|
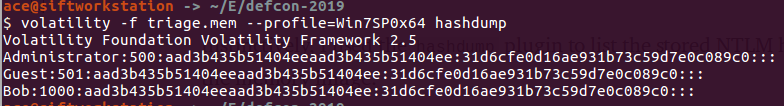
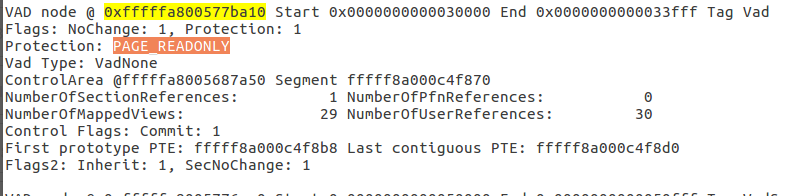
Thanks for Champlian Collage Digital Forensic Association to put up unofficial DFIR 2019 CTF for us. You can download the image from this dropbox link: https://www.dropbox.com/sh/4qfk1miauqbvqst/AAAVCI1G8Sc8xMoqK_TtmSbia?dl=0 CTF Link: https://defcon2019.ctfd.io/ In this post, I am only covering the "Memory Forensics Section" of the Defcon DFIR 2019 CTF. I'll be doing other posts for the other parts of the Defcon DFIR 2019 CTF. I am using Volatility to do this challenge but feel free to use the tool of your choice. Some of the questions are complex, please try it and feel free to contact me if you have any questions, Happy to help! flag<EMPLOY~1.LNK>
Memory images can contain the contents of many processes, activity and files; including Internet Chat History. BIOS settings and VSS files (stored on user's hard drive) are not present in the memory image!Pretty much everything in the Operating system goes through Random Access Memory (RAM). Data available in the RAM is of immense value.
