|
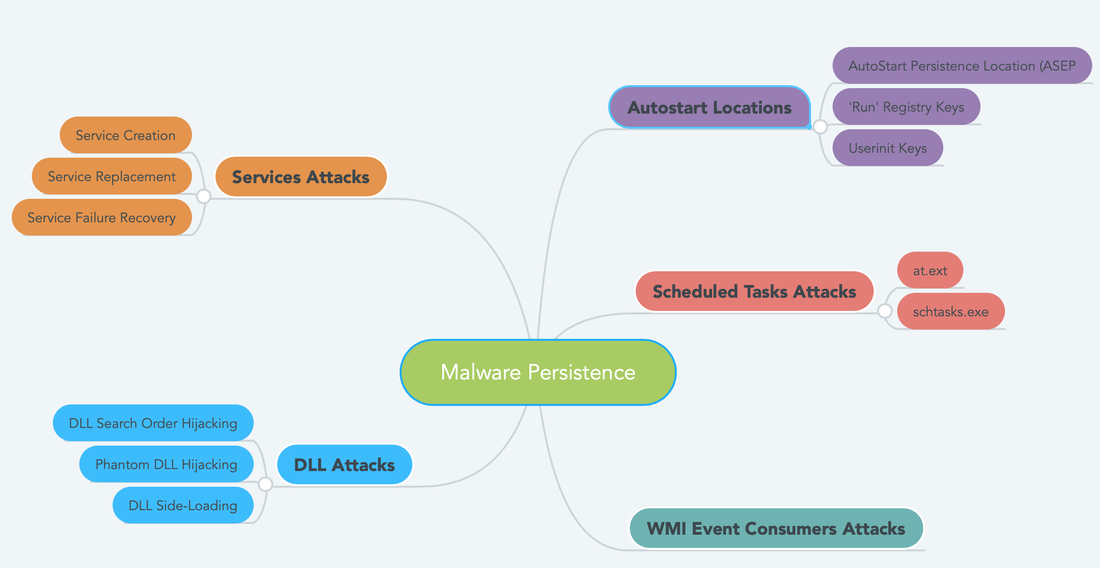
Windows Services Attacks:
Service Creation: Malware authors utilized windows services to maintain the persistence in the machine. There are some services that can be started at the boot by configuring the start type value by manually or by some event. Windows has tons of services, malware author utilized the concept of "Hide in Plain Sight". Once the attacker has admin rights he/she can easily create a new service or modify an existing one. Service Replacement: Malware author will find an unused service and replace it with a malicious executable and set it to autostart. Service Recovery Mode: Load a malicious services and an existing service crashes
profitcoin
4/27/2021 04:14:31 pm
FOR RECOVERY OF STOLEN BITCOIN / CRYPTOCURRENCY , RECOVERY OF LOST FUNDS FROM SCAMMER. Have you ever been a victim of a scam? or have you lost your money to fake hackers online? I implore you to contact this trustworthy hacker and recovery expert [email protected] , I was a victim of fake people posing as binary options and bitcoin investors, I lost a sum of $4,000 and 2BTC from my bitcoin wallet to these fakes. It took a while before I realized they were scams and this really hurt .Then an in-law of mine heard about it and recommended to me a specialist with the address - [email protected] . He helped me recover my lost bitcoins in less than 72hrs and the fakes were caught and made to pay for what they did to me .if you have lost any amount to online scams and you're seeking to recover LOST FUNDS from wallet hackers, fake hackers, online dating scams, BTC wallet hack, recovery of lost funds from fake binary investors .Reach out to Wizard Charles Group Hackers to help you Comments are closed.
|
Archives
September 2019
Categories
All
|
 RSS Feed
RSS Feed