|
Launch Agents (User Level) - Background User Process
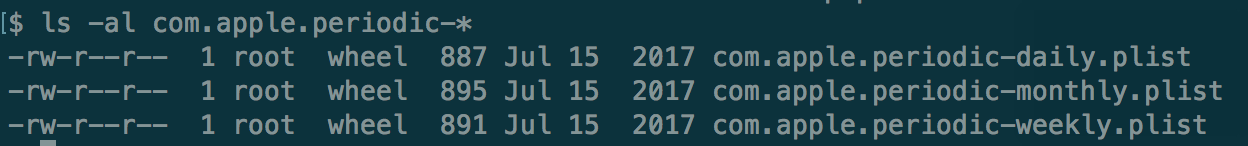
$ cd /System/Library/LaunchAgents/ $ cd /Library/LaunchAgents/ Launch Deamons (System Level) - Background System Process cd /System/Library/LaunchDaemons/ $ cd /Library/LaunchDaemons/ This is basically like a cron jobs.Best examples of Launch Daemons are following plist files: Bash History file is very useful for investigation purposes.
Location: /Users/<username>/.bash_history - Usually it stores upto last 500 Bash Command but sometimes in live response/collection - you may get little more.
Antedating: Creating a document with incorrect time stamps.
Investigation:
How to antedate a document?
Readings: http://www.cse.scu.edu/~tschwarz/COEN252_13/Papers/antedating.pdf |
ArchivesCategories |
 RSS Feed
RSS Feed