|
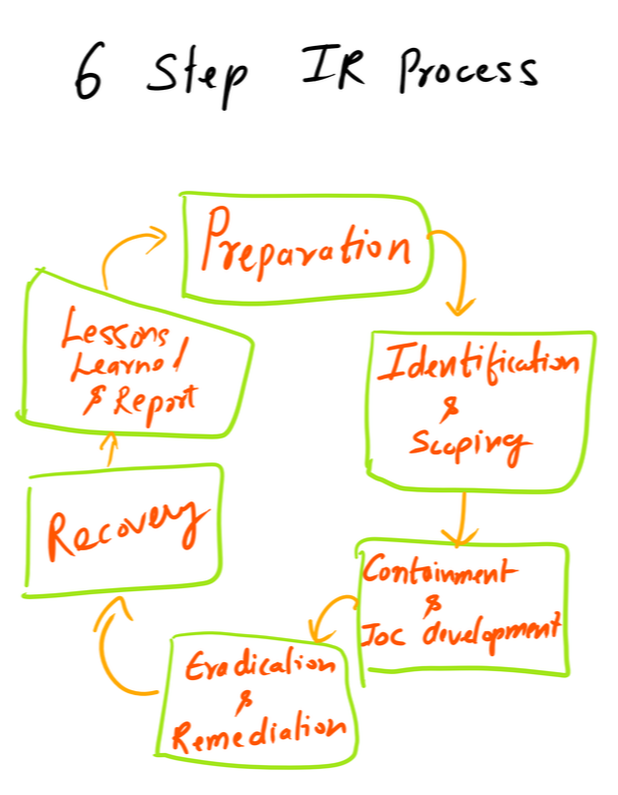
Six Steps of Incident Response are as follows:
The Incident management should also focus on understanding the motivation of the adversaries. Lets talk about the each step in detail below: Preparation - Organizations should not only focus on the development of an incident response capability but also think of the ways to respond to the incidents. Prevention is better than cure - Companies should focus on the ways to prevent and incident. Logging and retaining the right data is the key. This will help the security operations team to respond to the incident in a much faster way. * Another key aspect is to have a centralized database and use some sort of SIEM with it for free text search to enable your analyst to search quickly and report finding to the incident commander. * To respond better to Incidents, Organization does prepare cybersecurity plans, performs tabletop exercises, hires retainers and purchase cyber insurance, etc. Identification - Majority of the companies rely on the employees or law enforcement agencies to notify about the abnormal activity (Third Party). Having a good detection plan is critical for the organization to succeed. Usually, detection teams write/develop alerts based on the data EDR tools, and threat intel feeds. The adversaries are smart enough, and they know your detection methods very well. An advanced intruder will drop malware on only a few machines and move laterally to gain access to other machines and maintain persistence there. As a knee-jerk response, the majority of the organization will move to eradication without scoping the incident well. To identify the right Indicator of compromise must be granular like IP address, Hostname, Command, and Control (C2), FQDN, etc. Calculated Data is also critical like Hash Value on a file. Think about it - Will you trust an IP or a Computed Malicious hash more? In the majority of the cases, you'll not be able to find the IOC just based on granular and calculated data. You'll need to come up with behavior. User Behavior Analytics can play a crucial role in identifying an intruder. * Make sure you "Scope" the incident very well before moving forward else you'll end up month fighting the same intruder. Containment - To Scope an Incident in the right way, you'll need the information about the actions taken by the intruder. Things like malware type, how they are moving laterally, how they are maintaining persistence etc. Develop the intelligence about the intruder before moving to remediation. * Tools like Joe Sandbox, VirusTotal, Yara can help you in developing the intelligence as well. Eradication/Remediation - This is time to mitigate the incident, totally depends on the type of adversary you are fighting. You may need to block some IP, Sinkhole domains, change passwords etc. Recovery/Actions - There are several things that the security team will learn during the incident. Recovery is things like improving the authentication, or adding another layer of Authorization, Add additional logging, purchasing/implementing new tools for visibility etc. Follow up / Post Incident Review - Follow up needed to make sure the incident is completely mitigated and adversary is removed completely. May be you can have your red team perform the similar attack to see if there are any open loopholes. Key Point: The adversaries are smart and they know about majority of the tools and methods out there in the market. To be successful against them move towards the intelligence driven incident response. It's critical to understand the motive of the intruder. You should ask this question multiple times during an investigation. What is he/she trying to get? |
Archives
April 2020
Categories |
 RSS Feed
RSS Feed