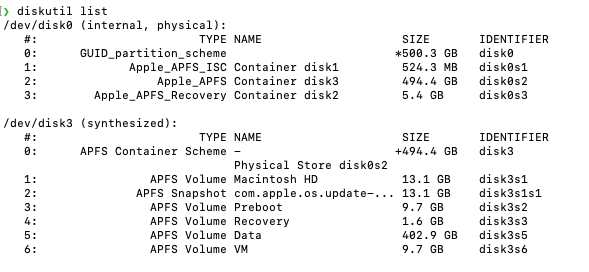
APFS - Apple File SystemAPFS uses a logical volume to create a synthesized disk containing additional virtual volumes. Apple uses the APFS File System. One File system across all the devices. APFS is designed to keep SSD and Flash Storage in mind. HFS does not offer full disk encryption by default. FileVault was added later. Support 4 Billion Files. Time only in Seconds. APFS has built-in Encryption. Snapshot Support - allowing us to revert in time to Volume Shadow Cop.Time in Nano Seconds (9 Zeros) - 1 Second is 1 Billion Nano Seconds. Support 9 Quintillion Files MacOS KernelBSD and Mach microkernel are the heart of the MacOS. BSD Security policies and Mach access permission constitute the core foundation of the security in the MacOS and super critical in enforcing the local security. How does MacOS protects the Kernel of the MacOS? "Code signing" protects the kernel. Apple won't allow anyone to access the kernel until the code is signed. Kext is not encouraged by Apple You should not get confused with the system extension. System Extensions operate in the User space only & Kernel Extension will operate at the Kernel Level User PermissionMacOS uses Mandatory Access Control (MAC) policies that can't be overwritten and are not visible to users. MAC enables several key security features like Sandboxing, parental control, System Integrity Protection Understanding APFS Disk OrganizationRun this command on a MacOS terminal to under the disk structure of an APFS System. diskutil list Let's delve into the intricacies of this screenshot. It's a complex concept, but I'm here to guide you through it. You have one actual Physical Disk; see/dev/disk0. The Physical disk has a logical volume to make a synthesized disk, which is /dev/disk3. The synthesized disk creates a container scheme with virtualized volumes and multiple containers. When doing the forensic analysis, you look for the APFS Volumes Data Virtual Disk (5). You may want to combine the APFS Volume Data with the Snapshot Container, So Snapshot(2) + APFS Volume Data (5) makes your Macintosh HD. The Physical Disk (/dev/disk0) has containers, and containers (/dev/disk3) contain virtualized volumes. Data is stored in the volumes (Snapshot + Data). Note: Most of the volumes are read-only except for data volume Signed System Volume: Apple has started producing signed system volumes, which means that whenever you download or update macOS, it will be connected to the Apple server via the Internet to verify the digital signature of the code. After verification, Apple Disk makes a snapshot (2) of itself, i.e., duplicating the APFS system volume (1) and creating a recovery volume and VM. So Technically, APFS-Data is the only volume you need to image (5) What about Deleted Files? Apple has TRIM enabled on SSDs for performance optimization. TRIM's job is to tell the system to continuously wipe the memory cells in the SSD when a file is deleted. This increases the overall longevity of the SSD but makes a Forensics Technician's life harder. It's also an Instantaneous process—the moment the file is deleted, all the memory cells related to it are gone. People claim they can recover the data even if TRIM is turned on. Truly, they are getting the data out of the Local Time Machine Backup if it's enabled. Command: tmutil listlocalsnapshots / * Snapshots is also stored in the data partition (5) only. You can perform the differential analysis using the image and the snapshot data. FileVault - Apple Software EncryptionFileVault is an Apple software encryption found in almost all MacOS versions, in addition to hardware encryption (Secure Enclaves). There are no backdoors to bypass FileVault. Uses XTS-AES-128 for data encrytion. You'll need the admin password or recovery key to decrypt it. Secure Enclave - Apple Hardware Encryption (T2 Chips)T2 was scary. When it was launched, I remember talking to a colleague about the end of the MAC Forensics type of stuff. All the Data in Mac SSDs are encrypted at Rest. Secure Enclaves are built into the Apple silicon processors. Admin password must be known to access the data. Image AcquisitionLogical Collection/ImagingDue to the changing world and increasing complexity, the Physical imaging of Macs is becoming less popular. Logical imaging is more prevalent, but it introduces complexities like changes in timestamps. Memory Collectionchick out: https://www.volexity.com/products-overview/surge/ They have signed kernel extension to image the Mac memory. System Integrity ProtectionSystem Integrity Protection (SIP)
Key MacOS ArtifactsUser Data (grab the profile) /Users/%username&/* Web Browser Activity /Chrome/Safari/Opera/Firefox /Users/<username>/Library/* iOS Backup /Users/<username>/Library/ Application Suppport/MobileSync iMessage /Users/<username>/Library/Application Support/ Airdrop iCloud Backup /Users/<username>/Library/iCloud Unified Logs /private/var/db/diagnostics Lockdown Folder () /private/var/db/lockdown QuarantineFiles-users/username/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2 Bash History /Users/<username>/.bash_sessions /users/<username>/.bash_history Spotlight Shortcuts /Users/<username>/Library/Application Support/ com.apple.spotlight.Shortcuts Daily.out - which are the things getting into the machines /private/var/log/daily.out Finder MRU /Users/username/Library/Preferences/com.apple.finder.plist App Store downloads /Library/Receipts/installHistory/plist FSEvents (Running list of things going on the machine) /.fseventsd(folder)
User Account
Quarantined Files
USB Forensics
Extended attribute: Xattr -xl <filename> kMDItemwherefroms mdls <filename> Installed Application /Library/Receipt/Installhistory.plist Network Usage /private/var/networkd/netusage.sqlite File and Folder Access
Trash .Trash is a hidden folder for each user .ds_store will give the information about Local Snapshots: Command: tmutil listlocalsnapshots / Key CommandsTimestamps that Mac uses are stored in extended Attributes. There are a couple of ways to look at them. MDLS is probably the most forensic timestamp on a file. However, it's important to note that many tools get the data from the Stat command, which can potentially lead to an incorrect timestamp. mdls <filename> View Timestamp of a File stat -x <filename> Note: Tools are just excellent; they simplify your investigation process but can make mistake also. A good tip from a fellow Forensicator is to ALWAYS Verify from TWO Souces before adding it to your report. If a tool shows you a MACB time for a file - Always Verify it with the extended attribute (MDLS) data. MacOs Security Incident Response Key ArtifactsAt midnight, you receive a page from a user who believes their Mac is compromised. How do you quickly triage the endpoint and determine whether it's a True Positive or False Positive?
Note: Not going into the whole lifecycle on the IR Process. Starting off directly with collections. What should you look for if it's a Mac malware? The majority of the MacOs malware will persist in 3 ways (although there are other ways too): 1) Launch Agents ( 2) Launch Deamons (/System/Library/LaunchDaemons) 3) Login Items (/System/Library/LaunchAgents) This is a great way to start your investigation if you want a Mac Malware. |
ArchivesCategories |
 RSS Feed
RSS Feed