|
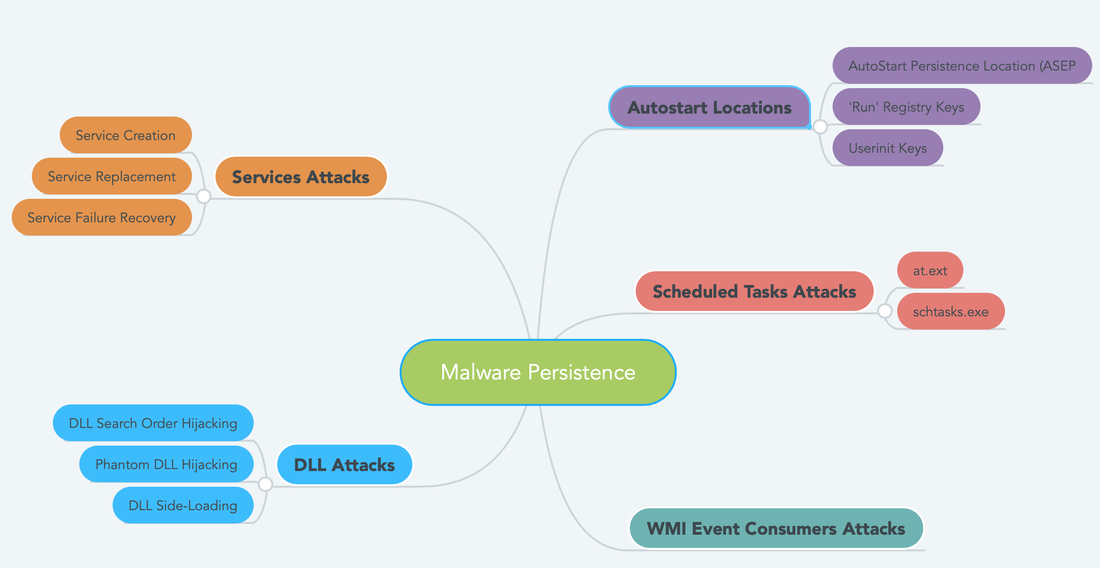
Windows Services Attacks:
Service Creation: Malware authors utilized windows services to maintain the persistence in the machine. There are some services that can be started at the boot by configuring the start type value by manually or by some event. Windows has tons of services, malware author utilized the concept of "Hide in Plain Sight". Once the attacker has admin rights he/she can easily create a new service or modify an existing one. Service Replacement: Malware author will find an unused service and replace it with a malicious executable and set it to autostart. Service Recovery Mode: Load a malicious services and an existing service crashes |
Archives
September 2019
Categories
All
|
 RSS Feed
RSS Feed