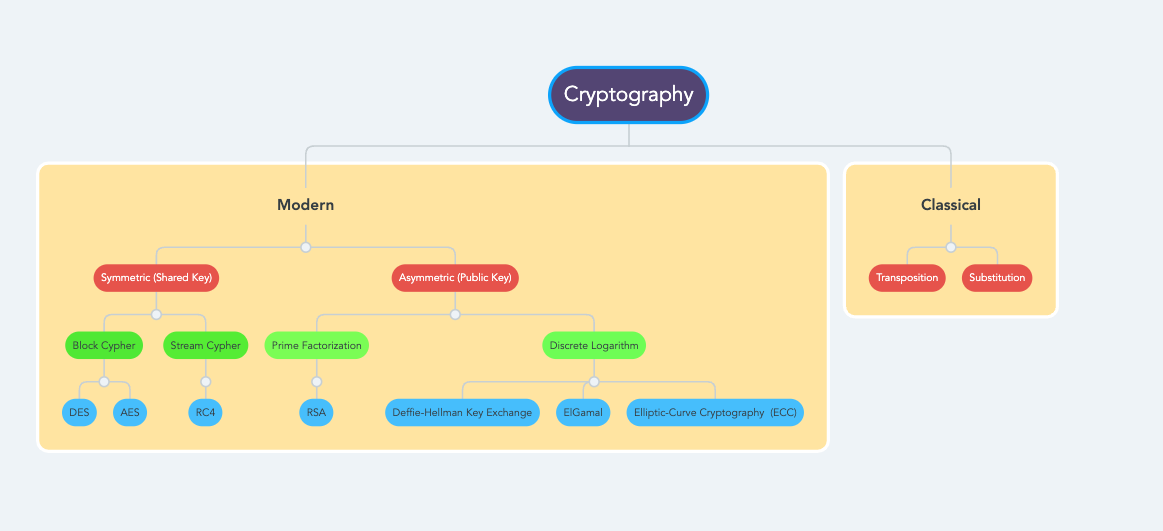
Crypto means secret and graphy means the science of writing, describing, representing. Cryptography is a science of secret writing. Cryptography has mainly two branches: Classical and Modern Cryptography Goals (PAIN/CAIN)
Confidentiality/Privacy, Authenticity, Integrity, Non Repudiation. Cryptography was originally introduced for Secrecy but over the time it's goals have evolved. Now a days, Cryptography is used to prevent unauthorized disclosure of information. Detect Tempering of the data, prevent repudiation and ensure the protection of data at Rest and in transit
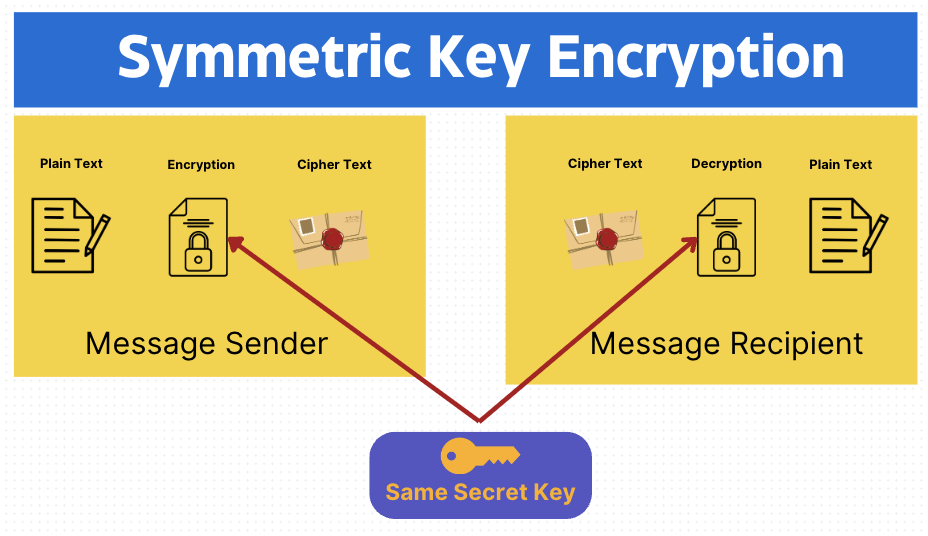
Symmetric Key Encryption
Symmetric Key Encryption has a single key. It's Fast but the biggest challenge is key exchange. The attacker can perform Man in the middle attack and intercept both the encrypted data and the key. If the attacker has the "key" it might be easy for the attacker to decrypt the data.
In Symmetric Cryptography key exchange happen using out of band (Alternate Channels) key distribution. Example of out of band key distribution sending Key by Text message, Email or on phone call etc.
There are mainly two types of Symmetric Encryption - Block based and Stream Based.
Stream based symmetric encryption is faster than the Block based encryption.
