|
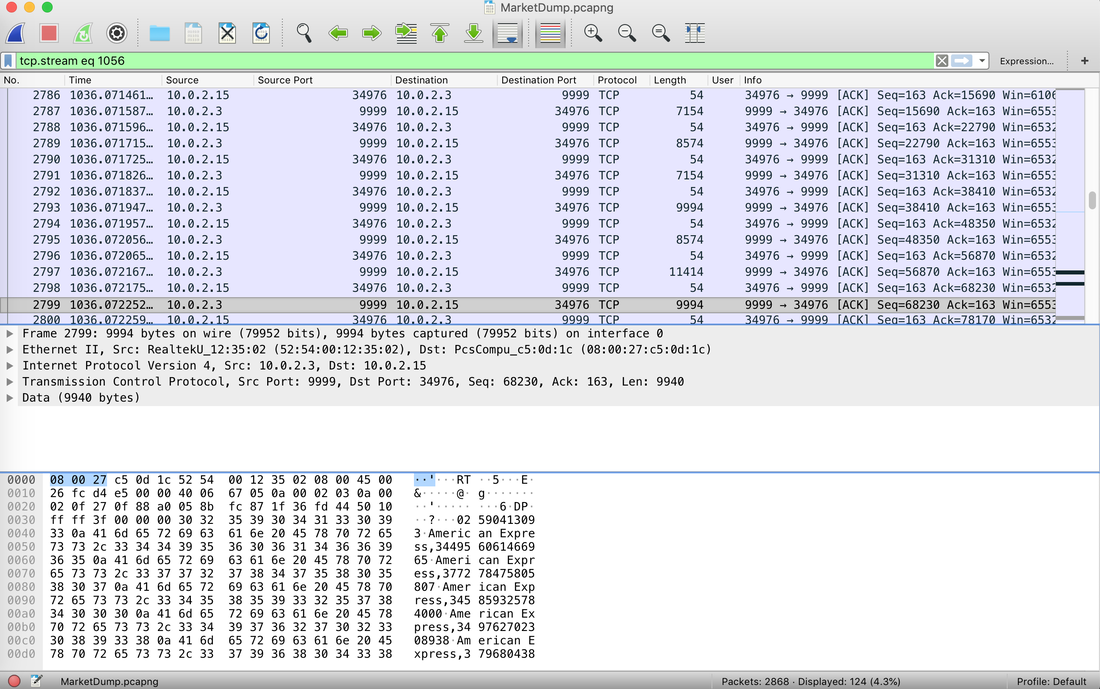
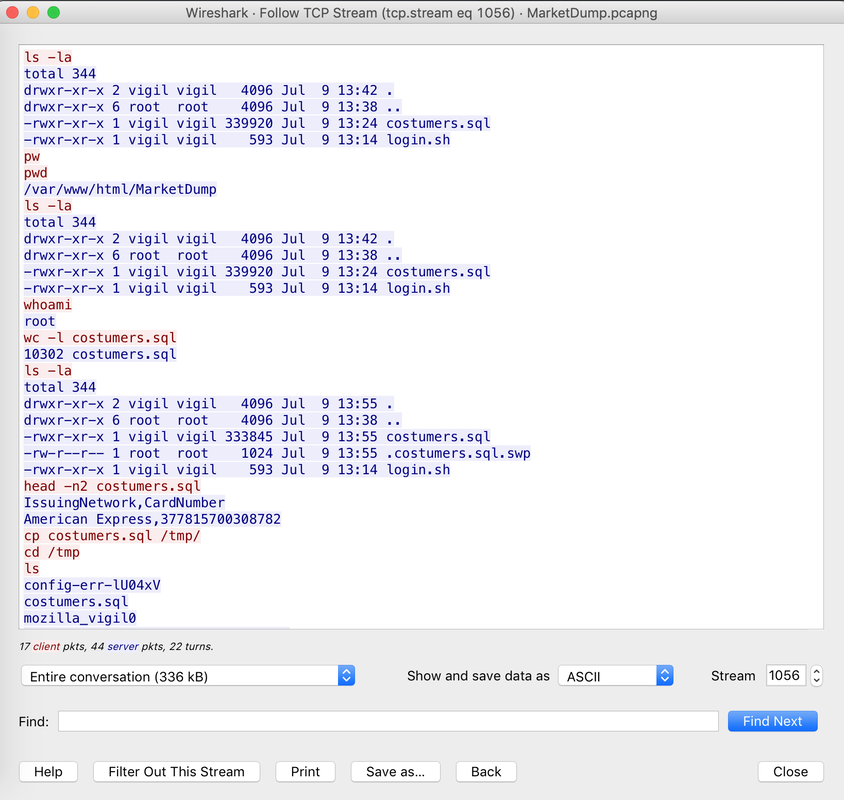
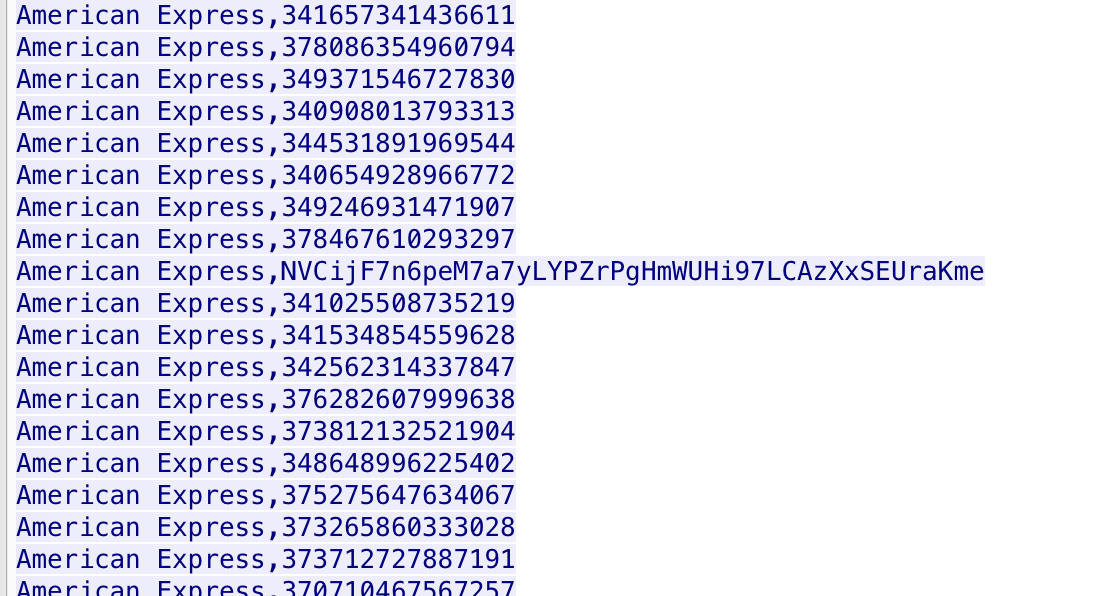
The Forensics CTF Challenge is from Hackthebox.eu. Please see the details of the challenge and download the file from this link: https://www.hackthebox.eu/home/challenges/Forensics We have got informed that a hacker managed to get into our internal network after pivoiting through the web platform that runs in public internet. He managed to bypass our small product stocks logging platform and then he got our costumer database file. We believe that only one of our costumers was targeted. Can you find out who the customer was? They have provided a pcap file for the analysis. For the analysis you need to follow the TCP Stream. Once you start following in TCP Stream, you'll find the exfiltration information in the 1056 Stream. Scroll down and review the content, it's fairly easy to notice the encoded flag in the data. Use CyberChef Magic Recipe to decode the flag. 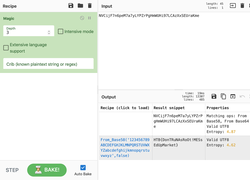 Comments are closed.
|
Mac Forensics
|
 RSS Feed
RSS Feed