|
Overview:
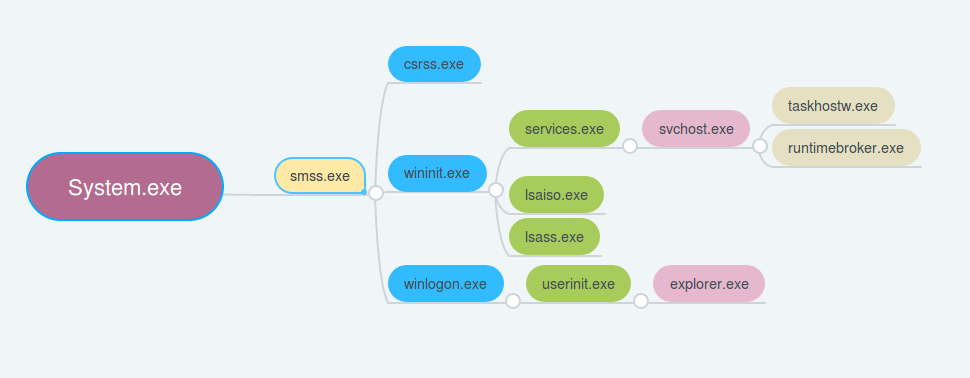
An application consists of one or more processes. A process, in the simplest terms, is an executing program. One or more threads run in the context of the process. A thread is the basic unit to which the operating system allocates processor time. A thread can execute any part of the process code, including parts currently being executed by another thread. Each process provides the resources needed to execute a program. A process has a virtual address space, executable code, open handles to system objects, a security context, a unique process identifier, environment variables, a priority class, minimum and maximum working set sizes, and at least one thread of execution. Each process is started with a single thread, often called the primary thread, but can create additional threads from any of its threads. System
smss.exe
csrss.exe
isaiso.exe
explorer.exe
wininit.exe
lsass.exe
taskhostw.exe
profitcoin
4/27/2021 04:01:42 pm
FOR RECOVERY OF STOLEN BITCOIN / CRYPTOCURRENCY , RECOVERY OF LOST FUNDS FROM SCAMMER. Have you ever been a victim of a scam? or have you lost your money to fake hackers online? I implore you to contact this trustworthy hacker and recovery expert [email protected] , I was a victim of fake people posing as binary options and bitcoin investors, I lost a sum of $4,000 and 2BTC from my bitcoin wallet to these fakes. It took a while before I realized they were scams and this really hurt .Then an in-law of mine heard about it and recommended to me a specialist with the address - [email protected] . He helped me recover my lost bitcoins in less than 72hrs and the fakes were caught and made to pay for what they did to me .if you have lost any amount to online scams and you're seeking to recover LOST FUNDS from wallet hackers, fake hackers, online dating scams, BTC wallet hack, recovery of lost funds from fake binary investors .Reach out to Wizard Charles Group Hackers to help you Comments are closed.
|
Archives
September 2019
Categories
All
|
 RSS Feed
RSS Feed