Data Encryption Standard (DES)
What is the key size of DES? 64 bit What is the effective key size of DES? 56 Bit Block Cipher Modes
In which mode Error Propagation happens? CBC and CFB
Double DES: Key thing to remember about double DES that it's vulnerable to Meet in the Middle Attack
RC4
Key Length is 128. RC4 is used in SSL. It's a weak algorithm also used it WEP
Advanced Encryption Standard (AES)
Development and Adoption: AES was established by the U.S. National Institute of Standards and Technology (NIST) in 2001 as a replacement for the Data Encryption Standard (DES). AES was selected through a competitive process and is based on the Rijndael cipher developed by Belgian cryptographers Vincent Rijmen and Joan Daemen. Block Cipher: AES is a block cipher, processing data in fixed-size blocks (128 bits for AES). Key Sizes: AES supports multiple key sizes: 128, 192, and 256 bits. The choice of key size affects the number of rounds the data goes through during encryption and decryption: 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys. Substitution-Permutation Network: Understand that AES operates on a 4x4 column-major order matrix of bytes, known as the state, and uses a series of linked operations involving substitution, permutation, and mixing of the input plaintext and the keys. Modes of Operation: Be aware of the different modes of operation for AES, such as ECB (Electronic Codebook), CBC (Cipher Block Chaining), CFB (Cipher Feedback), OFB (Output Feedback), and GCM (Galois/Counter Mode). Security: Recognize the high level of security provided by AES. Its larger key sizes make it resistant to brute-force attacks, and it is considered secure for most applications, including government and military use. Applications: AES is widely used in various applications, including SSL/TLS for securing internet connections, file encryption, VPNs, and wireless security protocols like WPA2. Performance and Efficiency: AES is efficient in both software and hardware, scalable, and performs well on a wide range of devices, from high-power servers to low-power mobile devices. Regulatory and Compliance Aspects: Understand AES's role in compliance with various security standards and regulations, such as FIPS 140-2, HIPAA, and GDPR for data protection and encryption. Cryptanalysis and Attacks: While AES is considered secure, be aware of theoretical attacks against reduced-round versions of AES or side-channel attacks, which exploit physical implementations rather than weaknesses in the algorithm itself.
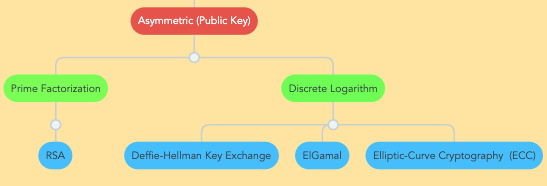
Asymmetric Key Encryption
Asymmetric Key Encryption has two keys Public and Private. Public key is shared and Private is kept secret. To Super Simplify things - think about your Debit Card - the PIN number is your Private key (You don't share it with anyone) even if your Card is with all your family members, no one will be able to take out the money until they know your PIN Number. There is a concern with Symmetric Key Encryption if A is sending a encrypted data to B with same key. How would you know who encrypted the data?
RSA (Rivest–Shamir–Adleman) is a Prime Factorization algorithm (Factoring the product of two large Prime Numbers) is used for encryption and digital signature
RSA is MOST effective algorithm for encryption and digital signature Elliptic Curve Cryptography (ECC) uses less key size and is suited best for low compute devices. ECC's offers higher efficiency and security at lower bit sizes. Therefore, more companies are preferring ECC over RSA.
Deffie-Hellmann - Key Negotiation AlgorithmEl Gamal
El Gamal is a Public key algorithm that can be used for digital signatures, encryption and Key exchange.
Digital Signature is designed to provide the proof of origin (Who Sent the data?). Lets discuss Digital Signature. Lets say we have our old friends again A, B and C
A and B both had encrypted a same set of data with C's Public Key and Sent it to C. In this Scenario we have achieved the confidentiality but not non repudiation. Even an attacker can find C's Public Key encrypt data and send it to C. How'd C know that the data is coming from a reputable source? To Solve this problem Digital Signatures are used to ensure non-repudiation. Lets understand the basic concept of Digital Signature If B wants to send the data to C. To Solve this issue B will encrypt the Hash Value of the data with his Private Key (B) and send Data to C. If C want to verify the sender C will use B's Public Key to decrypt the Encrypted Hash value. If C successfully decrypts the hash value with B's Public key - it means that the Non Repudiation is achieved. C can also compute the hash value of the received data and it matches with the B's Decrypted Hash Value - Integrity is also achieved.
Key Points
- Digital Signatures are used to Achieve Non Repudiation - Digital Signature is a Hash Value that has been encrypted by Sender's Private Key - Hashing is used to achieve Integrity - There are many types of Cryptographic systems available but we choose the one based on the sensitivity of the data. - Cryptanalyst are the people studying the science of breaking the algorithm system - Work Factor: Amount of time/Effort required to break a cryptosystem. - Which Cryptography is unbreakable? OTP - One Time Pad or Vernam Cipher - Two issues with Symmetric Algorithm is Scalability and Key Exchange. Quiz - Test your Knowledge |
ArchivesCategories |
 RSS Feed
RSS Feed