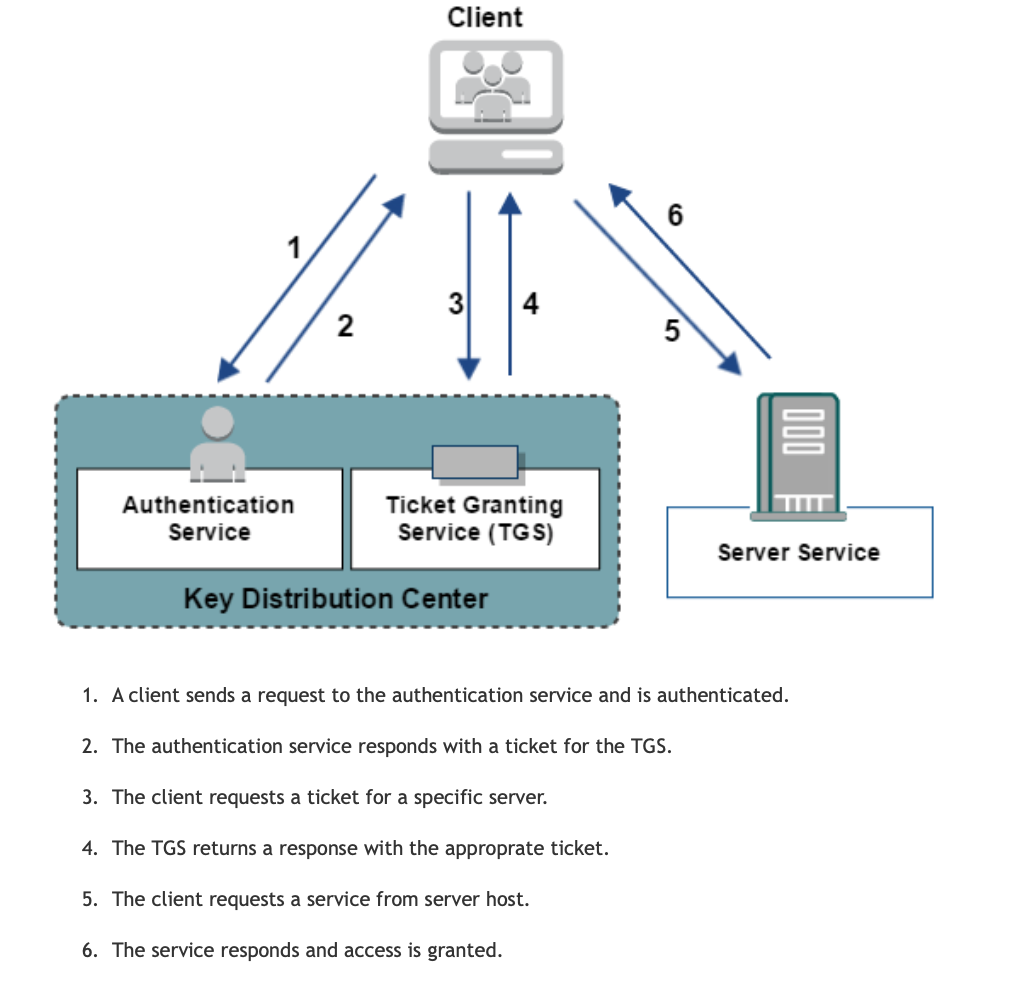
 Kerberos is a network authentication protocol inspired by the greek work for a a three heaed dog Cerberus. Couple of key points to remember about the protocol
Source: https://docops.ca.com/ca-single-sign-on/12-8/en/configuring/policy-server-configuration/authentication-schemes/configure-kerberos-authentication Kerberos Attacks#Pass the ticket:
Ways to investigate Pass the ticket Attack
Countermeasures:
In overpass-the-hash, the attacker will try to capture NTLM hash for the account it wishes to compromise using tools like Mimikatz etc. Using this command in mimikatz: Sekurlsa::pth /user:[USER] /domain:[DOMAIN] /ntlm:[NTLM HASH] The NTML hash was passed into Kerberos authentication provider using RC4 Encryption #Kerberoasting: The focus of this attack is to compromise a service account. It request a ticket for a highly privileged service account. Capture the hash for it and crack it offline. #Golden Ticket: This is generated with a Ticket Granting Ticket for any account with my expiration is generated. Majority of the Active Directory based attacks can be detected by implementing Microsoft Advanced Threat Analytics. https://docs.microsoft.com/en-us/advanced-threat-analytics/what-is-ata |
Archives
September 2019
Categories
All
|
 RSS Feed
RSS Feed