|
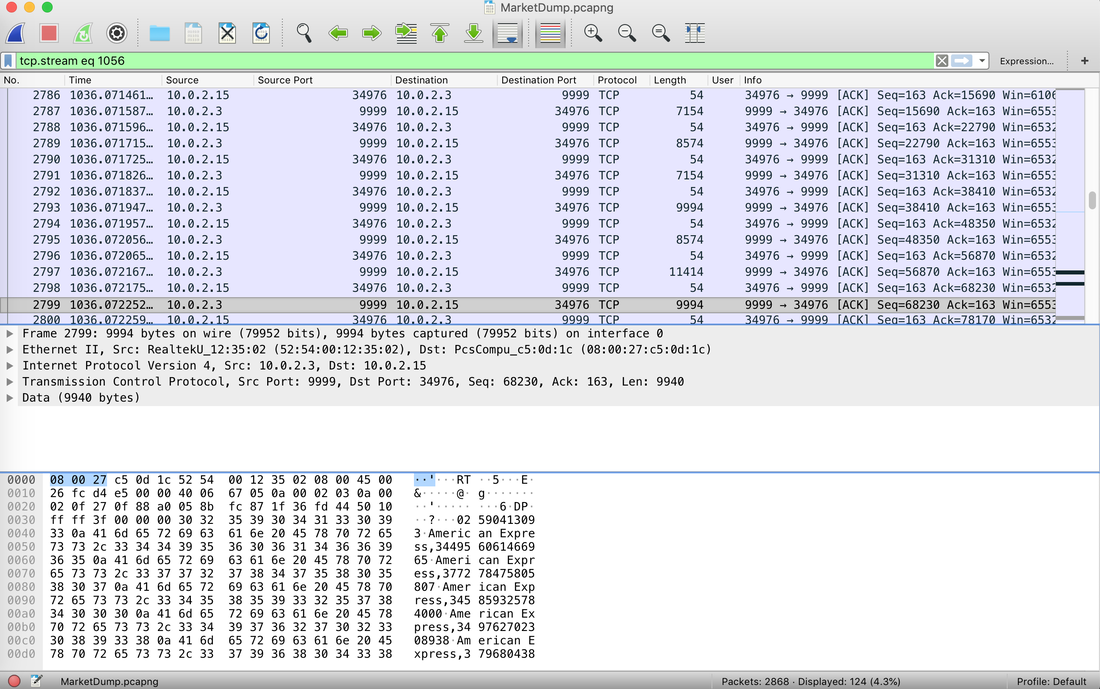
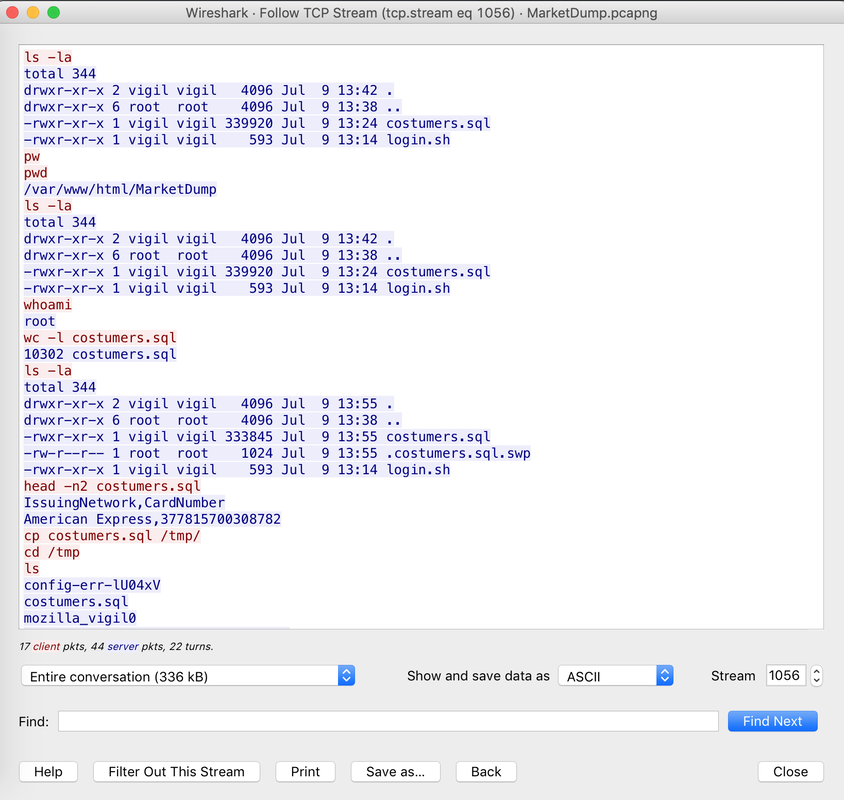
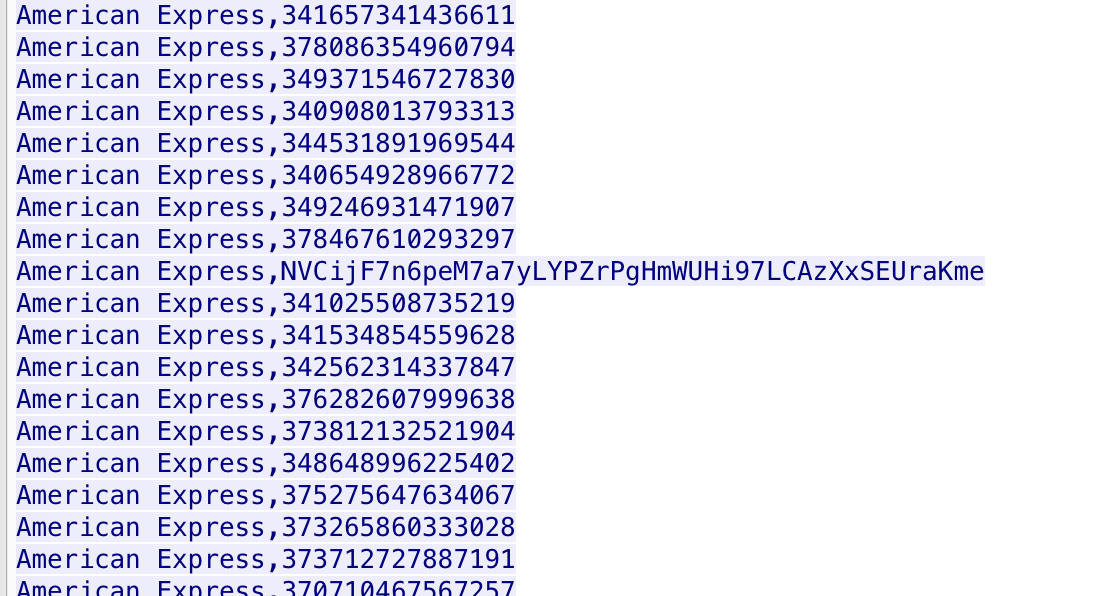
The Forensics CTF Challenge is from Hackthebox.eu. Please see the details of the challenge and download the file from this link: https://www.hackthebox.eu/home/challenges/Forensics We have got informed that a hacker managed to get into our internal network after pivoiting through the web platform that runs in public internet. He managed to bypass our small product stocks logging platform and then he got our costumer database file. We believe that only one of our costumers was targeted. Can you find out who the customer was? They have provided a pcap file for the analysis. For the analysis you need to follow the TCP Stream. Once you start following in TCP Stream, you'll find the exfiltration information in the 1056 Stream. Scroll down and review the content, it's fairly easy to notice the encoded flag in the data. Use CyberChef Magic Recipe to decode the flag. 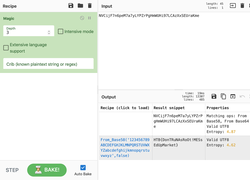 #Injection:
Websites and apps occasionally need to run commands on the underlying databases or operating system to add or delete data, execute a script, or start other apps. If unverified inputs are added to a commands string or a database command, attackers can launch commands at will to take control of a server, device or data. How does it work? If a website, app or device incorporates user input within a command, an attacker can insert a "payload" command directly into said input. If that input is not verified, an attacker then "injects" and runs their own commands. Why it's bad? Once attacker can make commands, they can control your website, apps and data. Example: SQL Injection was used in SONY Hack in 2014. The attackers used Server Message Block Worm tool to install several malicious components, including a backdoor and other tools. The SMB Worm Tool was equipped with five components, including a Listening Implant, Lightweight Backdoor, Proxy Tool, Destructive Hard Drive Tool, and Destructive Target Cleaning Tool. The worm moves throughout an infected network through brute-force authentication attacks on windows SMB Share and connects to a command and control (C2) infrastructure with servers located in Thailand, Poland, Italy, Bolivia, Singapore, and the United States |
Mac Forensics
|
 RSS Feed
RSS Feed