|
NTFS was designed to overcome the shortcomings of FAT Filesystem. Some common features are:
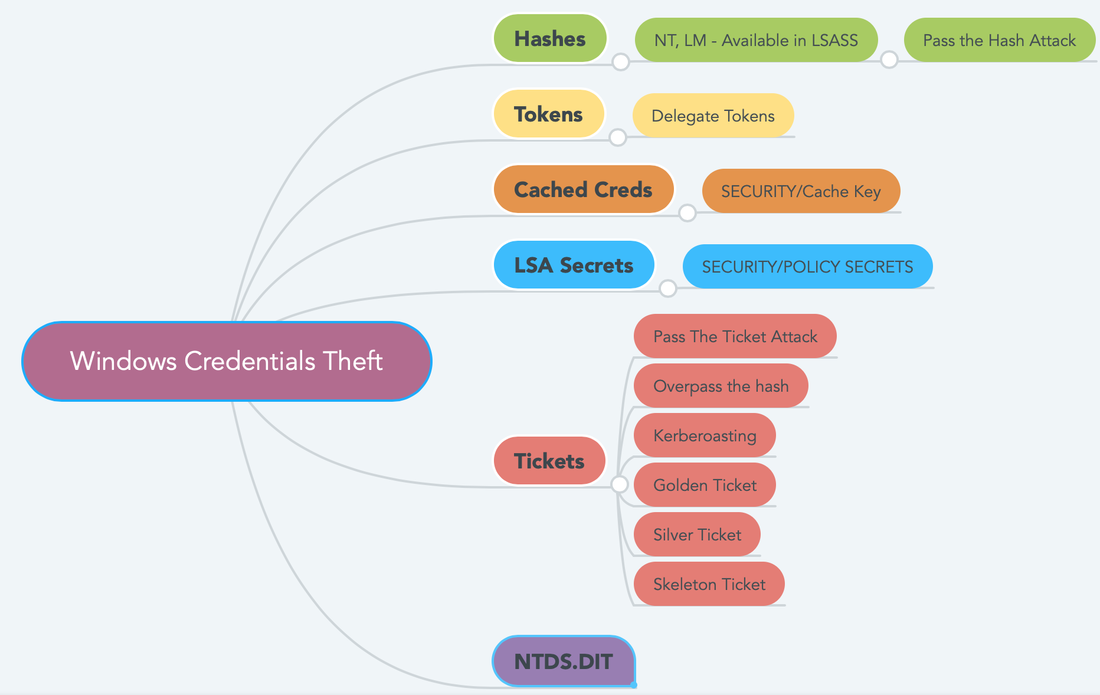
NTFS Transaction Logging / Journling: - NTFS uses a LOG FILE to record changes in the metadata to keep track of state and integrity. This allows to them to understand the system crashes in better way. USN (Update Sequence Number)/Change Journal: - NTFS keep track of all the files that have changed on the system by USN (Update Sequence Number) Journal or Change Journal. This is a great feature for the tools like antivirus scanners or backup tools. They only have to scan/review the changes/updates items and can perform incremental pass over the drive. POSIX:- NTFS Supports hard and soft links. Hard link is a single file respond to multiple name.In soft links the another copy gets created but doesn't have data in it just like an alias. Object ID:- NTFS uses Object ID to track certain files. You can move the files freely, rename it. etc. The distrubuted link tracking system will update all the links to the file and you'll never lose it. File Level Encryption:- It implements file level encryption. Because of this feature you are not able to easily read the files of other uses. Volume Shadow Copy:- NTFS keeps a backup of your files via the Volume Shadow Copy Feature. Alternate Data Stream:- Files in windows can have additional content. For example: Files downloaded from internet can be tagged and windows can give you warning before executing it. We will discuss about Windows Credentials Theft in the blog post. This is the first thing any attacker will do after exploiting to your network. The aim of the attacker will be to gather the credentials for privilege escalation and lateral movement. Companies do not pay much attention to the account and password management and adversaries do take advantage of it. See the mind-map below to understand the top categories.
|
Archives
September 2019
Categories
All
|
 RSS Feed
RSS Feed