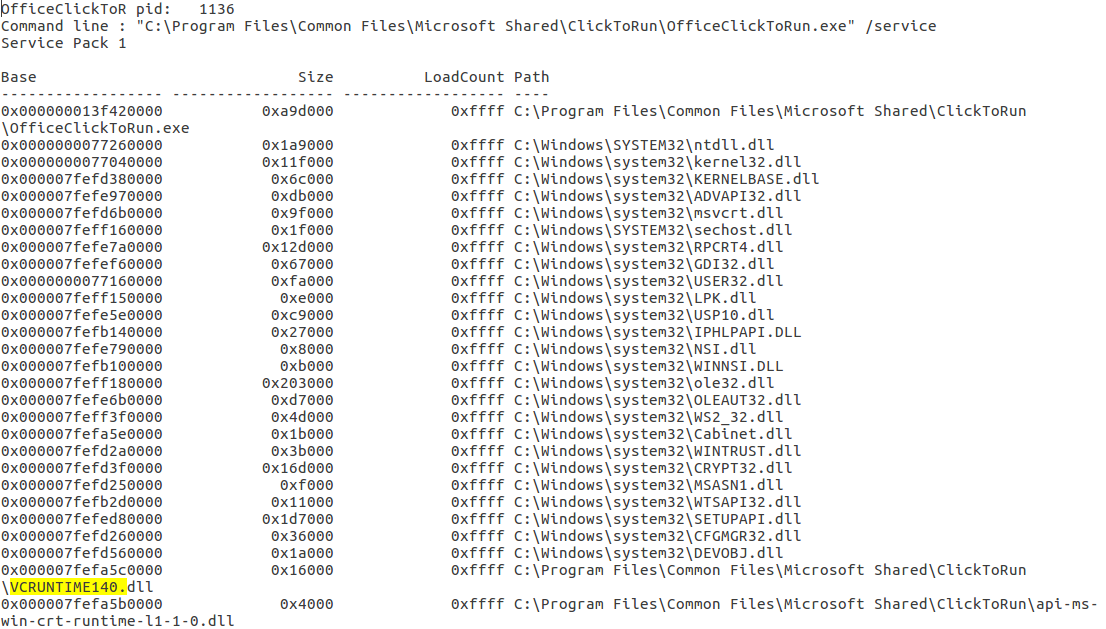
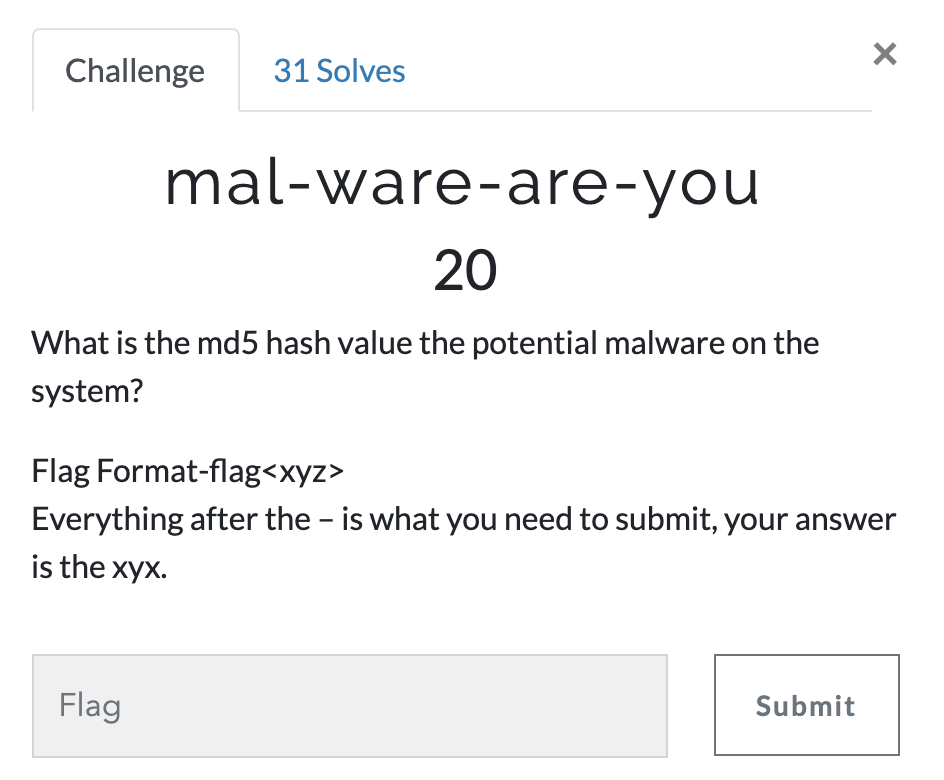
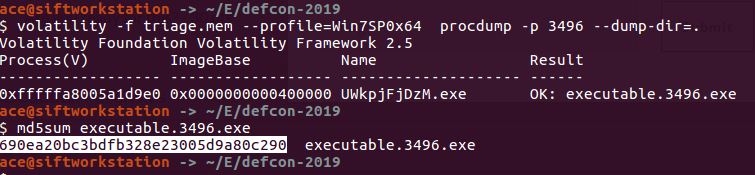
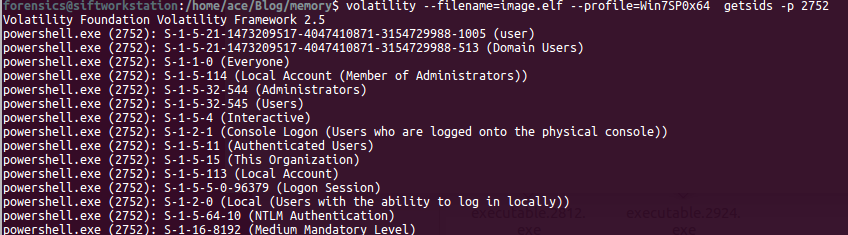
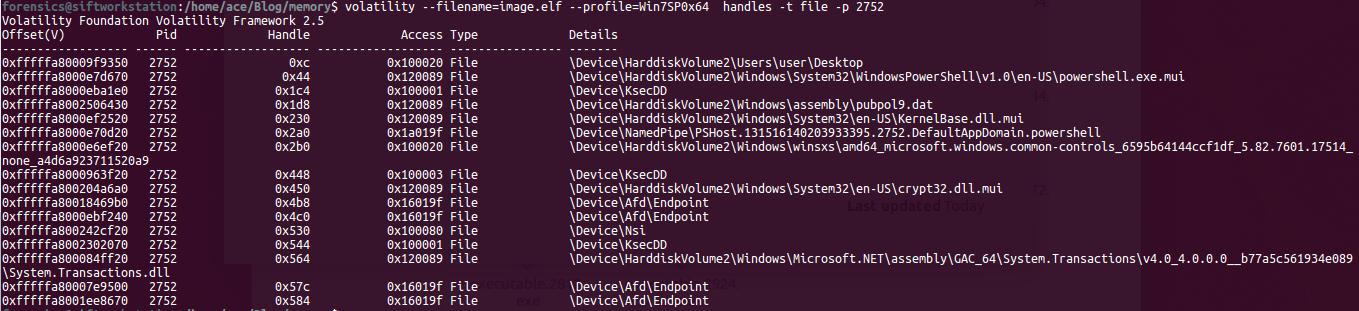
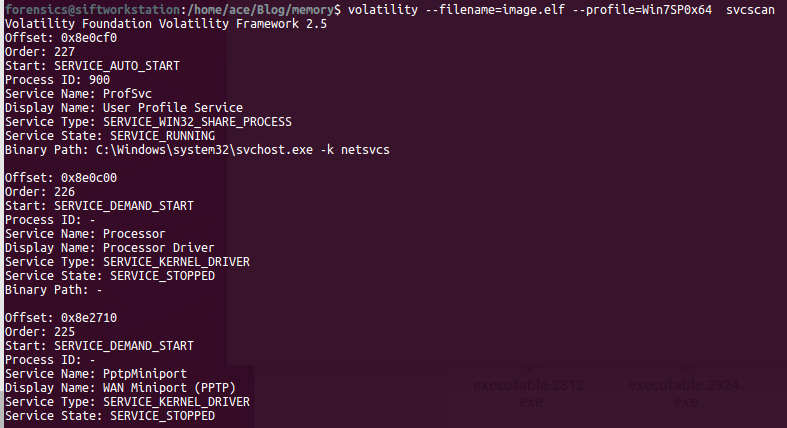
In order to understand a memory process, we need to understand the following terms: 1) DLL's: Dynamic Linked Libraries, this will define the capabilities of the process. Modern day malware uses it's own DLL's to take control of the process. 2) Handles: A pointer to resource . There are many pointers like file pointer, directory handles, Registry handles, Mutex, Event handles. 3) Threads: This of process as a box that will have all the items to do the work. Many threads will run to get things done within a process. 4) Sockets: Network connections endpoints. Helps us in tracking back the network activity of a process. # Analyzing DLL's By analyzing the loaded dlls in a process we can answer questions like - what process was doing? You can use another plugin called dlldump to carve out dll's for more analysis. use ldrmodules for more detailed analysis of the dll's DLLLIST getSIDS - Security Identifiers This will give the information about the about the processing spawning and permissions. Every processes in spawned by an account and every account has some permissions. Most system processes are spawned by system account itself. This will help in identifying malicious process. Link:https://support.microsoft.com/en-us/help/243330/well-known-security-identifiers-in-windows-operating-systems HandlesEach process can have multiple types of handles. use -t flag to find specific type of handles. -t Mutant Modern Malware uses Mutant to tag a processes as captured. Excellent IOC. Look for keywork "Mtx" Svcscan Mainly used by malware to maintain 'Persistance' (ability to survive reboot)
|
Archives
August 2019
Categories |
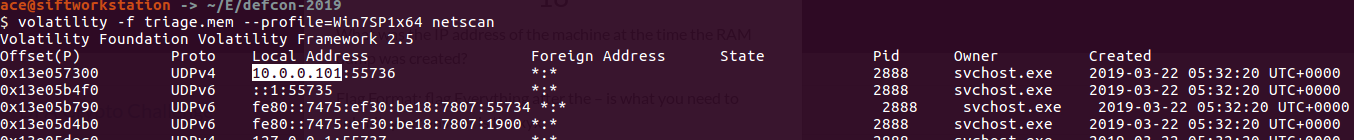
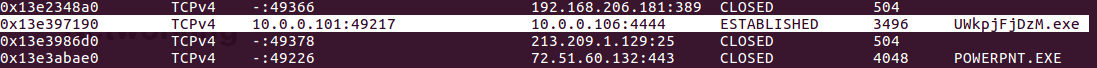

 RSS Feed
RSS Feed