|
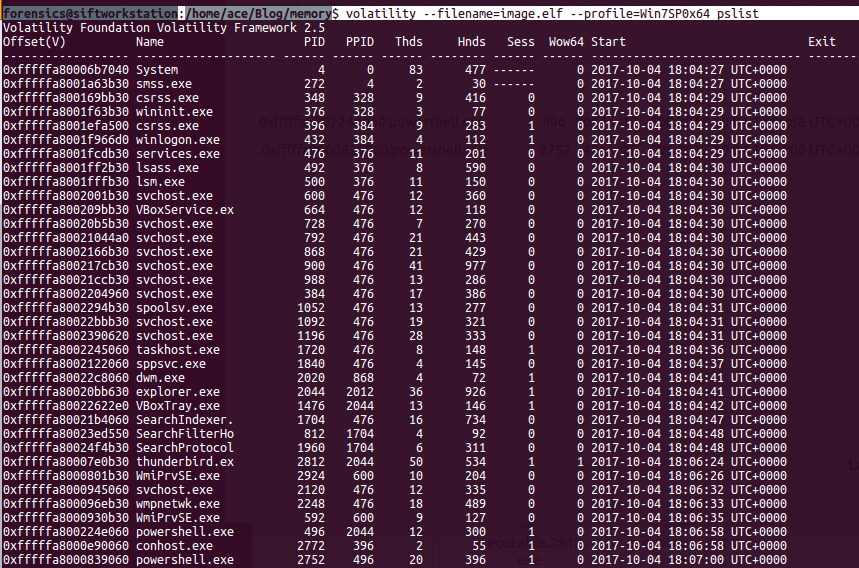
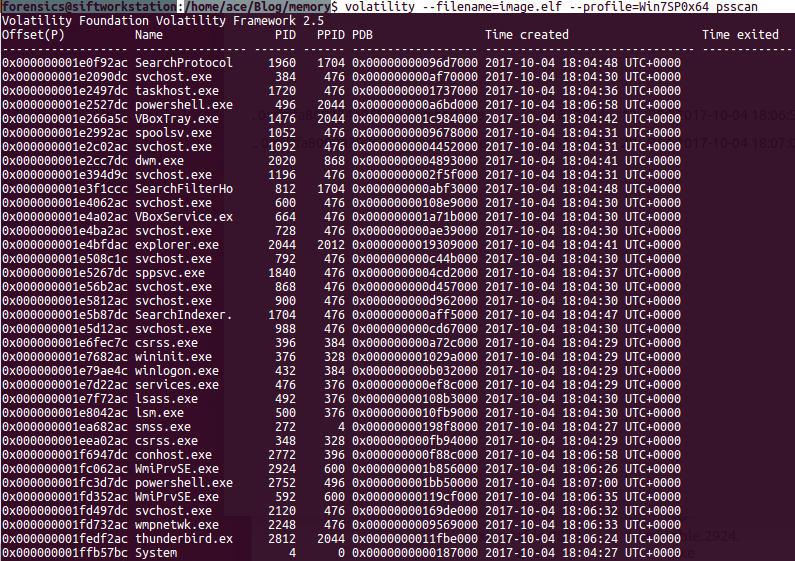
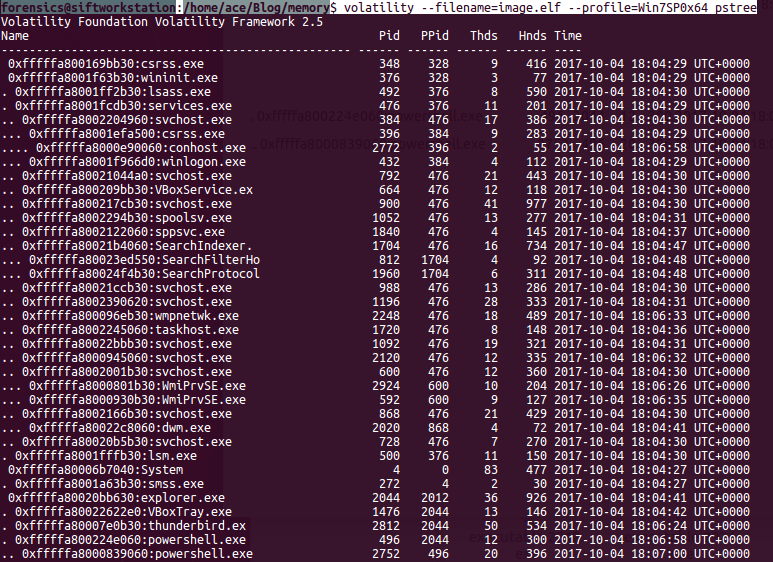
Analyzing Memory images with the tools like volatility is easy. Traditionally there are only few ways to identify a malware in a system like signature, contradiction and behavior. The key question is where to start you analysis. As an investigator, it's critical to have an structured though process before starting an investigation. Personally, I like to start with analyzing the processes. Processed will give us information about what was running on the system. The metadata of processes are in Executive Process Block or Eblock like name of the process, process identifier(PID), Parent PID, Offset (location in the memory) etc. The kernal uses DLL (Doubly Linked List) to track processes. Only running processed will be found in the list. There are other commands in volatility to review the unlinked processes as well.
There are three key plugins available to review the processes: 1) pslist - show all running processes (Not orphaned). quick results 2) Psscan - Comprehensive scan of memory may identify the not running processes. 3) pstree- print process list as a tree (very useful). You can also use -v flag for more verbose output.
Comments are closed.
|
Archives
August 2019
Categories |
 RSS Feed
RSS Feed