|
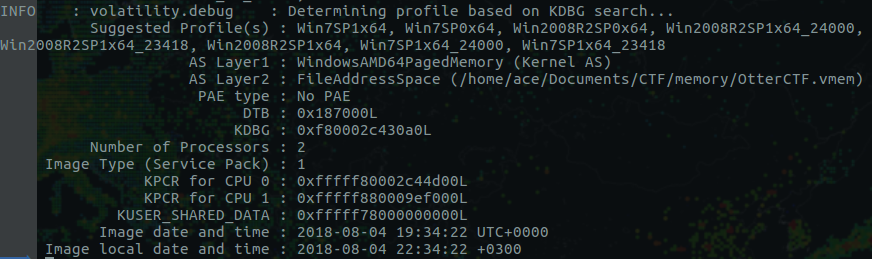
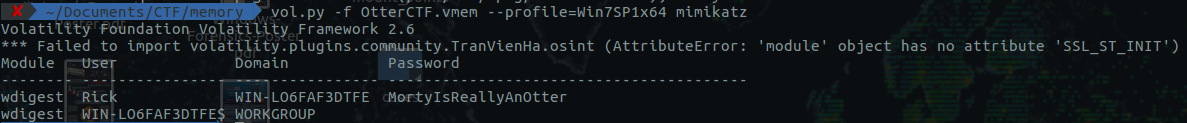
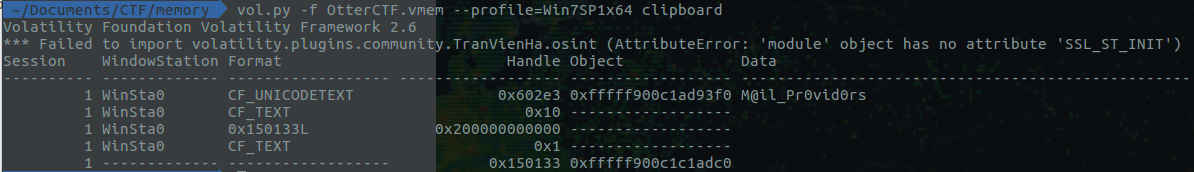
In this blog post, I'll be solving the Otter2018 Memory Forensics CTF Challenge. Alongside the challenge, I'll be share the key concept of memory forensics as well. The blog post will be an excellent start for the beginners. Lets start: 1) What is the password? The first question is for 100 Points: You got a sample of rick's PC's memory. can you get his user password? format: CTF{...} Image download link: https://mega.nz/#!sh8wmCIL!b4tpech4wzc3QQ6YgQ2uZnOmctRZ2duQxDqxbkWYipQ Solution: I'll be using "Volatility Foundation Volatility Framework 2.6" for the analysis of the memory image. Couple of things we need to do as soon as we get a memory image is to identify the profile of the image. You can do it by simply running the following command: vol.py -f '/home/ace/Documents/CTF/memory/OtterCTF.vmem' imageinfo 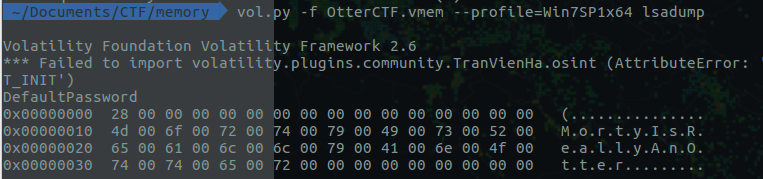 Investigation Tips: Lot of useful information here: 1) Suggested Image Profile: We'll use Win7SP1x64 for this case 2) Image Date and Time in UTC: 2018-08-04 19:34:22 UTC+0000 The first place to look for is lsasecrents use this command vol.py -f OtterCTF.vmem --profile=Win7SP1x64 lsadump Another cool plugin is mimikatz Volatility offer an amazing plugin called 'clipboard' clipboard - Extract the contents of the windows clipboard. We'll use this plugin to see the content present in the clipboard. This might be useful for future questions.
Comments are closed.
|
Archives
August 2019
Categories |
 RSS Feed
RSS Feed