|
Goal: The goal of the treat modeling is to redure the risk as can be applied as a repeatable process. It has numerous benefits. In this post, we will learn to answer following questions:
What is Threat Modelling? You have build a Web App which allows visitors to subscribers to a mailing list and a sign-up for the account. When you list down systematically all the potential ways one can attack your application. That is Threat Modelling in a Nut Shell. Remember Two Key Terms - "Systematic Approach". Threat modelling should be a repeatable process in the SDLC. Second Important key term is "Abuse". You are constantly looking at the Attacks in order to find vulnerability. Another apporach is to develop a probable threat scenarios and list of threats. It's an holistic approach to reduce the risk of an application. Bug - Software Defects Vulnerability - Weakness that can be exploited Attack/Incident - Needs a Target, Need a Threat Vector (Path an attacker can take to exploit the vulnerability) and a Threat Actor. Threat Surface- Anything that can be obtainer, user or attacked by a threat actor Risk - Risk = Impact * Liklihood Why you should do Threat Modelling? Remember the goal is to Risk Reduction. There are other methodology to serve the same purpose as well for example Penetration Testing, Source Code Analysis, Architectural Risk Analysis, Vulnerability Scanning. Lets discuss about the reasons to use Threat Modelling
Who Should Theat Model?
When to perform Theat modelling?
Threat Modeling Approachs We will discuss about the following approaches of Threat Modeling. The End goal will be to Generate a list of Threats. Example Scenario - A simple webapplication. Anonomayos users can visit the website. Sites runs a Content Management System and only authorized users can access it. Mailing Componenet to send out web mails Asset-Centric/Risk Approach: In this approach we focus on the things you want to protect for example: Example : Databases, Email accounts, Account Credentials, Servers
Advantages:
Attacker-Centric/Security Approach:This apporach is preferred by Pentesters. You'll need a team of highly qualified Security Engineers to succeed in the approach.
Advantage:
Application-Centric Approach: Think about the Application and get famalier with the application. User Step 1: Draw a diagram of the application. For example: Data Flow Diagram Step 2: List threts for each eleements. STRIDE (Threat Classification Model), OWASP Top 10 Step 3: Rank Threat using classification model Advantages:
Threat Modeling Methodologies In this section, we will discuss about the approaches for threat modeling focused towards the asset centric and application centric approach. PASTA - Process for Attack Simulation and Threat Analysis This is a threat modeling and threat analysis process. It's an asset centric approach with 7 Stages
Advantages:
Microsoft Threat Modeling It's a Threat Modeling Framework. Focuses on Technical risk, It's a developer driven approach.
Advantage:
Octave - Operationally Critical Threat, Asset and Vulnerability Evaluation
Trike
Process
Advantage:
Disadavantage
VAST Visual Agile Simple Threat Modeling Two Threat Model Types
Good for companies following Agile Advantages:
Disadvantage:
What is the best methodology?
Choose a methodology based on team, organization and objective. Recommendations Asset Centric - PASTA Application Centric - Microsoft Threat Modeling
0 Comments
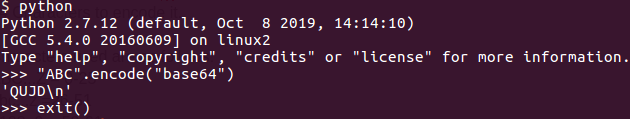
If you are working in the DFIR, you might have encountered Base64 Code many times. In this blog post, we will talk about the basics of base64 encoding.
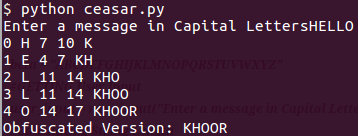
ASCII Data - Each Character turns into one byte A = 65 (Binary 0b01000001) B = 66 (Binary 0b01000010) C = 67 (Binary 0b01000011) The 3 Letter String = 24 Bit ABC = 0b010000010100001001000011 For base64 - we'll need ot break it in the group of 6 bits. 6 Bits will have 64 Combination and will need 64 Characters to encode it. Characters used are as follows: ABC...Z = 0-25 abc...z =26-51 0123..9 = 52-61 +,/ = 62,63 I am going to use spaces for the ease of reading ABC = 0b01000001 01000010 01000011 6-bit Groups = 0b010000 010100 001001 000011 Decimal = 16 20 9 3 base64 = Q U J D In this post, I am going to talk about the basic fundamental and concepts of Cryptography. Let's start with Obfuscation and Encryption. In layman's language, encryption techniques are used to hide data or make is difficult to read. The term 'Crypto' become super popular because of the introduction of the currencies like Bitcoin, Litecoin, Ethereum etc. For us, it's just a form of protection, our focus will be on the cryptography applied to the communication, storage, messages etc. We will be using Python for the code nuggets. Lets start with the 'Caesar Cipher' and 'ROT13' Caesar Cipher: It's an old trick where you just move every letter forward three character in the alphabet. Plain Text - abcdefghijklmnopqrstuvwxyz Cipher Text - defghijklmnopqrstuvwxyzabc For example: hello = khoor Lets implement this in python! beta = "ABCDEFGHIJKLMNOPQRSTUVWXYZ" ROT13 will do the shift by '13' instead of '3'
In the Mobile Application Penetration Testing, the end user is in the control of the device.There are usually four phases
Vulnerability in mobile apps can occur due to several reason like misconfiguration in code level bugs. There is a huge need to perform a penetration test and security analysis before releasing a mobile application. If you think in terms of data, there are four layers usually a mobile app will have some data
Another way to think about the data in Mobile Apps are:
Threat modeling is a process of identifying all possible threats to a system so that they can be categorized and analyzed. It's a proactive approach to a system security. Essentially, you are trying to identify and fix the vulnerability before adversaries can exploit them. There are two broad categories:
Goals:
Approaches:
Threat Identification:
STRIDE Method (Developed by Microsoft): S - Spoofing - Attacker trying to gain the access by falsified methods T - Tampering - Any action resulting in unauthorized changes of the data either in transit of storage. R - Repudiation - The ability of user or attacker to deny the activity. I - Information Disclosure - Revelation of private, confidential or controlled information to external and unauthorized sources. D - Denial of Service - An attack to prevent the authorized use of the resource. E - Elevation of Privilege - An attack where a limited user account is transformed into a higher privileged account. |
 RSS Feed
RSS Feed